思科ISR4351router的点对点IPSEC VPN问题
本段Cisco 4351 Rouer配置(对端是阿里云环境,阿里云环境与Cisco 3800Router的点对点VPN同配置OK):
crypto isakmp policy 1
hash md5
authentication pre-share
crypto isakmp key key*** address 47.100.*.*
!
!
crypto ipsec transform-set k** esp-des esp-md5-hmac
mode transport
!
crypto map ***map 1 ipsec-isakmp
set peer 47.100.*.*
set security-association lifetime seconds 86400
set transform-set k*
set pfs group1
match address 187
!
interface GigabitEthernet0/0/0
ip address 60.12.*.* 255.255.255.248
ip nat outside
media-type rj45
negotiation auto
crypto map ***map
!
interface GigabitEthernet0/0/1
ip address 192.168.*.1 255.255.255.0
ip nat inside
media-type rj45
negotiation auto
!
ip nat inside source route-map SDM_RMAP_1 interface GigabitEthernet0/0/0 overload
ip route 0.0.0.0 0.0.0.0 60.12.*.*
!
!
access-list 187 permit ip 192.168.*.0 0.0.0.255 172.*.0.0 0.15.255.255
access-list 192 deny ip 192.168.*.0 0.0.0.255 172.*.0.0 0.15.255.255
access-list 192 permit ip 192.168.*.0 0.0.0.255 any
!
!
route-map SDM_RMAP_1 permit 1
match ip address 192
!
cisco4351#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
47.100.189.157 60.12.187.132 MM_NO_STATE 0 ACTIVE
IPv6 Crypto ISAKMP SA
cisco4351#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
47.100.*.* 60.12.*.* MM_NO_STATE 0 ACTIVE (deleted)
cisco4351#sh version
........
cisco4351 uptime is 1 week
Uptime for this control processor is 1 week
System returned to ROM by PowerOn
System image file is "bootflash:isr4300-universalk9.16.06.04.SPA.bin"
Last reload reason: PowerOn
.......
- 标签:
-
IOS 和 XE平台
是的,不过确实看不到啥问题。用debug crypto isakmp一开始还能抓到很多信息,后来就抓不到任何信息。
MM_NO_STATE means that the VPN phase 1 (ISAKMP) is not even negotiated
不知你的环境是否为这样的:
IPSec无法建立比较好的办法就是检查两端的配置是否匹配,ISR这边制定的阿里云的VPN GW的PIP是否正确,以及中间是否有设备阻止了,500,4500等端口。建议还是检查两端的参数是否匹配,然后本端指定对端的IP是否正确吧。
Rps-Cheers | If it solves your problem, please mark as answer. Thanks !
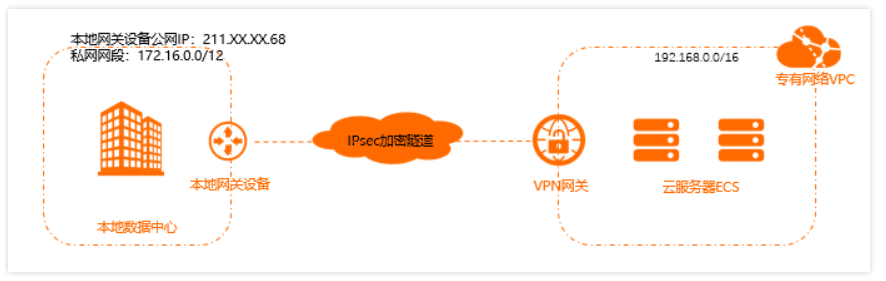
你好,示图很贴切,本地网关设备有Cisco isr4351和Cisco 3825。用Cisco3825和阿里云环境配置S2S IPSEC VPN,没有问题。用Ciscoisr4351和阿里云环境配置S2S IPSEC VPN就出现如上MM_NO_STATE问题,双边的VPN相关配置我都已确认过一致。Cisco4351和Cisco3825的G0/0/0口直接配置公网IP 60.12.*.*, 且路由可达阿里云VPN GW 47.100.*.*。这种情况下应是不会有其他设备阻止500,4500端口,不然也不会出现Cisco3825没有问题而Cisco isr4351不行的现象。我已查阅思科官网isr4351路由器的VPN配置,均是通用配置没有特别的地方。
跟云端的GW建立IPSEC的时候,建议尝试在第一阶段多选择配置hash的算法和group值看看。这里用的是ikev1,应该无法选择更多的算法和group吧。如果可以,也可以用IKEv2试试看。
不知道阿里云那边建立了S2S VPN后,是否可以根据设备的型号导出对应的配置template,如果可以的话,建议根据那个template来修改配置。
Rps-Cheers | If it solves your problem, please mark as answer. Thanks !