- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- "Infra" security domain does not exist
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
"Infra" security domain does not exist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 05:39 AM
"Infra" security domain does not exist! I don't know why..
APIC version 4.2, cluster with one apic.
- Labels:
-
APIC
-
Cisco ACI
-
Other ACI Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 06:04 AM
That's expected, there is no "infra" security domain by default. There's only the 'infra' tenant.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 06:17 AM
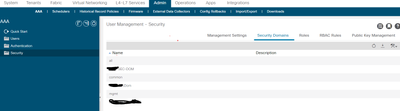
Even for infra tenant, cannot find it as you see in the capture I shared.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 06:30 AM
Your screenshot is showing security domains, not tenants. ... Show me "Tenants" > "All Tenants" screenshot while logged in with local admin account.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 06:35 AM
By default, the ACI fabric includes two special pre-created domains:
All—allows access to the entire MIT
Infra— allows access to fabric infrastructure objects/subtrees, such as fabric access policies
I talk about this Infra domain not about infra tenant as cisco documentation mentioned!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 06:51 AM
I think its just a doc error. That infra domain may have been present in earlier versions, but its not part of the more recent releases. The docs likely need updating as the only 'default' Domains are mgmt, common and all.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 07:19 AM
So how can I manage security roles for Fabric Policies and Fabric Access Policies?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 12:30 PM
Thanks @conft after I dug into this more I found we do indeed have a bug. There once was a default security domain called 'infra'. Even in the latest releases, though it doesn't exist, it's still referenced in other policies (RBAC Rules). Somewhere along the road it was removed. I'll get it added back unless engineering tells me there's a valid reason it was remove (but still referenced by other policies)
So we'll need to fix that missing 'infra' default Security Domain (I'll handle that). For now, go ahead and create a Security Domain named 'infra'. That will automatically give you access to the infra tenant (Infra tenant already associated with an 'infra' secDom). Next if you want a non-admin level user to have access to Access Policies, then you need to create an RBAC rule using the DN=uni/infra. If you want more granularity, you'll need to further create specific RBAC rules against the objects in question.
Should look something like this:
Then associate your User account with that Security Domain and privilege:
infa - admin + R/W
all - admin + R/O
This should accomplish what you need, and you can tweak/adjust it as needed from here.
Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2023 02:59 AM
Hi Robert,
How can I create Physical Domain with non-admin user?
find attached a capture with the error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2023 03:05 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2023 03:08 AM
Hi RedNectar,
Ok I will do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2023 12:38 AM
Thank you for your response !
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide