- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Using DUO with ISE 2.3 and ACS 5.X for 2FA Cisco Network Admin Access
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 02-15-2018 10:27 AM
Have tested using DUO with ISE2.3 and ACS 5.6 for network device access using 2FA. Here are the steps for your reference:
- Setup DUO proxy server and add ISE IPs as DUO proxy clients
- In ISE, add DUO as a RADIUS Token in Administration > Identity Management > External Identity Sources.
- Change Server Timeout value to 30 (or other appropriate value) seconds from default to relax user input timeout under Connection tab, make sure you have the correct DUO proxy server IP address and Shared Secret value entered there. Add the secondary server info if you have HA setup for the DUO proxy servers
- Add network admins under Identities > Users and Create an Identity group, such as Net Admin; add all network admin users you created under Identities to the group. Note: make sure that the user you added in pick DUO as the Password Type under Passwords
- Create a policy set for network admin access with condition DEVICE: Network Device Profile EQUALS: Cisco, where Cisco includes all your Cisco network devices and this just an example for Cisco. Note: Make sure that you put the new policy set at the bottom of Policy sets if you have multiple policy sets, such as VPN clients, wireless clients, and so on since you do not want to use the same admin user names as other user names, such as AD domain user name.
- Authentication Policy: set protocol match condition equal to Radius
- Authorization Policy: set Identity group equal to network admin group which you have created above
- Configure Cisco device AAA section
- Create a Radius server group and add ISE servers under that group
- Configure authentication login default group using radius with optional local after radius failed
- Configure authorization commands default group using tacacs+ assuming you already have this group with ACS IPs configured.
Test it out and enjoy it
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you very much for adding your notes for ISE/ ACS integration with Duo.
I will add this to the 2FA community page.
Two Factor Authentication on ISE – 2FA on ISE
-Krishnan
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you so much for sharing. I am currently deploying ISE 2.3 in our network and definitely TACACS+ is a key component of that deployment. We are also looking into deploying DUO, I am new to DUO and 2FA so with this setup regardless if its an on or off campus access 2FA will always occur?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
It's the same way as any of the other services. It's depending on your setup, using privatr or public IP for the Duo proxy servers
Thanks,
Song
Sent from my iPhone
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
what about if they want to use the PIV/CAC card for user authentication form VPN users, can that be done using ISE?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
is this a specific ask for this product or a general question? if the latter please post a new question with the deep details and product you're asking about
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am seeing conflicting designs out here!
I see a design were the ASA points to ISE and then ISE points to Duo Proxys. Duo proxy is setup as RADIUS TOKEN and ISE is setup as RADIUS server in duo config.
I am having lots of issues with this config. I have also figured out that with this configuration, if the user is configured in AD but NOT duo they still authenticate to the vpn. I assume this is because the ASA looks to ISE and if ISE says its good then it sends it back to the ASA and the user auths freely without the intervention of DUO. If ASA points to DUO then DUO does the first check for the user in DUO. Am I right in that thinking?
Then I see designs that say ASA points to DUO proxy and DUO proxy points to ISE and ISE servers are radius clients in the DUO config.
I have not tried this but here are the issue with that:
ASA will only point to a single DUO proxy so single point of failure there, so I can see putting DUO proxys behind a F5 VIP and use it that way. But I am issues with that on its own due to the fact that the DUO proxy is a service, so if the service is down but the node can answer icmp its still "UP" and never fails over to secondary DUO Proxy or takes the primary offline.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Mountain Man this just about worked for me but here are my findings still got this working though slightly different method.
I had a look at the ACS/ISE guide which is also shared by duo. I ran into an issue with ISE 2.4 Patch 5. When I added an external ID source I got a lot of error 401 in the DUO proxy log. Our initial login to the devices was via RADIUS not TACACS.
I fixed the issue by configuring the DUO auth proxy as an external radius server with timeout of 60 seconds.
Configured a radius server sequence pointing to the new external RADIUS server.
In the advance options select continue to Authorization policy on access acept
Configured the policy set in ISE to reference the external RADIUS server sequence.
Configured authorization polices as required with different levels of access.
Hope this helps anyone who is struggling to get ISE working with RADIUS MFA from network device. I also believe this would work for other RADIUS base logins via ISE.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have moved to a completely different design that I have worked with Cisco and DUO with and we have decided it was the best design for my scenario.
In my scenario we moved to the Cisco ASA doing the authentication (DUO Only) to the DUO API in the Cloud. This was used as secondary authentication and then primary authentication was to Cisco ISE for AD and dACL.
The issue with using ASA -> ISE -> Duo Proxy is we has major timing issues with the push method to people phones. It was causing lock outs consistently so we needed a new solution.
Then we tried ASA -> DUO Proxy -> ISE. The issue here was CoA. I couldn't get users assigned to the correct dACL and I think the issue was the DUO Proxy couldn't pass the CoA packet to the ISE server.
So that lead us to ASA doing the auth to both ISE and DUO. It has cleared up the timing issues and has removed 2 Duo Proxies from my VMware environment.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Steven02-19-2019 06:32 AMI have moved to a completely different design that I have worked with Cisco and DUO with and we have decided it was the best design for my scenario.
In my scenario we moved to the Cisco ASA doing the authentication (DUO Only) to the DUO API in the Cloud. This was used as secondary authentication and then primary authentication was to Cisco ISE for AD and dACL.
I'm surprised Cisco have not put more effort into detailing this integration.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
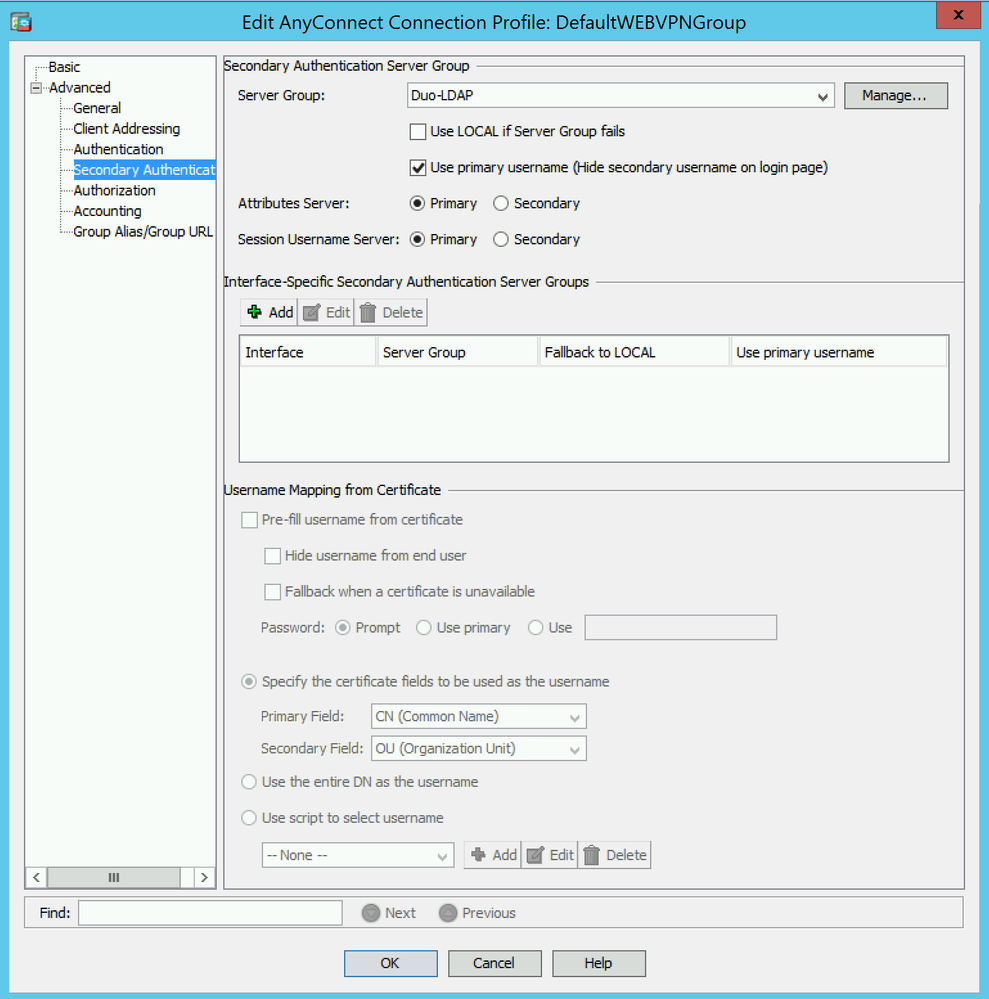
ISE is primary Authentication and DUO-LDAP is secondary authentication
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: