- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- Re: Cisco ACI L4-L7
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 04:01 AM
Hello guys,
I have a question as follows:
can I integrate checkpoint firewall into ACI in one-arm mode to make L4-L7 SG with PBR for east-west and north-sourth traffic?
Solved! Go to Solution.
- Labels:
-
APIC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 04:21 AM - edited 03-28-2020 04:24 AM
Hi,
As already mentioned in this post, yes, it is supported (assumptions: unmanaged mode. Firewall in Routed mode)
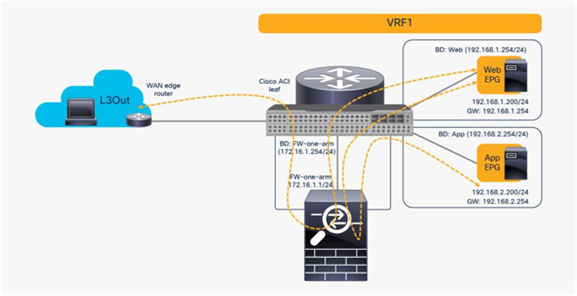
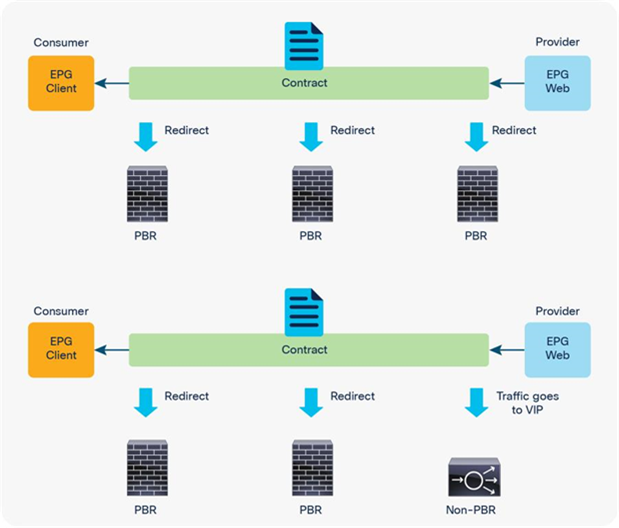
"If you want to use the same PBR node and its interfaces, you can reuse the service graph template, L4-L7 device, PBR policy, and device selection policy. In this example, traffic is redirected to FW-one-arm if it is between the L3Out EPG and the Web EPG (North-South), or between the Web EPG and the App EPG (East-West)(Figure 44)"
Figure 44.
A high level configuration example:
Here is a configuration example (Figure 45):
● Contract (Tenant > Security Policies > Contracts)
◦ Contract1: Between L3Out EPG and Web EPG
◦ Contract2: Between Web EPG and App EPG
● L4-L7 device (Tenant > L4-L7 Services > L4-L7 Devices)
◦ PBRnode1 has one cluster interface
◦ FW-one-arm
● Service graph template (Tenant > L4-L7 Services > L4-L7 Service Graph Templates)
◦ FWGraph1: Node1 is the firewall function node that is PBR enabled
● PBR policies (Tenant > Networking > Protocol Policies > L4-L7 Policy Based Redirect)
◦ PBR-policy1 (172.16.1.1 with MAC A)
● Device selection policy (Tenant > L4-L7 Services > Device Selection Policies)
◦ any-FWGraph1-FW (If FWGraph1 is applied to any contract, the firewall function node will be this node.)
◦ Node: PBRnode1
◦ Consumer: FW-one-arm with PBR-policy1
◦ Provider: FW-one-arm with PBR-policy1
Configuration example: Reuse the same PBR node (using the same interface)
Source:
Cisco Application Centric Infrastructure Policy-Based Redirect Service Graph Design White Paper
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 04:15 AM
Hi there,
Yes there is an option to add checkpoint as either a managed or unmanaged mode. For version compatibility please check the following link:
Dijar
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 04:21 AM - edited 03-28-2020 04:24 AM
Hi,
As already mentioned in this post, yes, it is supported (assumptions: unmanaged mode. Firewall in Routed mode)
"If you want to use the same PBR node and its interfaces, you can reuse the service graph template, L4-L7 device, PBR policy, and device selection policy. In this example, traffic is redirected to FW-one-arm if it is between the L3Out EPG and the Web EPG (North-South), or between the Web EPG and the App EPG (East-West)(Figure 44)"
Figure 44.
A high level configuration example:
Here is a configuration example (Figure 45):
● Contract (Tenant > Security Policies > Contracts)
◦ Contract1: Between L3Out EPG and Web EPG
◦ Contract2: Between Web EPG and App EPG
● L4-L7 device (Tenant > L4-L7 Services > L4-L7 Devices)
◦ PBRnode1 has one cluster interface
◦ FW-one-arm
● Service graph template (Tenant > L4-L7 Services > L4-L7 Service Graph Templates)
◦ FWGraph1: Node1 is the firewall function node that is PBR enabled
● PBR policies (Tenant > Networking > Protocol Policies > L4-L7 Policy Based Redirect)
◦ PBR-policy1 (172.16.1.1 with MAC A)
● Device selection policy (Tenant > L4-L7 Services > Device Selection Policies)
◦ any-FWGraph1-FW (If FWGraph1 is applied to any contract, the firewall function node will be this node.)
◦ Node: PBRnode1
◦ Consumer: FW-one-arm with PBR-policy1
◦ Provider: FW-one-arm with PBR-policy1
Configuration example: Reuse the same PBR node (using the same interface)
Source:
Cisco Application Centric Infrastructure Policy-Based Redirect Service Graph Design White Paper
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 04:53 AM
thanks everyone!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 05:28 AM
I have one more question:
can i connect one-arm to aci from firewall to aci using PC / vPC or connect to ACI by single physical interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 05:51 AM
Hi,
Yes you can use vpc for one-arm deployments. Example:
Cheers,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 06:01 AM
Hi msdaniluk, thank so much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 05:46 AM
can i connect one-arm to aci from firewall to aci using PC / vPC or connect to ACI by single physical interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2020 04:39 AM
If you ask on a Cisco community, the answer is that you can - you would be pointed out with the instruction and white paper on how to do so. Be aware of the anti IP spoofing configuration on the L4-L7 side.
If it's CheckPoint, you also are strictly required to configure a virtual MAC since even on Active/Standby, both nodes use their own interface MAC addresses to associate with the active IP. If failover happens without a vMAC, it would break your L4-L7 PBR policy.
On some others like Palo Alto or Cisco FirePower/ASA, the failover node will use both the MAC and IP of the previously active node so you're only recommended to configure vMAC as per best practice. But if you forgot to, or if you're integrating with the existing setup, you can just leave it as it is.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide