Emergency Directive 21-01
On December 13th 2020, in response to an advanced supply-chain attack [0] against SolarWinds Orion, the Cyber and Infrastructure Security Agency (CISA) of the U.S. Department of Homeland Security (DHS) released Emergency Directive 21-01, “Mitigate SolarWinds Orion Code Compromise”. [1] In this Query Corner, we discuss how Orbital Advanced Search can help with the actions listed in the CISA Directive.
Required action 1 a reads as follows:
Forensically image system memory and/or host operating systems hosting all instances of SolarWinds Orion versions 2019.4 through 2020.2.1 HF1]. Analyze for new user or service accounts, privileged or otherwise.
Let’s break this down a bit. The first step, of course, is to identify systems running SolarWinds Orion. Presumably, an organization would be aware of where it had installed important network management tools; but are you sure your list is complete? Does it include other groups that might have procured a tool for their own use, or even just an evaluation or proof-of-concept? Fortunately, we don’t have to guess, because Orbital makes it easy to inventory installed software assets. In the Query Catalog, the query titled “Installed Programs On Windows Host” is exactly what we’re looking for.
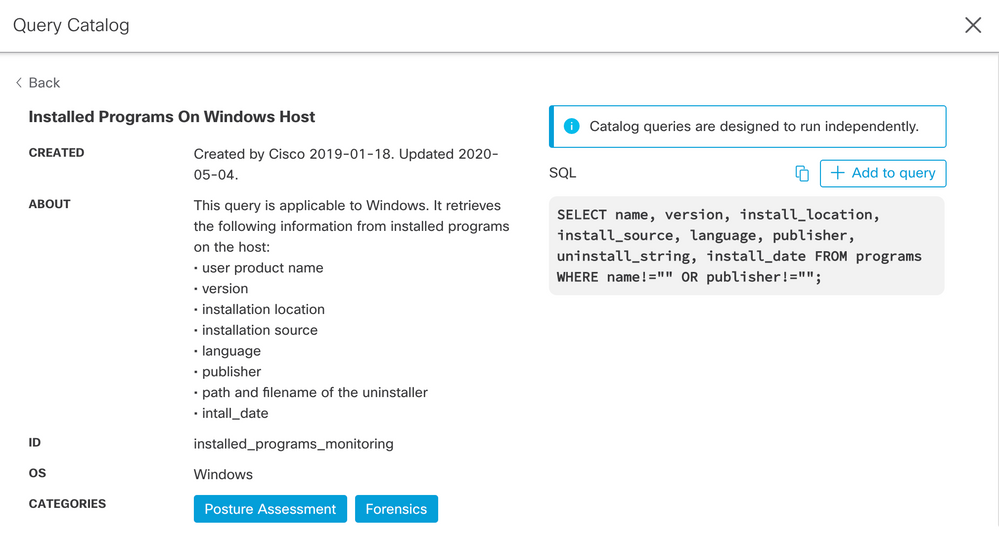
As you can see, this query gives us a lot of detail about the installed software on the targeted hosts. In particular, note that it includes the installed version in the report, so we can quickly identify any hosts running the affected versions, as specified in the CISA Directive.
Narrowing the Focus
We can also use the catalog query as the starting point for a more focused search, by adding a condition. There is a handly little button in the query catalog window to copy the query so we can modify it:
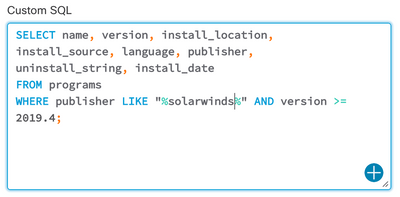
Then we can paste the copied text into the custom query window and modify it. We'll look only for a specific publisher and the range of versions identified as affected (starting with 2019.4 according to the advisory).
Looking for New Accounts
Now that we have identified potentially affected systems, we can run a new query on those endpoints, as specified in the CISA Directive, to list user and service accounts, looking for any suspicious modifications. Again, there is a prebuilt query in the catalog to get us started.
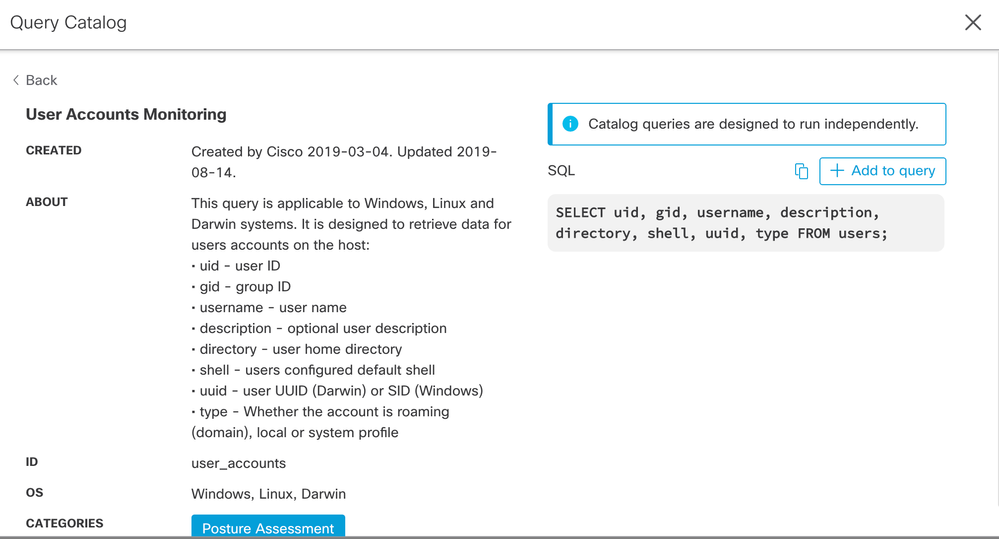
And here are the results of a query on a Windows 10 test system. Notice that, despite the name, a "users" query returns both user and virtual service accounts.
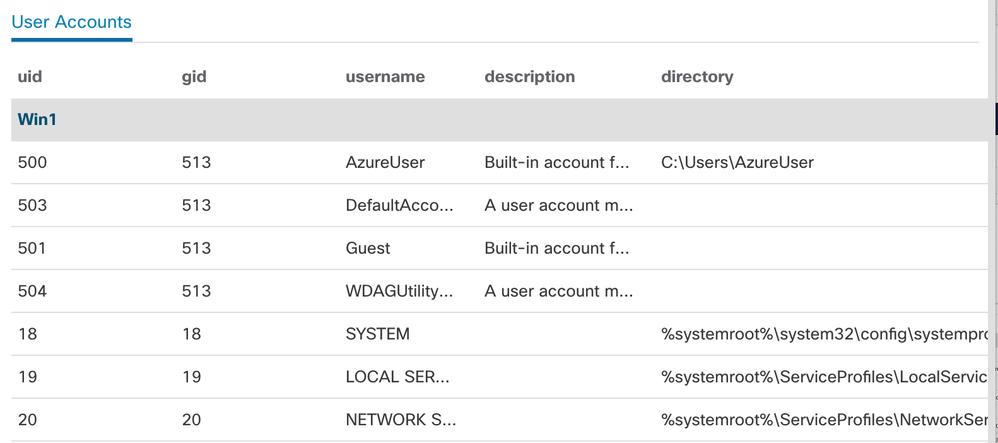
So, with a few minutes of work in the Orbital Query catalog, we were able to quickly identify any systems that might be affected by the Emergency Directive, and conduct the required audit of accounts present on those systems. No memory dump required!
For another Orbital angle on the Solarwinds Orion issue, check out Jason Maynard's Orbital Threat Hunting video on YouTube. [2] Cisco is tracking this issue on a Security Event Response page [3].
[0] https://blog.talosintelligence.com/2020/12/solarwinds-supplychain-coverage.html
[1] https://cyber.dhs.gov/ed/21-01/
[2] https://youtu.be/hr1WWfrw51o
[3] https://tools.cisco.com/security/center/resources/solarwinds_orion_event_response