- Cisco Community
- Technology and Support
- DevNet
- General DevNet Topics
- DevNet General Knowledge Base
- Bringing Visibility over Industrial Networks using Cisco Cyber Vision
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 09-07-2022 11:46 AM
Moving from proprietary networking technologies, to open standard networking such as Ethernet, WiFi, IP, etc improves the accessibility of data and information. Visibility and Operational Insights are key to providing security to Industrial Networks. Cisco Cyber Vision is a foundational element of Cisco's industrial security solutions that can bring full visibility into industrial environments and integrates into the rest of the Cisco Security portfolio to provide a holistic industrial security solution.
In this note we are going to find answer for the following questions?
- What is Zero Trust
- How does Zero Trust translate into industrial environments
- What is Cisco Cyber Vision
- Integrations with Cisco Enterprise Security Products
- Examples of it in action!
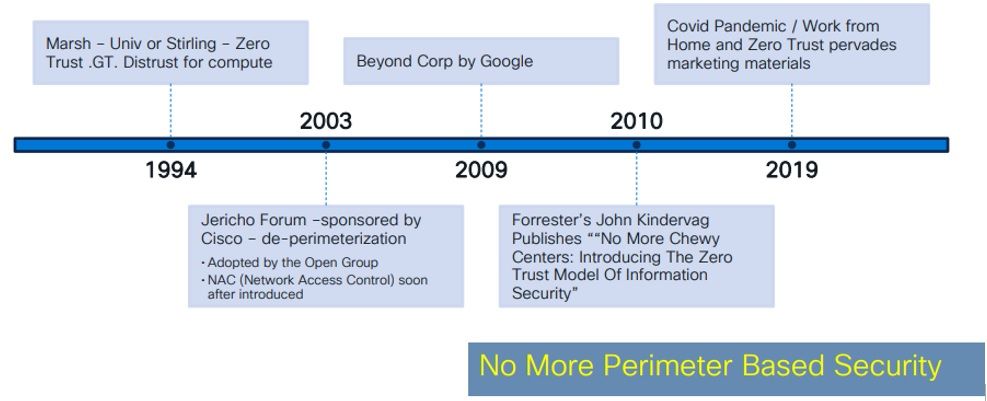
What is Zero-Trust security?
Zero Trust is a security model associated with a set of architectural principles and patterns. it’s about trying to secure everything everywhere. It is a comprehensive approach on securing all access across your networks, applications, and environment.
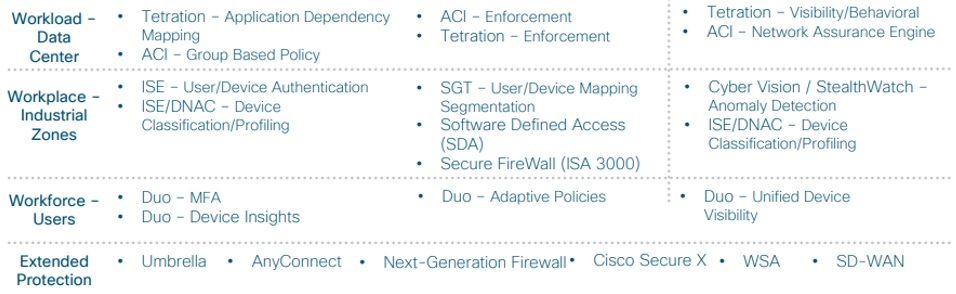
Cisco Secure Zero Trust is built on these three pillars
As the Internet of Things (Io T) world very much falls into the workplace arena these are the foundations of Zero Trust for workplaces. Industrial endpoints are not the same as the visibility endpoints in industrial settings. what you need for visibility in this particular environment is the ability to inspect traffic and decode the type of asset that is communicating on the network. Also get visibility to the communications within that traffic payload. This is based on application level decoding of the industrial traffic as well as behavior modeling of the industrial endpoint.
For more details can search on - https://www.cisco.com/c/en/us/products/security/zero-trust.html
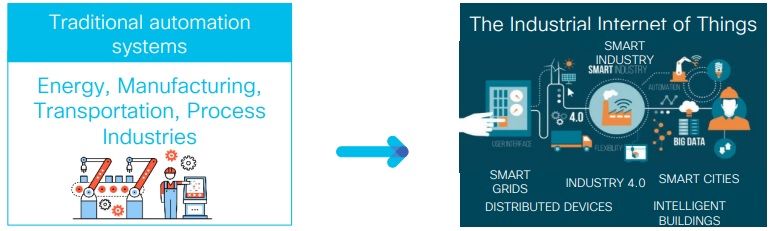
What is the current trend in Industrial IoT?
Digitization brings new requirements & challenges
- More automation devices
- IoT devices connecting to cloud
- Remote access/Hybrid work
- Malware intrusions
- New regulatory requirements
The role of IT is critical to help OT secure industrial operations- When it comes to the actual industrial environment we can see increased amount of industrial control systems are now connected to the enterprise and there is an increased volume of remote users that are connecting to the network. So the notion of the traditional perimeter is slowly going away as we can see users, devices, apps are everywhere.
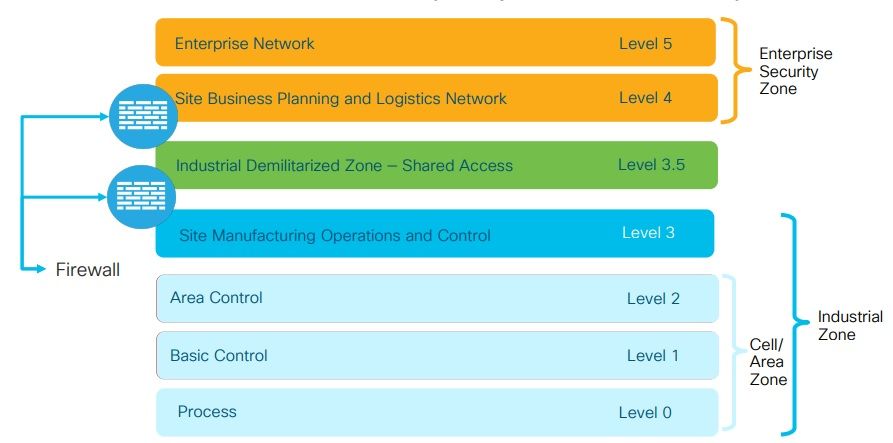
• Many dynamic applications.
• Interoperability unconstrained.
• IT teams manage the data.
• Equipment are known, modern and controlled.
• IT attacks can be identified.
OT Networks:
• Continually operating.
• Availability and safety first!
• Few defined long conversations.
• OT assets are very old.
• Attacks look like legitimate instructions.
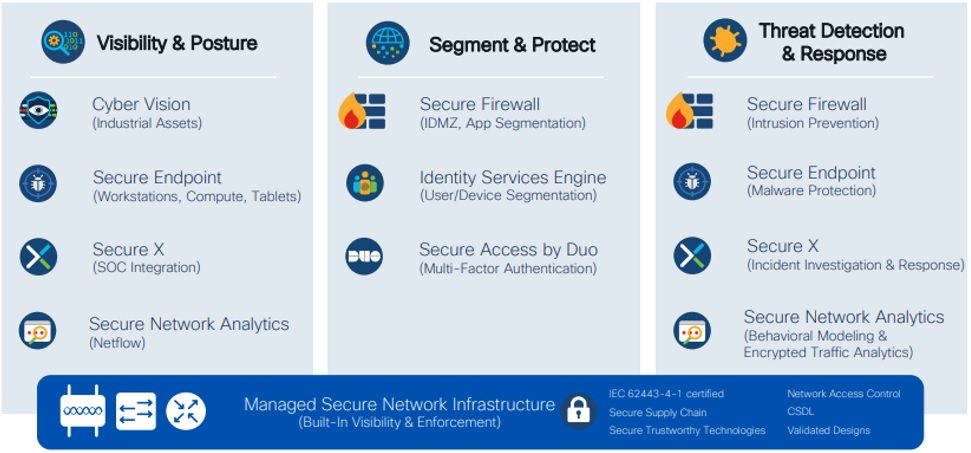
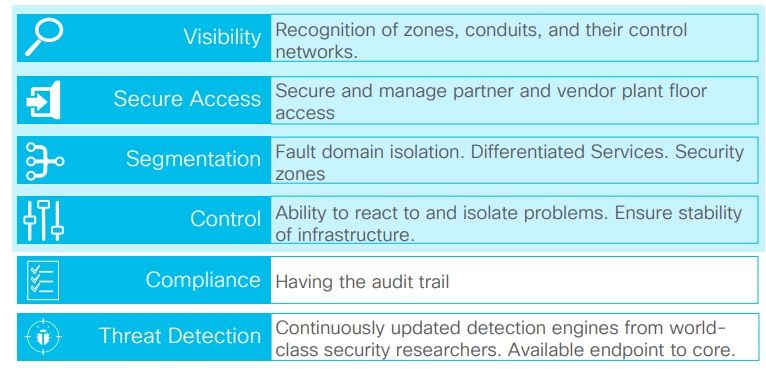
What are the Security Capabilities in Industrial Security?
Architecture for Visibility and Monitoring
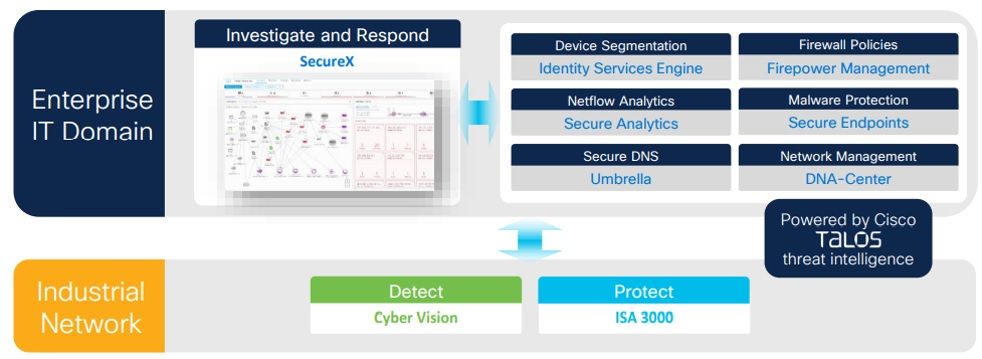
Explain Cisco’s fully integrated IT-OT security solution?
You cannot secure the “things” if you don’t know what they are. We can Integrate data from Cyber Vision into additional tools for example
- Asset Inventory - ISE + Cisco Cyber Vision
- Blind to what their assets are communicating with - Cisco Cyber Vision + Stealthwatch
For Industrial endpoint compliance these are the two key focus areas:
One is common vulnerabilities and exposures on devices. They are known vulnerabilities that have been published about industrial assets.
Second is risk coding of these endpoints - now Cyber Vision has a vulnerability feed that it uses to match known vulnerabilities about assets with what it sees on the network.
So cybervision is decoding the make model serial number of these devices matching it against the vulnerability feed and let you know which is vulnerable against which assets in your environment. Cyber Vision computes the risk score based on likelihood times impact. Cyber vision has visibility to where the asset lies in the network. It has the ability to understand what is the likelihood of this asset being compromised. When it comes to impact it's looking at the criticality of this particular asset.
What is Cisco Cyber Vision?
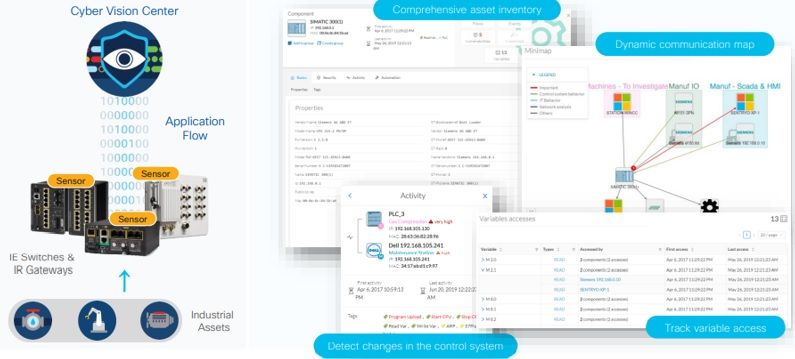
Cisco solution Cyber Vision is the product that provides the same point of visibility based on application-level decoding of industrial protocol traffic and behavior modeling of industrial endpoints. Cyber Vision provides cyber-resilience for Industrial Control Systems (ICS) that integrates with your SOC.
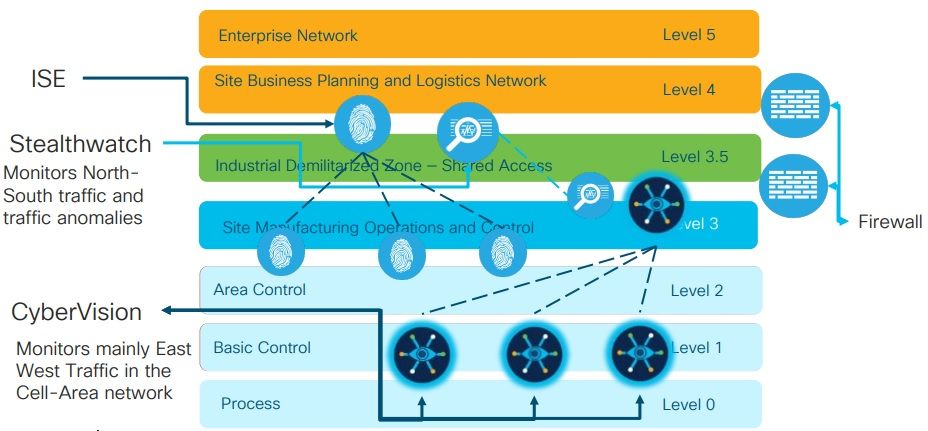
You have the component called as the cyber vision sensor that runs on the network which is a small lightweight app running within the industrial ethernet switches and gateways. It is inspecting the traffic that is traversing these devices and decoding the device identity along with the communication that's going on between these devices. All these information is sent up to the cyber vision center which is the brains of the operation. At Cyber Vision Center based on the pieces of information gathered will get you the identity of the assets and their behavior.
- Passively analyses industrial protocols and communications.
- Dynamically builds an inventory of all components and a map of all connections.
- Operational insight: extracts process information from network flows to give OT staff visibility on industrial events.
- Provides advanced anomaly detection, and real-time alerts for any threat to operational continuity and system integrity.
The key point here is that the flow of traffic is not just the network header level information. But the actual application payload of the industrial protocol. So we get to see much more than just the device identity. That is a very detailed information about the make, model, serial number and what kind of PLC program is running on the actual asset. Also we get information about the communication patterns. We know who's talking to whom and can look inside those application level payloads to understand what the device is performing. Whether it is a read operation or a write operation, or is it a PLC (Programmable Logical Controller) program to download something or to perform CPU start/ stop commands and so on. Here we go one level further and actually give you visibility into what objects or variables are being read or written.
Why do we need Segmentation?
For securing the environment to block/contain attacks. We Segment infrastructure to protect inbound and outbound communications and each other. We can also permit Identity based access for restricting connection to known systems and devices.
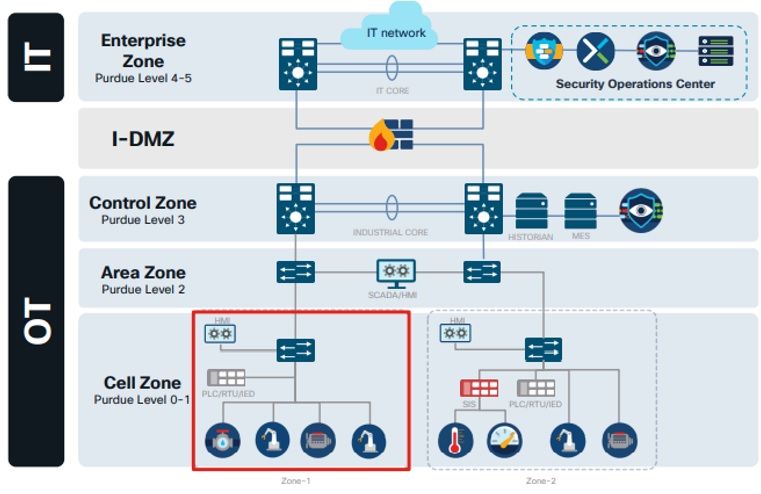
Segmentation in industrial environments is quite a challenging aspect because experts who know how to write segmentation policy are not necessarily familiar with the processes on the plant floor. This is where the Cisco solution helps you build these segmentation policies. We're focusing on endpoint visibility to identify groups of devices so you can create zones and conduits .
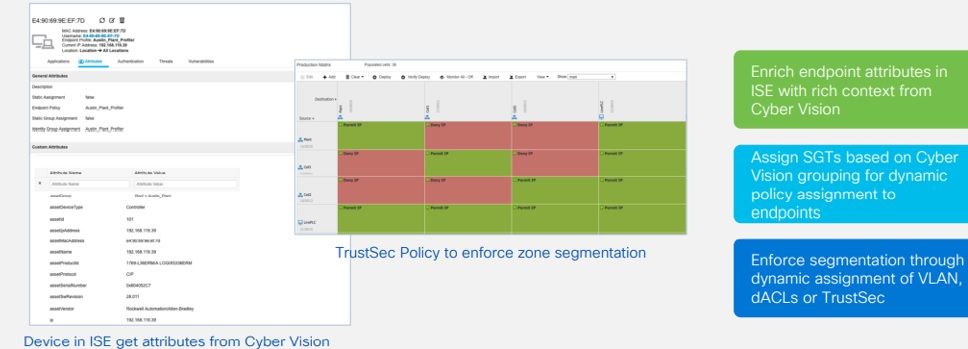
After that the ability to dynamically map assets into these zones is provided. Once you have this information it will help you assign scalable group tags to assets and this is based on integration with ISE.
How do Cyber Vision and ISE enable dynamic segmentation of industrial networks?
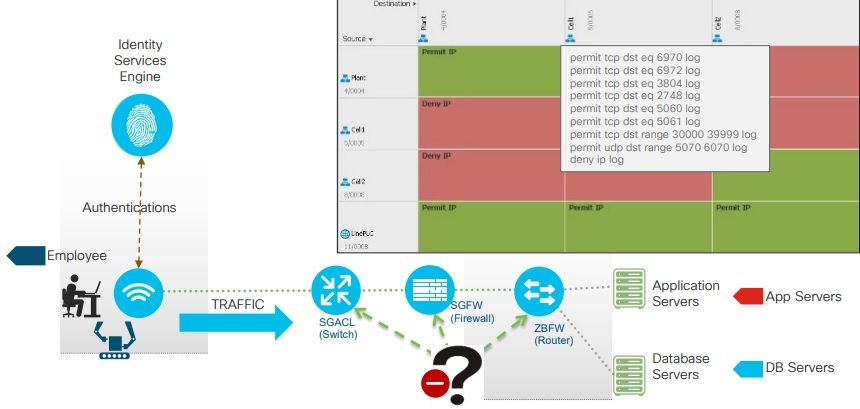
To monitor traffic patterns between scalable group tags we have to deploy the segmentation policy onto the network. Now let's take each of these step by step
- Identify zones (A grouping of logical or physical assets) and conduits (logical grouping of communication channels that share common security requirements Or connecting two or more zones). Cyber Vision gives you visibility into the communication patterns of these devices. Once you have this communication pattern it allows the user to identify the assets that belong to a certain process and at this stage the user is provided with the ability to group the assets to create zones or sales.
- Once you have mapped these assets into their respective zones we give you the ability to aggregate communication flows between these zones so you can identify conduits. Once you have this information you're now set to build your segmentation policy because you understand what devices belong together and what devices are meant to communicate with which other devices.
- Once you have that information you can assign these zones to their corresponding scalable group tags. This is again a step where the OT user needs to help the IT person who's enforcing this or who's responsible for the security policy to help define the policy.
- The way this works is that you can start by building out your segmentation logic and in this particular case we're talking about Trustsec. Here we have a simple map with two cells (a PLC & MES system). The key point here is that this Trustsec matrix can be built purely based on business logic. In this particular case devices on cell one will be able to talk to devices in cell one only but not in cell two. All cells need all devices from all cells need to be able to talk to the MES system so on and so forth.
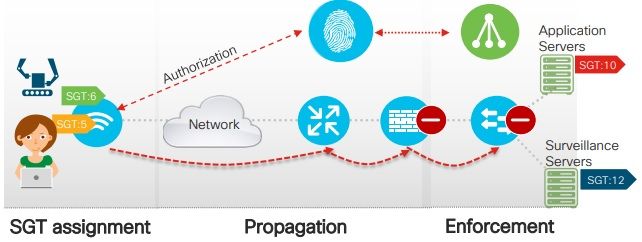
Identity Based Segmentation (TrustSec)
• Assignment of Security Group Tag (SGT) based on context (identity, device group, etc.).
• SGT are carried propagated through the network
• Firewalls, routers and switches use SGT to make filtering decisions via SGACL.
- This is a high level business logic that you can build into your Trustsec matrix even before you've discovered your assets. Once Trustsec matrix is built OT user will get the ability to log on to cyber vision and group the assets into cells or zones .
- As soon as the OT user does that An information is send to the ISE through Pxgrid . From Cisco ISE you can match this information using profiling policies that are keying off of these grouping attributes that has been send as custom attributes in Pxgrid.
- Now you can trigger a corresponding authorization policy. At this point in time we are not enforcing Trustsec on the network we're just mapping them to scalable group tags. Once you do that you can now start to observe how these scalable group tracks or traffic between these scalable group tags is flowing through the network.
- In this particular case ISE has fed the information about the segmentation mapping to policy analytics. The industrial switches in the network are feeding NetFlow information up into the policy analytics application and now you can start visualizing how various groups are communicating with each other. This allows you to model your policy take a look at whether you're breaking any flows and you can keep this monitoring in place for a couple of weeks or months to determine that your policy that you're building is not breaking any legitimate flows and causing downtime in the network.
Cyber Vision is able to detect threats and alert users in the sock about these threats and then give them the ability to run investigations in addition to the visibility aspect. Cyber vision is not only alerting you on changes in control system behavior but it also gives you the ability to set baselines according to what is normal and then the platform will alert you when there's deviation to that normal.
When it comes to signature-based threat detection we're using a smart engine and the signatures for these threats are being fed from a threat intelligence. Once a threat is detected an alert is issued by cyber vision. You have to feed that information up into the sock. The key here is to alert the sock to critical events as they happen on the plant floor by feeding events from cyber vision via syslog.
Let‘s put everything together:
- CyberVision discovers industrial assets and groupsit into Zones.
- CyberVision context is shared with ISE & Stealthwatch so that security policy can be written based on business logic: e.g. zone-1 cannot talk to zone-2.
- ISE enforces segmentation within zones based on Scalable Group Tags (SGT).
- Stealthwatch and CyberVision run analytics to raise alarms on policy violation.
- Users can trigger quarantine of offending assets .
Summary
We have gone through Cyber Vision's capabilities including OT Asset Visibility and how this information is leveraged by other Cisco solutions like ISE (Identity Services Engine), TrustSec, and Cisco Secure Firewalls to effectively construct the appropriate Security policy and enforce Segmentation without disrupting operations.
References:
- Getting started with Cisco Cyber Vision 4.0 APIs
- Cybervision Security and Automated Components Grouping
- Cisco Cyber Vision API Scripts
- Sandbox - Cyber Vision 4.0
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: