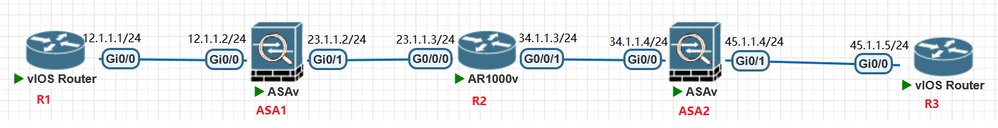
R1有一个环回口lookup 0(1.1.1.1) ,比如R1上带源lookup 0(1.1.1.1) 去 ping R5的lookup 0 (5.5.5.5) 地址,ICMP包到达 ASA1防火墙的时候,封装类似gre over ipsec vpn隧道的SVTI 外层隧道地址,外层隧道地址的源为ASA1的 trust区域的Gi0/0 (12.1.1.2) 目的地址为 ASA2的trust区域的Gi0/1( 45.1.1.4) ,然后ICMP包到达ASA2后,解封装SVTI隧道外层地址,露出内层地址源 1.1.1.1 目的 5.5.5.5,再送往R3路由器。
其中ASA1的trust区域的Gi0/0(12.1.1.2)无法和ASA2的trust区域的Gi0/1(45.1.1.4)建立SVTI隧道,现在罗列出三台关键设备 ASA1 - R2 - ASA2 的配置,至于R1和R3的配置就不列出了。
设备配置如下:
ASA1配置:
interface GigabitEthernet0/0
nameif trust
security-level 100
ip address 12.1.1.2 255.255.255.0
no shutdown
interface GigabitEthernet0/1
nameif untrust
security-level 0
ip address 23.1.1.2 255.255.255.0
no shutdown
---
object network nei_wang
subnet 12.1.1.0 255.255.255.0
object-group network internet_group
network-object object nei_wang
---
object network wai_wang
subnet 45.1.1.0 255.255.255.0
object-group network outside_group
network-object object wai_wang
---
object-group service ipsecSERVER
service-object gre
service-object esp
service-object ah
service-object udp destination eq isakmp
---
ACL放通策略,放通建立SVTI的源和目地址的所需要的服务
access-list trust-untrust extended permit object-group ipsecSERVER object-group internet_group object-group outside_group
access-list trust-untrust extended permit object-group ipsecSERVER object-group outside_group object-group internet_group
---
把以上定义的ACL包括允许访问的服务,源地址,目的地址应用到对应的区域trust包含的接口上去,主要目的是放行SVTI隧道建立的源12.1.1.2,到目的45.1.1.4的建立隧道的两个阶段的流量
access-group trust-untrust in interface trust
---
放行tunnel所在AS3区域接口的流量,为了让刚兴趣流比如从R1流到当前ASA1时的 源1.1.1.1,目的5.5.5.5的经过tunnel隧道的时候被封装外层SVTI地址放行,目前不知道是不是要放行该流量,首先先列举配置出来,先放行所有流量.
access-list as2_access_in extended permit ip any any
access-group as2_access_in in interface as3
---
首先,在内部trust区域接口上启用IKEv2并配置IKEv2策略
crypto ikev2 policy 10
encryption aes-gcm-256 aes-gcm-192 aes-gcm
integrity null
group 20 5
prf sha512 sha384 sha256 sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes-256 aes-192 aes
integrity sha512 sha384 sha256 sha
group 20 5
prf sha512 sha384 sha256 sha
lifetime seconds 86400
crypto ikev2 enable trust
---
配置IKEv2第二阶段的IPsec转换集和IPsec配置文件。
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal as2-proposal
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto ipsec profile as2-proposal
set ikev2 ipsec-proposal as2-proposal
---
然后,在ASA上使用步骤3中定义的预共享密钥配置组策略和隧道组。预共享密钥用于第一阶段协商认证的.
group-policy as2 internal
group-policy as2 attributes
vpn-tunnel-protocol ikev2
tunnel-group 45.1.1.4 type ipsec-l2l
tunnel-group 45.1.1.4 general-attributes
default-group-policy as2
tunnel-group 45.1.1.4 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco@123
ikev2 local-authentication pre-shared-key cisco@123
---
interface Tunnel1
nameif as3
ip address 10.2.100.1 255.255.255.252
tunnel source interface trust
tunnel destination 45.1.1.4
tunnel mode ipsec ipv4
tunnel protection ipsec profile as2-proposal
route trust 1.0.0.0 255.0.0.0 12.1.1.1
route untrust 0.0.0.0 0.0.0.0 23.1.1.3
route as3 5.5.5.5 255.255.255.255 10.2.100.2 1
---
ASA2的配置:
interface GigabitEthernet0/1
nameif trust
security-level 100
ip address 45.1.1.4 255.255.255.0
no shutdown
interface GigabitEthernet0/0
nameif untrust
security-level 0
ip address 34.1.1.4 255.255.255.0
no shutdown
---
object network nei_wang
subnet 45.1.1.0 255.255.255.0
object-group network internet_group
network-object object nei_wang
---
object network wai_wang
subnet 12.1.1.0 255.255.255.0
object-group network outside_group
network-object object wai_wang
---
object-group service ipsecSERVER
service-object gre
service-object esp
service-object ah
service-object udp destination eq isakmp
---
ACL放通策略,放通建立SVTI的源和目地址的所需要的服务
access-list trust-untrust extended permit object-group ipsecSERVER object-group internet_group object-group outside_group
access-list trust-untrust extended permit object-group ipsecSERVER object-group outside_group object-group internet_group
---
把以上定义的ACL包括允许访问的服务,源地址,目的地址应用到对应的区域trust包含的接口上去,主要目的是放行SVTI隧道建立的源45.1.1.4,到目的12.1.1.2的建立隧道的两个阶段的流量
access-group trust-untrust in interface trust
---
放行tunnel所在AS3区域接口的流量,为了让刚兴趣流比如从R1流到当前ASA1时的 源1.1.1.1,目的5.5.5.5的经过tunnel隧道的时候被封装外层SVTI地址放行,目前不知道是不是要放行该流量,首先先列举配置出来,先放行所有流量.
access-list as2_access_in extended permit ip any any
access-group as2_access_in in interface as3
---
首先,在内部trust区域接口上启用IKEv2并配置IKEv2策略
crypto ikev2 policy 10
encryption aes-gcm-256 aes-gcm-192 aes-gcm
integrity null
group 20 5
prf sha512 sha384 sha256 sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes-256 aes-192 aes
integrity sha512 sha384 sha256 sha
group 20 5
prf sha512 sha384 sha256 sha
lifetime seconds 86400
crypto ikev2 enable trust
---
配置IKEv2第二阶段的IPsec转换集和IPsec配置文件。
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal as2-proposal
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto ipsec profile as2-proposal
set ikev2 ipsec-proposal as2-proposal
---
然后,在ASA上使用步骤3中定义的预共享密钥配置组策略和隧道组。预共享密钥用于第一阶段协商认证的.
group-policy as2 internal
group-policy as2 attributes
vpn-tunnel-protocol ikev2
tunnel-group 12.1.1.2 type ipsec-l2l
tunnel-group 12.1.1.2 general-attributes
default-group-policy as2
tunnel-group 12.1.1.2 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco@123
ikev2 local-authentication pre-shared-key cisco@123
---
interface Tunnel1
nameif as3
ip address 10.2.100.2 255.255.255.252
tunnel source interface trust
tunnel destination 12.1.1.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile as2-proposal
route trust 5.0.0.0 255.0.0.0 45.1.1.5
route untrust 0.0.0.0 0.0.0.0 34.1.1.3
route as3 1.1.1.1 255.255.255.255 10.2.100.1 1
----
华为路由R2的配置:
interface G0/0/0
ip address 23.1.1.3 255.255.255.0
no shutdown
interface G0/0/1
ip address 34.1.1.3 255.255.255.0
no shutdown
ip route-static 45.1.1.4 255.255.255.255 34.1.1.4
ip route-static 12.1.1.2 255.255.255.255 23.1.1.2
已解决! 转到解答。
- 标签:
-
路由协议
这个是思科官方的SVTI建立隧道的ipsec vpn的配置,以上也是按照文档配置,还是SVTI隧道无法建立,奇怪
https://www.cisco.com/c/zh_cn/support/docs/security/adaptive-security-appliance-asa-software/214109-configure-asa-ipsec-vti-connection-to-az.html?dtid=osscdc000283
切记,站在设备角度上,使用去往目标地址“最近”的接口作为vpn及tunnel的源接口, 受教了.
但是上面的拓扑和配置是不能建立tunnel的ipse vpn隧道吗,我怎么配置都不通的,是不是怎么配置都无法建立隧道呢
trust接口可以不用挂acl,高安全级别到低安全级别的流量默认是permit的,保证trust的security-level高于untrust即可
这点我也明白了,谢谢大神赐教.



