- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- Re: EPG without a physical domain association
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 04:13 PM
Hello community,
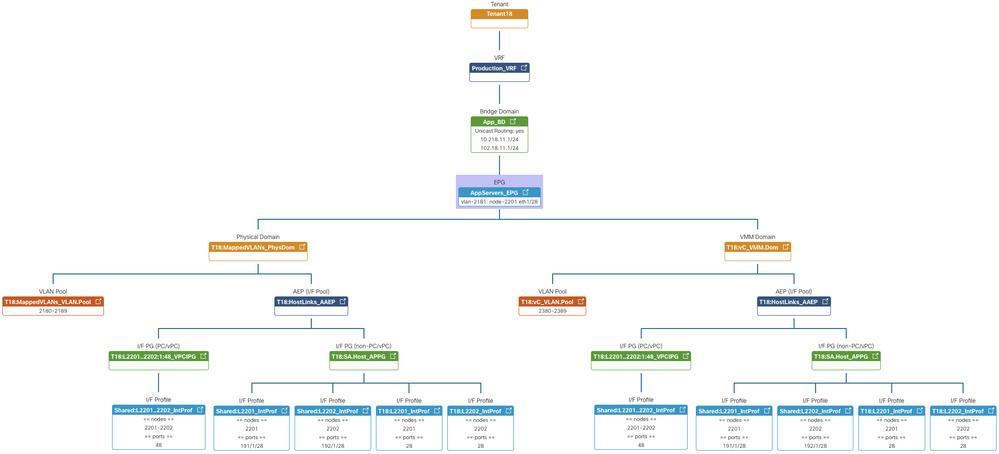
It is required to assign a physical domain to an EPG? Is not the static path assignment enough? In that case what exactly is the purpose of assign a physical domain to an EPG?
As I understood when I went over some documentation, the domain is necessary because it provides the range of VLANs that we are allowed to use in the static path assignment, this is, if our domain includes vlans from 300-350, we just cannot assign vlan 250 to an EP within that EPG.
My confusion came for the fact that in an online ACI course, the engineer forgot to include a domain in the EPG and he was still able to assign a vlan under the static port assignment for both EPs and the EPs were also able to communicate with each other with no problem at all, and no domain defined for the EPG at that point!!!
Is that the way that is supposed to be? Am I missing something here?
Solved! Go to Solution.
- Labels:
-
Cisco ACI
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 05:19 PM - edited 09-10-2021 04:22 PM
[Edited: Corrected statement on feature name per Chris' catch]
Yes its going to work without assigning a domain to the EPG. I raised the enhancement to correct this behavior many years ago and we introduced the "Enforce Domain Validation" feature under the System Settings - Fabric Wide Settings - Enforce Domain Validation. With this enabled (best practice to turn this on) it will NOT program the VLAN on the interface. Instead it will raise a fault. Even running with the configuration you have, ACI will still raise a fault on the EPG, but the programming will stuff be applied on the interface. Obviously this isn't a good idea as the Domain becomes an RBAC control point where an Infrastructure/Access Policy Admin can restrict Tenant Admins from mistakenly assigning VLANs to interfaces they shouldn't be.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 05:19 PM - edited 09-10-2021 04:22 PM
[Edited: Corrected statement on feature name per Chris' catch]
Yes its going to work without assigning a domain to the EPG. I raised the enhancement to correct this behavior many years ago and we introduced the "Enforce Domain Validation" feature under the System Settings - Fabric Wide Settings - Enforce Domain Validation. With this enabled (best practice to turn this on) it will NOT program the VLAN on the interface. Instead it will raise a fault. Even running with the configuration you have, ACI will still raise a fault on the EPG, but the programming will stuff be applied on the interface. Obviously this isn't a good idea as the Domain becomes an RBAC control point where an Infrastructure/Access Policy Admin can restrict Tenant Admins from mistakenly assigning VLANs to interfaces they shouldn't be.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 05:37 PM
Thank you Robert ! I did not know about that "Enforce EPG VLAN Validation" option, it all makes sense now !
By the way, is that feature enabled the default behavior for ACI? Or we actually need to have in mind to enable it as a best practice like you mentioned?
Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 06:23 PM
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 07:45 PM
Got it, Thank you so much Robert!
I was really struggling with that since I noticed it by mistake.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 05:06 AM
Accident or not, that's a good catch to notice this behavior. It shows you're verifying your policy deployment then questioning its operation - which I love to see. Anytime your team configures Tenant policies always check the configured object itself (EPG/BD etc) or the parent Tenant (which they all roll up into) for any faults. Quick and easy way to find & avoid issues.
Let us know if you have any other Qs.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 07:34 PM
Thank you so much, I really appreciate it!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 02:31 PM
Hi @glezJos91986 ,
Just three points to add to Robert's explanations.
Firstly, @robert is not EXACTLY right when he says:
"Enforce Domain Validation" feature under the System Settings - Fabric Wide Settings - Enforce EPG VLAN Validation (previously called Domain Validation)
because it is STILL called Enforce Domain Validation - AND there is a DIFFERENT option to Enforce EPG VLAN Validation.
So, @glezJos91986 - the feature that you really need is indeed the Enforce Domain Validation - NOT the Enforce EPG VLAN Validation.
Secondly, you need to understand that IF you have taken APIC Fabric backups or snapshots BEFORE you flick the ACI Enforce Domain Validation option on, you will NOT be able to restore them once the option has been toggled. This is because once it's turned on, you can't turn it off. And if you were to restore a Fabric backup, it would be attempting to turn the switch off.
And thridly, and this is really cosmetic - I want to make sure you know about the best App you can add to ACI - it's called the Policy Viewer - and when installed, you can look at your EPGs and see the whole Tenant AND Access Policy Chain - but ONLY after the EPG has been linked to the Domain. It is just AWESOME.
Forum Tips: 1. Paste images inline - don't attach. 2. Always mark helpful and correct answers, it helps others find what they need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 07:39 PM - edited 09-10-2021 07:41 PM
Thank you so much Chris for the aclaration/explanation and pictures.
I am really curious about this policy viewer, I will dig into it since it seems pretty useful.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2023 10:11 AM
Hi,
I have one question on enabling Enforce Domain Validation . Currently in our ACI fabric it's not enable. If I want to enable it it will impact on currently EPG traffic flow ? like MAC flapping or no MAC receive on EPG . please answer my question as soon as so I can take decision to enable that parameter at out ACI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 04:22 PM
I can always count on Chris to keep me honest! Serves me right trying to answer from memory. Updated my original response to keep the information accurate.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 07:51 PM
I appreciate your time in clarify this matter, thanks a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2023 10:44 PM - edited 09-09-2023 10:46 PM
Hello, sorry for reviving such an old post. But is this behaviour possible because it is a Port-Channel or a vPC, since you specify the Policy Group which itself is linked to the VLAN Pool?
Because if I try this with an Individual Port which I only specify the interface, no Policy Group, it requires the Domain to work.
Just trying to understand how ACI thinks. Didn't want to create another Post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2023 11:14 PM
Hi @BertiniB ,
This post is already answered. If the answer didn't answer your question, ask a new one (with reference to this one if necessary)
Forum Tips: 1. Paste images inline - don't attach. 2. Always mark helpful and correct answers, it helps others find what they need.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide