- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Anyconnect Dynamic Split Include Tunneling
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Anyconnect Dynamic Split Include Tunneling
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2020 07:48 AM - edited 04-21-2020 12:35 AM
Hi,
When configuring split tunnel on the ASA an ACL must be configured to filter which subnets will be allowed over the VPN tunnel, this is ok when internal networks are RFC 1918 compliant, however in some cases i have seen companies using public ip addressing internally that is not owned by the company, this causes IP overlapping when deploying split tunnel VPNs.
In order to overcome this issues, there is a feature called Dynamic Split Include Tunneling which is configured as a Anyconnect custom attribute and uses FQDN instead of IP when filtering the traffic that goes over the VPN.
I am wondering if split tunnel can be configured using only anyconnect custom attributes or if IP subnetworks still need to be defined on the split tunnel section in group policies?
TIA
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2020 11:32 AM
I dig into to this but could not find an answer what you looking for but find this link might help you out https://woland.com/2020/03/30/dynamic-split-tunneling-a-covid-19-best-practice/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2020 02:34 PM
Bonjour,
Je suis dans le même cas. Je n'arrive pas à mettre en place le Dynamic Split incluse via l'ASDM via l'ASA. Malgré avoir rajouté les attributs names dans la group policy et de rajouter une ACL standard, il est indiqué NONE dans la partie statisic Annyconnect pour Dynamic Split inclusion
Aucun problème par contre pour le Dynamic Split excude. Cela fonctionne.
Quelqu'un peut il m'aider svp je m'attache les cheveux !!!
Merci encore
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2020 01:59 AM
Hello,
I am in the same situation. I am unable to set up the included Dynamic Split via ASDM via ASA. Despite having added the names attributes in the group policy and adding a standard ACL, it is indicated NONE in the statistics part Annyconnect for Dynamic Split inclusion
No problem on the other hand for the Dynamic Split excude. It works.
Can someone help me please
thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 12:16 AM
Hi all,
After much digging around,and to answer the original Post Dynamic split tunnel Include requires at least 1 IP network or host to be configured under the Group Policy > split tunneling section.
There is a very helpful guide here, written in detail, which i think it can help many of you
Happy VPN Tunneling 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2020 07:50 AM
Hi,
Thanks but it's don't work for me by follow your procedure for dynamic split include by group policies:( but why in this procedure, he do exclude on attribution name in group policies , it'is a mistake no ?
Dynamic tunnel inclusion display "none" on statistic
ASA: 9.8(4)
ASDM Version 7.12(2)
Devyce type: Firepower 2110
Annyconnect : 4.9.04043
Can you help me please , i browse my file on attach
many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2020 01:00 AM - edited 12-03-2020 01:00 AM
Salut Zidane
From your attachment i assume that your are missing some configuration for the dynamic split include tunnel to work properly, you do not have specified the internal domains that should go over the tunnel.
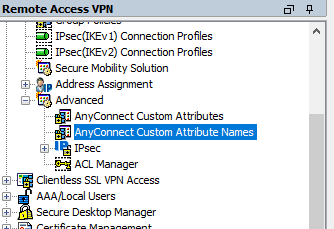
To specify the domains go to:
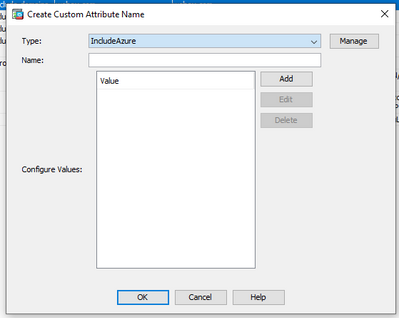
Once in this section click on the ADD button and in the type field select the IncludeAzure attribute you have created previously.
then click on the Add button to add the domains you which to split include. Once all this configuration is done you can attach it to the group policy like you did.
All this configuration can be done through the CLI as well and in my opinion is actually simpler.
ASA(config)#webvpn
ASA(config-webvpn)#anyconnect-custom-attr IncludeAzure description tunnel-traffic-to-Azure
ASA(config-webvpn)#exit
ASA(config)#anyconnect-custom-data IncludeAzure azure-domains azure.micro.com,azure.soft.com [the domains must be separated by a comma or space not sure now]
ASA(config)# group-policy [your-group-policy] attributes
ASA(config-group-policy)# anyconnect-custom dynamic-split-include-domains value azure-domains
If you still need help, please post your cli conf related to the split tunnel include.
Good Luck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2020 06:22 AM
Hi,
It's don't working 😞
I have
anyconnect-custom-attr IncludeAzure description Dynamic_Include
anyconnect-custom-data IncludeAzure Include domain.fr
group-lock value TEST
split-tunnel-policy tunnelspecified
split-tunnel-network-list value IP_TEST
default-domain value domain.com
split-tunnel-all-dns disable
anyconnect-custom IncludeAzure value Include
webvpn
html-content-filter none
anyconnect ask none default webvpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2020 01:11 AM
Hi Zidane,
I am not sure, i think the anyconnect-custom-attr must be dynamic-split-include-domains instead of IncludeAzure, this is what is described in the official doc and it was the attribute type i used in my setup. Try and change the attribute type according to the official doc. You can find more information in the following URL:
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 11:16 PM
Hello,
Sorry for the late but it is working !!
Thank you very mutch GoncaloReis.
Have a good day
Zidany
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide