- Cisco Community
- Technology and Support
- Cisco Software
- Cisco Software Discussions
- Re: SSM LDAP Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSM LDAP Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2019 02:36 AM - edited 05-01-2019 02:36 AM
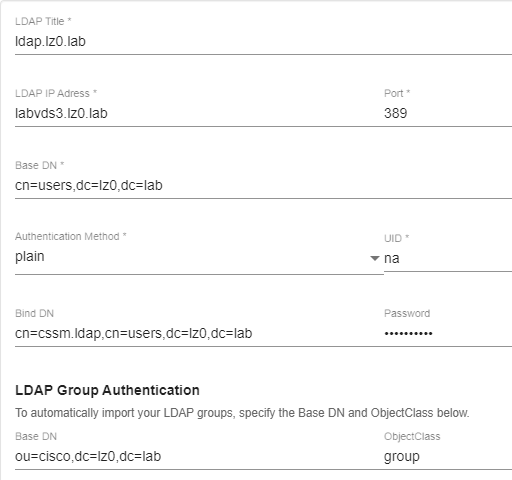
I'm trying to configure the Smart Software Manager satellite to use LDAP instead of local accounts, but I can't get this to work at present. There aren't any logs that I can see in the GUI to help with, my settings are below can anyone see what I am doing wrong?
We use non-SSL communication for LDAP/AD.
LDAP IP: 192.168.0.1 Port: 389 Base DN: OU=Admins,OU=Users,DC=Domain,DC=Local Authentication: plain UID: Cisco Service Account Bind DN: CN=Cisco Service Account,OU=Admins,OU=Users,DC=Domain,DC=Local Password: something
- Labels:
-
Cisco Software
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 01:28 PM
Also trying to resolve this issue, in your case the AD DN for Users should be:
OU=Admins,CN=Users,DC=Domain,DC=Local
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 07:54 AM
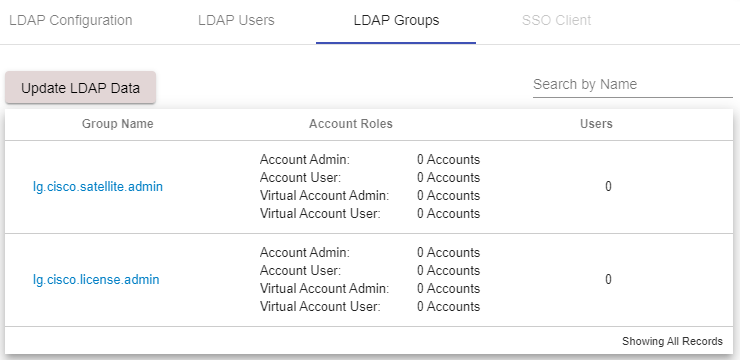
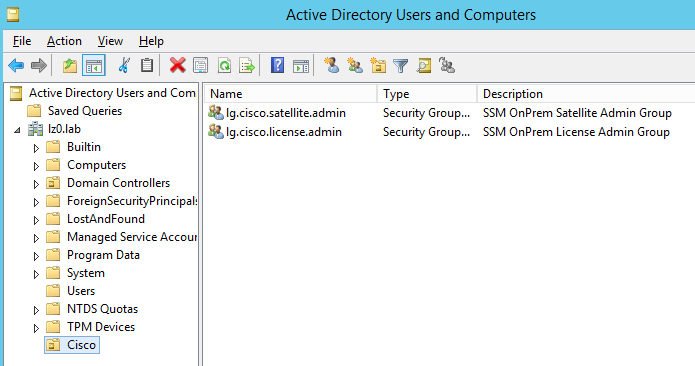
It is possible to use AD LDAP, in this case the application needs a unique gidNumber for each LDAP group object returned from the AD container.
By creating a separate ou and placing group objects with serialized gidNumbers you can fix the applications requirement for it.
The gidNumber attribute can be edited with your AD attribute editor tab or ADSI.
Once this is done you with be able to enumerate the groups within the container.
e.g.
In AD it looks like this:
I must caution anyone that looking at his using plain authentication. The password on the cssm.ladp user will be passed in the clear. With that I would advise that this user is heavily restricted and has no privilege other than reading the dedicated OU.
There are likely to be other issues that will surface here, but this is a start.
Regards,
mike.laspina
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2019 08:29 AM
Thanks for posting this - I had a look at the latest version of ssm 7-201910 released last week. It has support for AD and openldap and imports the AD groups specified in the dn if you select Active Directory - can't seem to allocate roles based on the groups though. It also has secure ldap support (simple_tls) which I've tested successfully.
The iso for the new version on the download site has an incorrect hash but the iso included in the zip (same download page) installed fine for me.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2020 01:41 AM
I have got the same issue with the group mapping. Even after upgrading to the latest version 8-202004 I still cannot see any users in my groups.
Lucas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2020 04:28 AM
I have similar problem. I am able to see LDAP groups (security groups), but I am unable to see users. I am also using the newest 8-0202004. Strange is that when I am in LDAP Users I cannot see in tcpdump initiated traffic from SSM.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide