- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Router Security - App Aware Zone Based Firewall Step-by-Step Config
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-27-2022 02:42 PM - edited 05-28-2022 10:13 AM
- Benefits
- Documentation
- Prerequisite
- Image Download Links
- Supported Platforms
- Limitations
- License Requirements
- Topology
- Step-by-step Configuration
- Configure PAT
- Create Custom Zones
- Create Class Map
- Create the Policy-map
- Create Zone Pair
- Assign the Interfaces to the Zones
- Relevant Configuration
- Verification
- Make sure NAT is working
- Make sure FW is working
- Optional App Ware FW Configuration
- Requirement
- Fixing the existing FW Class-map
- Create a separate class-map for AVC
- Create a policy-map for AVC
- Incorporate this AVC policy into the FW policy-map
- Verify Application Aware FW
- Check policy-map
- Check FW drop
- Check for syslogs
Benefits
- Helps meet PCI compliance.
- Threat protection built into Catalyst 8000 Family, ISR and ISRv branch routers and CSR
- Integrated on-prem Security
- Supports VRF
- Supports IPv6
Documentation
This configuration example is meant to be interpreted with the aid of the official documentation from the configuration guide located here:
Prerequisite
XE 3.9 and above on ISR 4K
XE 16.6.1 and above on ISR 1K
XE 16.6.1 and above on ISRv
XE 3.7S and above on ASR1K
XE 3.10S and above on CSR 1000V
XE 17.3.2 and above for C8300
XE 17.4.1 and above for C8200 and 8000V
Image Download Links
Catalyst 8500 - https://software.cisco.com/download/home/286323412/type
Catalyst 8300 - https://software.cisco.com/download/home/286324476/type
Catalyst 8200 - https://software.cisco.com/download/home/286324472/type
Catalyst 8000V - https://software.cisco.com/download/home/286327102/type
ISR - https://software.cisco.com/download/home/284389362/type
CSR - https://software.cisco.com/download/home/284364978/type
ISRv - https://software.cisco.com/download/home/286308693/type
Supported Platforms
ISR 4K, CSR, ISRv, ISR 1K
Catalyst 8500, 8300, 8200, 8000V.
Limitations
1. AppAware FW does not support traffic to self-zone
2. AVC policy should allow all and only deny certain application. Allowing certain and denying all is not guaranteed to work since many applications are dependent on each other, allowing one application while denying all others might not work all the time.
3. Once "match protocol attribute category <category name>" is specified, "match protocol attribute application-family" or "match protocol application-group" cannot be configured (and vice versa).
License Requirements
Security K9 license is required on the ISR1K, ISR 4K routers, CSRs and ISRv.
DNA-Essentials license is required on the Catalyst 8000 Edge routers mentioned in the Supported Platforms section in order to be able to configure Zone Based Firewall.
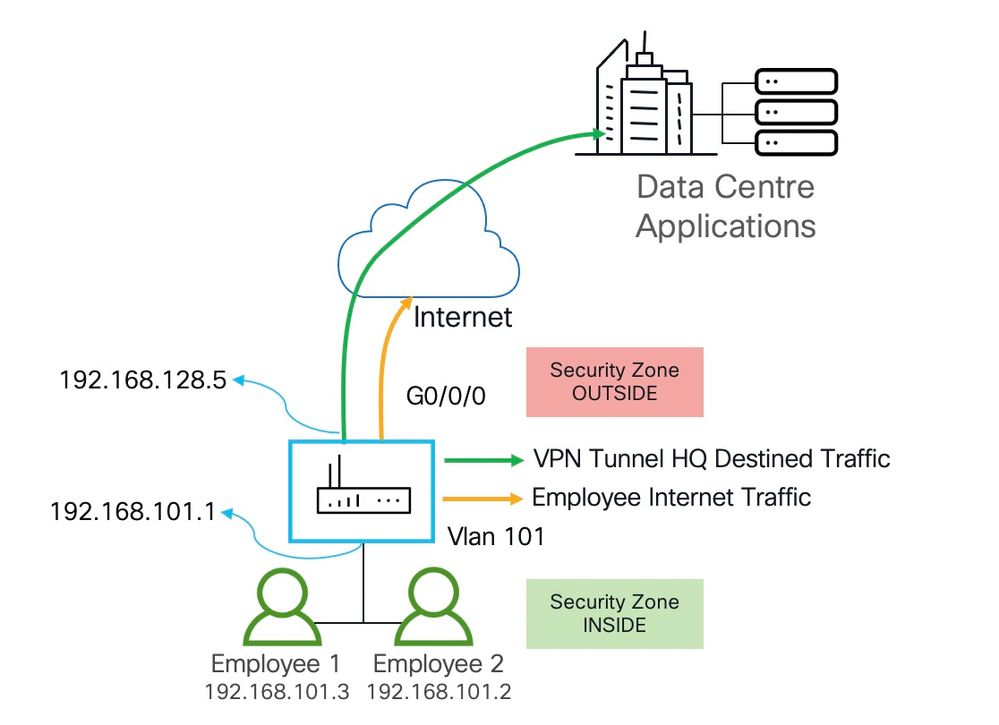
Topology
In this topology don't get confused with the fact both inside and outside interfaces using RFC 1918 addresses. This router (ISR 1121X) is sitting behind the home internet router that is not shown in the image.
Step-by-step Configuration
Configure PAT
Since this router is interface facing, we need to configure NAT, actually PAT so all the inside hosts look like the outside interface IP address when they go out to the internet.
ip access-list extended IN-OUT
permit ip 192.168.101.0 0.0.0.255 any
ip nat inside source list IN-OUT interface GigabitEthernet0/0/0 overload
interface vlan101
ip nat inside
interface g0/0/0
ip nat outside
Create Custom Zones
Create the custom zones. In this case we will create two zones INSIDE and OUTSIDE to allow traffic from the high security inside to the low security outside.
zone security INSIDE zone security OUTSIDE
Create Class Map
Create class-map and identify the protocols that needs to be allowed from the inside to the outside.
class-map type inspect match-any INSIDE-TO-OUTSIDE-CLASS match protocol ftp match protocol tcp match protocol udp match protocol icmp
Notice we added "ftp" above "tcp", this is important because if you added "ftp" below "tcp" then ftp traffic will match the "tcp rule and these packets will not be inspected for ftp. Meaning depending on active or passive ftp and whether the ftp server is on the inside or outside, ftp traffic might not work.
Create the Policy-map
Next create a policy-map and call the class-map that you configure in the above step. This is required to ensure we configure an action for the identified traffic. These actions are:
inspect - where by the response traffic will be automatically allowed
pass - one way the traffic will be allowed but for the response traffic to come back, we need to configure another "pass" action from the OUTSIDE to INSIDE
policy-map type inspect INSIDE-TO-OUTSIDE-POLICY class type inspect INSIDE-TO-OUTSIDE-CLASS inspect class class-default drop
Any traffic that is not allowed in the class-map INSIDE-TO-OUTSIDE-CLASS will be automatically dropped.
Create Zone Pair
Next, we create a zone pair to indicate the direction of traffic initiation. In our case this is outbound traffic. Traffic is initiated from the inside destined to the outside. This step is to apply the policy-map to the outbound traffic.
zone-pair security IN_OUT source INSIDE destination OUTSIDE service-policy type inspect INSIDE-TO-OUTSIDE-POLICY
Assign the Interfaces to the Zones
interface g0/0/0 zone sec OUTSIDE interface vlan101 zone sec INSIDE
Relevant Configuration
interface GigabitEthernet0/0/0 ip address dhcp ip nat outside zone-member security OUTSIDE ! interface Vlan101 ip address 192.168.101.1 255.255.255.0 ip nat inside zone-member security INSIDE ! interface GigabitEthernet0/1/0 switchport access vlan 101 ===> Employee 1 is connected switchport mode access ! class-map type inspect match-any INSIDE-TO-OUTSIDE-CLASS match protocol ftp match protocol tcp match protocol udp match protocol icmp ! policy-map type inspect INSIDE-TO-OUTSIDE-POLICY class type inspect INSIDE-TO-OUTSIDE-CLASS inspect class class-default drop ! ! zone security INSIDE zone security OUTSIDE zone-pair security IN_OUT source INSIDE destination OUTSIDE service-policy type inspect INSIDE-TO-OUTSIDE-POLICY ! ip nat inside source list IN-OUT interface GigabitEthernet0/0/0 overload ! ip access-list extended IN-OUT 10 permit ip 192.168.101.0 0.0.0.255 any
Verification
Make sure NAT is working
Let us first verify whether NAT is working. The below output looks good. Both DNS as well as HTTPS connections have been established from the employee host 192.168.101.2 to the internet.
kusankar-1121X#show ip nat translations Pro Inside global Inside local Outside local Outside global udp 192.168.128.5:5698 192.168.101.2:50837 4.2.2.2:53 4.2.2.2:53 =====> DNS udp 192.168.128.5:5700 192.168.101.2:64528 4.2.2.2:53 4.2.2.2:53 udp 192.168.128.5:5704 192.168.101.2:64248 4.2.2.2:53 4.2.2.2:53 tcp 192.168.128.5:5573 192.168.101.2:55538 172.16.1.1:443 172.16.1.1:443 udp 192.168.128.5:5707 192.168.101.2:56965 4.2.2.2:53 4.2.2.2:53 tcp 192.168.128.5:5569 192.168.101.2:55534 172.16.1.1:443 172.16.1.1:443 tcp 192.168.128.5:5568 192.168.101.2:55539 172.16.1.1:443 172.16.1.1:443 tcp 192.168.128.5:5524 192.168.101.2:55381 146.75.37.67:443 146.75.37.67:443 udp 192.168.128.5:5703 192.168.101.2:55918 4.2.2.2:53 4.2.2.2:53 udp 192.168.128.5:5699 192.168.101.2:61675 4.2.2.2:53 4.2.2.2:53 udp 192.168.128.5:5705 192.168.101.2:50079 4.2.2.2:53 4.2.2.2:53 tcp 192.168.128.5:5570 192.168.101.2:55535 172.16.1.1:443 172.16.1.1:443 icmp 192.168.128.5:2 192.168.101.2:3 142.251.45.110:3 142.251.45.110:2 icmp 192.168.128.5:3 192.168.101.2:3 192.168.1.1:3 192.168.1.1:3 udp 192.168.128.5:5702 192.168.101.2:62893 4.2.2.2:53 4.2.2.2:53 udp 192.168.128.5:5701 192.168.101.2:55939 4.2.2.2:53 4.2.2.2:53 udp 192.168.128.5:5697 192.168.101.2:62200 4.2.2.2:53 4.2.2.2:53 udp 192.168.128.5:5706 192.168.101.2:60987 4.2.2.2:53 4.2.2.2:53 udp 192.168.128.5:5696 192.168.101.2:51506 4.2.2.2:53 4.2.2.2:53 tcp 192.168.128.5:5571 192.168.101.2:55536 172.16.1.1:443 172.16.1.1:443 ======> HTTPS tcp 192.168.128.5:5574 192.168.101.2:55533 172.16.1.1:443 172.16.1.1:443 tcp 192.168.128.5:5592 192.168.101.2:55420 99.83.161.114:443 99.83.161.114:443 tcp 192.168.128.5:5572 192.168.101.2:55537 52.44.84.180:443 52.44.84.180:443 Total number of translations: 23
Make sure FW is working
kusankar-1121X#show policy-map type inspect zone-pair sessions
Zone-pair: IN_OUT
Service-policy inspect : INSIDE-TO-OUTSIDE-POLICY
Class-map: INSIDE-TO-OUTSIDE-CLASS (match-any)
Match: protocol ftp
Match: protocol tcp
Match: protocol udp
Match: protocol icmp
Inspect
Established Sessions
Session ID 0x00004D57 (192.168.101.2:56252)=>(4.2.2.2:53) udp SIS_OPEN
Created 00:00:48, Last heard 00:00:48
Bytes sent (initiator:responder) [34:66]
Session ID 0x00004B86 (192.168.101.2:55420)=>(99.83.161.114:443) tcp SIS_OPEN
Created 03:47:29, Last heard 00:00:48
Bytes sent (initiator:responder) [596644:20676]
Session ID 0x00004D58 (192.168.101.2:62572)=>(4.2.2.2:53) udp SIS_OPEN
Created 00:00:48, Last heard 00:00:48
Bytes sent (initiator:responder) [34:66]
Session ID 0x00000000 (192.168.101.2:8)=>(192.168.1.1:3) icmp SIS_OPEN
Created 88:57:38, Last heard 00:01:18
Bytes sent (initiator:responder) [81952:81952]
Session ID 0x00004A90 (192.168.101.2:55381)=>(146.75.37.67:443) tcp SIS_OPEN
Created 03:49:19, Last heard 00:01:57
Bytes sent (initiator:responder) [3908:471953]
Session ID 0x00000001 (192.168.101.2:8)=>(142.251.45.110:3) icmp SIS_OPEN
Created 88:57:24, Last heard 00:00:03
Bytes sent (initiator:responder) [767360:767360]
Half-open Sessions
Session ID 0x00004D55 (192.168.101.2:55549)=>(172.16.1.1:443) tcp SIS_OPENING
Created 00:05:36, Last heard 00:03:36
Bytes sent (initiator:responder) [0:0]
Session ID 0x00004D56 (192.168.101.2:55550)=>(172.16.1.1:443) tcp SIS_OPENING
Created 00:01:49, Last heard 00:01:09
Bytes sent (initiator:responder) [0:0]
Class-map: class-default (match-any)
Match: any
Drop
0 packets, 0 bytes
This completes FW configuration. Let us now look at incorporating option application awareness to the FW configuration.
Optional App Ware FW Configuration
Requirement
1. Make sure the router has AppX license. The match protocol CLI is available without the appkx9 license. Users will be able to configure everything without the AppX license enabled. But, without the AppX license, NBAR will not work and the application traffic will not be detected.
Install license. In this example we are just installing the traditional license. Once done write mem and reload
kusankar-1121X(config)#license boot level securityk9 % use 'write' command to make license boot config take effect on next boot kusankar-1121X(config)#license boot level appxk9 % use 'write' command to make license boot config take effect on next boot
Once the router comes back up make sure to verify that the license is installed.
kusankar-1121X#show license summary Account Information: Smart Account: <none> Virtual Account: <none> License Usage: License Entitlement Tag Count Status ----------------------------------------------------------------------------- appxk9 (ISR_1100_8P_Application) 1 IN USE securityk9 (ISR_1100_8P_Security) 1 IN USE
2. nbar protocol pack comes with the router image and it is enabled by default. You can verify that with the following command.
kusankar-1121X#show ip nbar protocol-pack active Active Protocol Pack: Name: Advanced Protocol Pack Version: 60.0 ===================> This is the version of the protocol Pack Publisher: Cisco Systems Inc. NBAR Engine Version: 45 State: Active
You can verify the latest protocol pack using the "Image Download Link" referred above.
Also refer: NBAR Protocol Pack
Fixing the existing FW Class-map
We need to modify the existing class-map that we configured up above. The reason is that dns inspection is mandatory for NBAR to work and it is to be called out in the same class-map where the AVC service-policy is applied.
class-map type inspect match-any INSIDE-TO-OUTSIDE-CLASS match protocol ftp no match protocol tcp ====> removing them and adding after adding specific protocols no match protocol udp no match protocol icmp match protocol http match protocol dns ===> adding more specific dns before adding udp inspection match protocol tcp match protocol udp match protocol icmp
Create a separate class-map for AVC
Create a class-map for applications that we need to block. AVC is Application Visibility and Control.
class-map match-any AVC-CLASS match protocol yahoo match protocol amazon match protocol attribute category consumer-streaming match protocol attribute category gaming match protocol attribute category social-networking
Create a policy-map for AVC
Now create a policy-map so we can call the AVC-CLASS class-map that we just created above. We will "deny" the apps that we called out in the AVC-CLASS and allow everything else.
policy-map type inspect avc AVC-POLICY class AVC-CLASS deny class class-default allow
Incorporate this AVC policy into the FW policy-map
Now, it is time to include this AVC policy into the previously configured FW policy - under the policy-map section.
policy-map type inspect INSIDE-TO-OUTSIDE-POLICY class type inspect INSIDE-TO-OUTSIDE-CLASS inspect service-policy avc AVC-POLICY ========> This is the new additional line to the existing policy-map class class-default drop
Verify Application Aware FW
Check policy-map
Browse from a host behind the router to amazon.com, facebook.com and other applications that we blocked / denied in the AVC policy. Check if the AVC policy is seeing traffic.
kusankar-1121X#sh policy-map type inspect zone-pair sessions
Zone-pair: IN_OUT
Service-policy inspect : INSIDE-TO-OUTSIDE-POLICY
Class-map: INSIDE-TO-OUTSIDE-CLASS (match-any)
Match: protocol ftp
Match: protocol http
Match: protocol dns
Match: protocol tcp
Match: protocol udp
Match: protocol icmp
Inspect
Established Sessions
Session ID 0x00001580 (192.168.102.4:64730)=>(4.2.2.2:53) dns SIS_OPEN
Created 00:00:29, Last heard 00:00:29
Bytes sent (initiator:responder) [31:210]
.
.
Session ID 0x0000156D (192.168.102.4:63219)=>(170.72.231.0:443) tcp SIS_OPEN
Created 00:04:29, Last heard 00:04:28
Bytes sent (initiator:responder) [4616:7862]
Half-open Sessions
Session ID 0x00001577 (192.168.101.2:49191)=>(172.16.1.1:443) tcp SIS_OPENING
Created 00:01:58, Last heard 00:01:18
Bytes sent (initiator:responder) [0:0]
Session ID 0x00001562 (192.168.102.4:63214)=>(80.254.145.118:80) http SIS_OPENING
Created 00:09:57, Last heard 00:02:08
Bytes sent (initiator:responder) [0:0]
Service-policy inspect avc : AVC-POLICY
Class-map: AVC-CLASS (match-any)
1042 packets, 329027 bytes
30 second offered rate 0000 bps, drop rate 0000 bps
Match: protocol yahoo
Match: protocol amazon
Match: protocol attribute category consumer-streaming
Match: protocol attribute category gaming
Match: protocol attribute category social-networking
Deny
Class-map: class-default (match-any)
645784 packets, 519767221 bytes
30 second offered rate 60000 bps, drop rate 0000 bps
Match: any
Allow
Class-map: class-default (match-any)
Match: any
Drop
0 packets, 0 bytes
Check FW drop
kusankar-1121X#show platform hardware qfp active feature firewall drop ------------------------------------------------------------------------------- Drop Reason Packets ------------------------------------------------------------------------------- Invalid TCP initiator 26 Retrans with invalid flags 150 SYN inside current window 1 RST inside current window 86 Stray Segment 1150 ICMP ERR Pkt:exceed burst lmt 5 ICMP Unreach pkt exceeds lmt 439 AVC Policy drop:classify result 1042 ==> New Drop Counter No Zone-pair found 44
Check for syslogs
In order to see the logs generated for dropped packets we need to enable "log dropped-packets". Once you enable with the following command globally, try the blocked websites again and check the logs by issues show logs.
parameter-map type inspect-global log dropped-packets
kusankar-1121X#show logg | i AVC
*May 28 16:05:59.435: %IOSXE-6-PLATFORM: R0/0: cpp_cp: QFP:0.0 Thread:000 TS:00000001523546478400 %FW-6-DROP_PKT: Dropping dns/amazon pkt from Vlan102 192.168.102.4:59833 => 4.2.2.2:53(target:class)-(IN_OUT:INSIDE-TO-OUTSIDE-CLASS) due to AVC Policy drop:classify result with ip ident 49937 *May 28 16:21:51.275: %IOSXE-6-PLATFORM: R0/0: cpp_cp: QFP:0.0 Thread:000 TS:00000002475387069240 %FW-6-DROP_PKT: Dropping dns/facebook pkt from Vlan102 192.168.102.4:53596 => 4.2.2.2:53(target:class)-(IN_OUT:INSIDE-TO-OUTSIDE-CLASS) due to AVC Policy drop:classify result with ip ident 21824 *May 28 16:23:02.190: %IOSXE-6-PLATFORM: R0/0: cpp_cp: QFP:0.0 Thread:000 TS:00000002546301506680 %FW-6-DROP_PKT: Dropping dns/youtube pkt from Vlan102 192.168.102.4:54670 => 4.2.2.2:53(target:class)-(IN_OUT:INSIDE-TO-OUTSIDE-CLASS) due to AVC Policy drop:classify result with ip ident 65389 *May 28 16:16:18.743: %IOSXE-6-PLATFORM: R0/0: cpp_cp: QFP:0.0 Thread:000 TS:00000002142855257640 %FW-6-DROP_PKT: Dropping dns/itunes-audio pkt from Vlan102 192.168.102.4:63516 => 4.2.2.2:53(target:class)-(IN_OUT:INSIDE-TO-OUTSIDE-CLASS) due to AVC Policy drop:classify result with ip ident 31087
Hope you found this document useful. Please provide your feedback below.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hello, thanks.... :):):)
Please can you explain again but with NAT portforwarding ( static nat) please
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: