- Cisco Community
- Technology and Support
- Service Providers
- Service Providers Knowledge Base
- ASR9000/XR Flexible VLAN matching, EVC, VLAN-Tag rewriting, IRB/BVI and defining L2 services
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-07-2011 07:18 AM
Introduction
In this article we'll be discussing the EVC (Ethernet Virtual Circuit) infrastructure that the ASR9000 and IOS-XR use to define L2 services.
You'll find in this article how packets coming in on an interface are being matched against an EFP (Ethernet Flow Point), how to manipulate the vlan tags and use them in XCONNECT (VPWS) or Bridging (eg VPLS) scenarios with the optional L3 endpoint to provide IRB (Integrated Route Bridging)
Core Issue
The way that IOS-XR handles EVC's is a bit different then the way that IOS handles it when for instance using the 7600.
When starting with IOS-XR and the ASR9000 there are a few things that you will want to be aware of when defining L2 services.
A couple of the key differences are:
- XR does have the concept of a trunk interface
- therefore XR cannot do vlan pruning
- XR does not strip vlan tags by default.
- XR does not have the concept of an "interface VLAN" a.k.a. SVI's (Switch Virtual Interface), instead it uses a BVI (Bridge Virtual Interface) that can be inserted into the bridge-domain.
Flexible VLAN matching
How the ASR9000 matches traffic to an EFP
TAG rewriting
how to modify the vlan headers and how that works
Defining L2 services
and a comparison with IOS
Providing L3 services in L2VPN
using IRB/BVI interfaces
Resolution
In order to define an L2 service, we need to match traffic to a particular interface. In IOS-XR and the ASR9000 we use the Ethernet Flow Point (EFP) to match this traffic. An EFP is effectively a subinterface of a physical interface with the keyword "l2transport" attached to it. This l2transport defines that we are going to use this (sub) interface for L2 Services. We can match L2 and L3 interfaces on a single physical port:
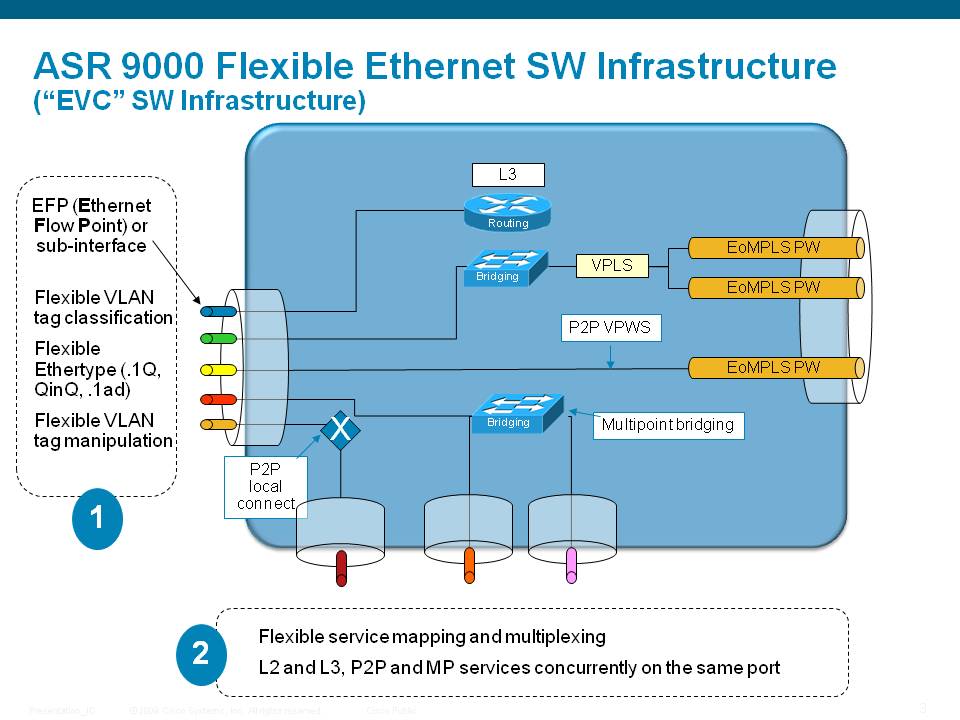
Flexible VLAN matching
When traffic is coming in on a port, we use the TCAM to find out which particular subinterface this traffic matches on. With that in mind there are a couple of rules as to how traffic is matched.
An EFP is defined as follows:
RP/0/RSP0/CPU0:asr(config)#int gig 0/0/0/4.100 l2transport
RP/0/RSP0/CPU0:asr(config-subif)#encapsulation ?
default Packets unmatched by other service instances
If a particular packet is not matching any other specific EFP on this physical port, this "Default" will capture all unmatched traffic.
dot1ad IEEE 802.1ad VLAN-tagged packets
dot1q IEEE 802.1Q VLAN-tagged packets
untagged Packets with no explicit VLAN tag
If there is no vlan tag on the packet, the "untagged" EFP will capture this traffic, this is effectively plain ethernet and useful for instance to capture
BPDU's for instance.
When we are going to match on say dot1q encapsulated traffic we have a variaty of how we can match vlan tagged traffic (see also foot note below in the "Related Information" section on the ethertypes used).
RP/0/RSP1/CPU0:A9K-BOTTOM(config-subif)#encapsulation dot1q ?
<1-4094> Start of VLAN range
<1-4094> Single VLAN id
any Match any VLAN id
priority-tagged IEEE 802.1ad priority-tagged packets
At the first level of dot1q classification we can select a vlan, vlan-range or any. These are obvious. The option "Priority tagged" allows us to capture vlan encapped traffic that is with a vlan id of 0.
RP/0/RSP1/CPU0:A9K-BOTTOM(config-subif)#encapsulation dot1q 100 ?
comma comma
exact Do not allow further inner tags
ingress Perform MAC-based matching
second-dot1q IEEE 802.1Q VLAN-tagged packets
Here is an important concept that is to be highlighted. You see the "word" exact" here. What that means is, in the absence of the keyword exact, if the outter vlan header is "100" in this example, this EFP is matched. so that means that also qinq frames that are of the 100 outter and 200 inner kind (if there is no specific EFP for the qiq combo 100/200 available) will match this EFP.
Just a few examples:
encapsulation dot1q 100: will match any number of vlan headers as long as the outter vlan id is 100
encapsulation dot1q 100 second any: will match any qiq frame where the outter vlan is 100
encapsulation dot1q 100 second 200: will match vlan tagged packets whereby the outter is 100, the inner is 200 and also a potential vlan combo of 100/200/300
encapsulation dot1q 100 second 200 exact: will match vlan tagged packets whereby the outter is 100, the inner is 200 and no other vlan tags are on the packet then these 2 specified.
Normally "longest match" will win, or better put, the most specific match will win.
ASR9000 doesn't support best match for VLAN ranges, but we do support best match if the "any" keyword is used.
So the configuration :
EFP 1 VLAN: S-VLAN=1000, C-VLAN_range=1-4095
EFP 2 VLAN= S-VLAN=1000, C-VLAN=2000
isn't allowed because the more specific C-vlan is part of the range. The parser will reject this config upon commit.
The following options A and B, achieving the same, are allowed :
A)
EFP 1) VLAN: S-VLAN=1000, C-VLAN_range=1-1999,2001-4095
EFP 2) VLAN= S-VLAN=1000, C-VLAN=2000
B)
EFP 1) VLAN: S-VLAN=1000, C-VLAN=any
EFP 2) VLAN= S-VLAN=1000, C-VLAN=2000,
VLAN TAG rewriting
The ASR9000/XR is capable of doing many translations on vlan to a packet.
The behavior is always symmetric (though this keyword is to be provided as part of that config command). The symmetry means that if we pop a tag on ingress, we push it back on egress.
the following rewrites are possible:
RP/0/RSP0/CPU0:A9K(config)#int gig 0/0/0/4.100 l2transport
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag ?
pop Remove one or more tags
push Push one or more tags
translate Replace tags with other tags
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag pop ?
1 Remove outer tag only
2 Remove two outermost tags
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag push ?
dot1ad Push a Dot1ad tag (ethertype 88a8)
dot1q Push a Dot1Q tag (ethertype 8100 by default, or 9100/9200 is specied on the main interface for the outter most tag)
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag push dot1q 100 ?
second-dot1q Push another Dot1Q tag
symmetric All rewrites must be symmetric
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag translate ?
1-to-1 Replace the outermost tag with another tag
1-to-2 Replace the outermost tag with two tags
2-to-1 Replace the outermost two tags with one tag
2-to-2 Replace the outermost two tags with two other tags
If you want to make a cross connect or bridge between two EFP's where one EFP is vlan 100 and the other EFP is vlan 200,
you need to make sure you pop the tags so that the vlan 100 is removed from the packet so it, by means of symmetry, will get vlan 200 on the egress
of the other EFP.
L2VPN configuration examples and comparison to 7600
The following picture highlights how to create L2 services on the ASR9000.
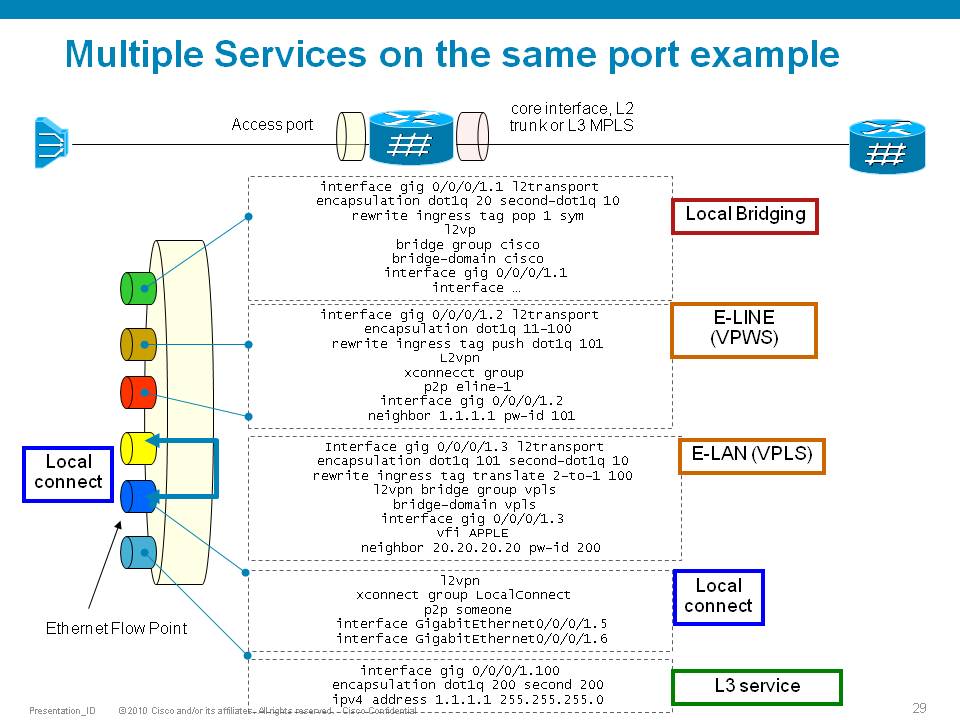
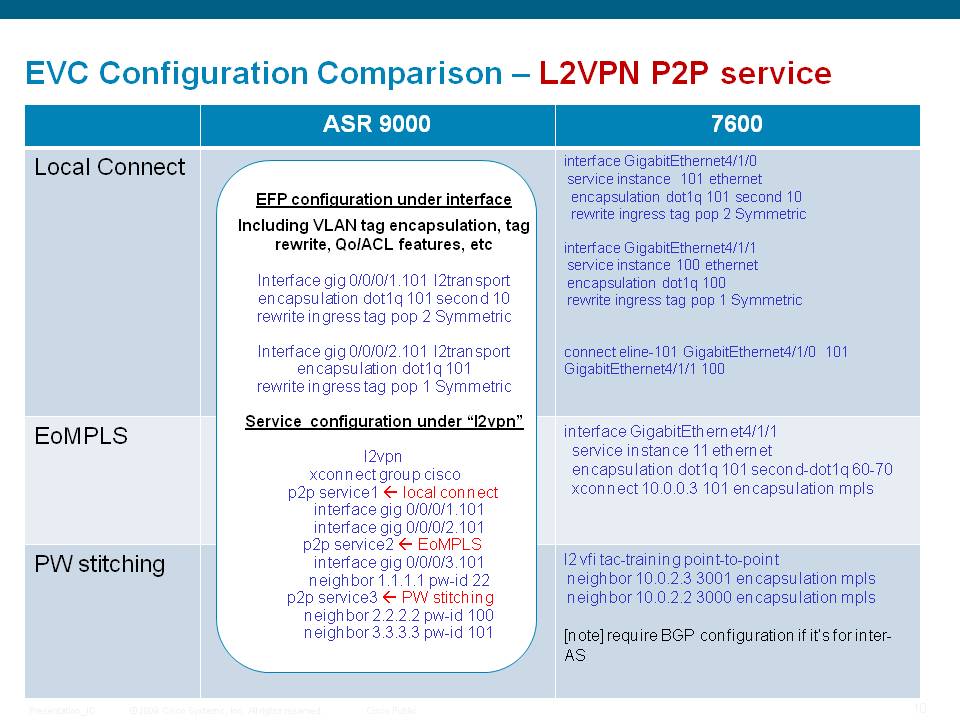
Using IRB/BVI
To provide L3 services in a bridge-domain, you can add a routed interface to the bridge domain.
What is important here is that the BVI is not vlan tagged. So in order for the EFP's to talk to the BVI, we need to pop ALL Tags on ingress!!
This means that frames with more then 2 tags cannot be natively using the BVI, unless we do some workarounds such as loopback cables to
pop more tags.
interface BVI5
ipv4 address 31.1.1.1 255.255.255.0
mac-address 0.4343.3434
! when creating the bvi verify the show int bvi to see if the mac address is correctly programmed, these macs are coming from the backplane mac table, ! if we ran out because of so many bundle interfaces etc, you may need to provide a mac manually.
interface TenGigE0/7/0/3.100 l2transport
encapsulation dot1q 100
rewrite ingress tag pop 1 symmetric
l2vpn
bridge group testing
bridge-domain testing
interface TenGigE0/7/0/3.100
!
interface GigabitEthernet0/1/0/14
!
routed interface BVI5
!
Related Information
Dot1q, Dot1ad and configuring "dot1q tunneling ethertype on the physical interface:
Xander Thuijs, CCIE #6775
Sr. Tech Lead ASR9000
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
That is great, Xander.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Dear Xander Thuijus,
Thank you for this article!
Can you please explain if EFPs (with options mentioned in the article above) can be made over bundle interface instead of a physical interface.
Best regards!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Atif, appreciate your comment! Yes you can use bundle interfaces as an EFP also.
The configuration for that would be:
int g0/0/0/0
bundle id 100 mode act
int bundle-e100
int bundle-e100.123 l2trans
encap dot1q 123
etc. the bundle-id number references the bundle interface number, they must match.
the subinterface in my example 123 does not need to be linked to vlan 123, but is nice for consistency.
The bundle EFP's can now be used as an AC in an l2vpn xconnect/vpls etc.
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Dear Alexander,
Thanks!
Is it possible to have an alternative of open trunk as we use to have it in switches. (switch mode trunk).
In my scenario, i have a pair of PEs where each PE is configured with X number of BVI interfaces with HSRP on them. To have redundant L2 connectivity between the two PEs, i want to have direct L2 link b/w PEs. One way of doing is to have EFP configuation per BVI on this direct link b/w PEs exactly the same way as it is done on the access ports (connected to access switches). Can we have just one EFP (similar to open trunk in 7600) which will provide L2 connectivity for all BVIs configured in both PEs?
So far, i didn't find any such option. I believe it is the hard way we have to go with.
Regards!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Atif,
great question! I like your analogy of open vs closed. IOS-XR with the EVC model follows the normally closed model, so you have to define your EFP's which you want to trunk the vlans for.
I have a document here on how to "convert" an IOS trunk to an XR like model.
You can define an EFP with a vlan range (aka ambigious), but you can't pop the tags from it. Popping the tag is required when using BVI. Popping a tag on an ambigious range would not allow you to slap the tag back on in the egress direction as we have no clue what the tag would be in that direction.
As powerful as the XR implementation is, the "open trunk" situation is unfortunately one drawback that bloats the configuration a bit as opposed to the IOS model...
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi dear Xander how are you..., I would like to know if it´s possible in the MSE ASR9000 configure a port to support, at the same time, a level two interface, for instance
S-VLAN 100 C-VLAN 30-3016, and a level 3 interface EFP S-VLAN 100 C-VLAN 3017-3999. You see, both interfaces with the same S-VLAN. If this is possible, the idea is to associate each kind of traffic to a different VPLS.
I know you will be wondering why I want to do this. Believe me we have a PTN equipment (my working area has inherited) that for a matter of performance we can only configure a unique pwe towards another one which is the border connected to our NPE. And of course we need to transport on it three services, which would detect them because of the C-VLAN as I have describeb in the previous paragraph.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Humphry
yes you can!
note however that for l3 interface the encap cannot be ambigious, but you can do something like this:
interface GigabitEthernet0/1/0/10.1003017
encapsulation dot1q 100 second 3017
ipv4 address 1.1.1.1 255.255.255.0
!
interface GigabitEthernet0/1/0/10.10030316 l2transport
encapsulation dot1q 100 second-dot1q 30-3016 <<< ambigious range
The L2 transport interface can then be pulled into an xcon or BD no problem, while the L3 subif does routing.
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Xander!!
Regards,
Javier.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander, may you let me some more questions,... currently we dont see the inner tag to filter. We only check the SVLAN to map the services to differents vpls (we have any in the encapsul sentence, you see). The fact that we must filter looking at the c-valn with ambiguous range and also have L3 interfaces, t does impact in the NPE performance? what kind of resources does it consume?
Regards,
Javier
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hey Javier, The flexible vlan matching is taken care of by the TCAM per NP.
regardless of the vlan stack and the range it has it is just a single tcam lookup.
The tcam has a pre-carved (set of) regions for this vlan matching to EFP and that is why there is a scale limit of the number of EFP's per NP. So as long as you stay within that range which is documented on the linecard specifications and is different betwee L/B/E cards (trident based) or TR/SE (typhoon based).
regards!
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander,
I have a scenario that inner VLANs is unique but outer VLAN is different, in this case can we use the following configuration.
interface Bundle-Ether10.100 l2transport
encapsulation dot1q any second-dot1q 100
rewrite ingress tag pop 2 symmetric
and use a BVI to have the Layer3 IP address.
Rgds
Harin
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Using ambigious vlans is not recommended (/not working) when popping tags.
the reason for that is that the system doesn't associate macs with vlans for that matter in this case
so packets on egress can't be rewritten with the right outer tag value in this amb case.
Note that 9k BNG can do this though with ambigious vlans (no popping) as the PPPoE session table or dHCP binding will remember the vlan (combo) and is able to slap on the right vlan for the session in amb cases.
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You need to create a bridge per vlan and pull in a bvi into that bd for your routed endpoint:
int g 0/0/0/0.10 l2trans
encap dot1q 10
rewrite ingress tag pop 1 sym
int bvi 10
ipv4 add 192.168.x.y
l2vpn
bridge domain VL10
bridge group VL10
int g 0/0/0/0.10
routed-interface bvi10
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
bundle efp's are created like this:
int g 0/0/0/0
bundle id 100 mode active/on/passive
int bundle-e 100 (number must match the id given above)
int bundle-e 100.10 l2trans
encap dot1q 10
rewrite ingress tag pop 1 symm
and the bd then pulls in this newly created EFP.
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
two minor nits, but in general the gist here will work:
1) add a config item for the main bundle interface
interface bundle-ether 100
2) the bridge group and domain are reversed
l2vpn
bridge group VL10
bridge-domain VL10
...interfaces...
other then that all good.
xander
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: