- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- D279: Duo Release Notes for Nov 27, 2023
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-27-2023 12:35 PM - edited 11-28-2023 07:10 AM
What's in this release?
- New features, enhancements, and other improvements
- Updates to the Duo Admin Panel
- Now generally available: Trusted Endpoints support for Meraki with Duo Desktop for Windows and MacOS
- TLS 1.0, TLS 1.1, and select ciphers fully removed for all Duo authentication services
- Operating systems policy updated
- Expanded support for cross-browser and cross-device passkeys
- Now in Public Preview: Unenrolled user lockout
- Temporarily disable user access through Duo Trust Monitor
- Updates to Risk-Based Authentication
- New and updated applications
- Four new named SAML applications with Duo SSO
- Duo Desktop macOS public beta version 6.1.1.0 released
- Duo Desktop Windows 10 and 11 version 6.1.0 released
- Duo Desktop Windows public beta version 6.1.1 released
- Duo Mobile for Android version 4.54.0 released
- Duo Mobile for iOS version 4.54.0 released
Hello everyone! Here are the release notes for our most recent updates to Duo.
Public release notes are published on the Customer Community every other Friday, the day after the D-release is completely rolled out. You can subscribe to notifications for new release notes by following the process described here. If you have any questions about these changes, please comment below.
Check out the Guide to Duo End-of-Life and End-of-Support Plans. This guide provides an up-to-date list of current and past end-of-life plans for Duo products.
New features, enhancements, and other improvements
Updates to the Duo Admin Panel
- Role-Based Access Control (RBAC) is now available to non-MSP (Managed Service Provider) customers with sub-accounts.
- In the Applications > Authentication Proxy report, Hide from dashboard replaces the Remove option.
- Administrators can choose to include or omit the hidden Authentication Proxies from their view by toggling the Show hidden Authentication Proxies checkbox.
- When all are shown, hidden Authentication Proxies display a Show on dashboard option.
- Administrators with the Billing role will no longer see a search bar in the Admin Panel, as they do not have access to read what comes up in search results.
Now generally available: Trusted Endpoints support for Meraki with Duo Desktop for Windows and MacOS
- Trusted Endpoint management integrations that use Duo Desktop for verification match the information reported by the Duo Desktop app to information reported by the endpoint management system to determine the computer's management status.
TLS 1.0, TLS 1.1, and select ciphers fully removed for all Duo authentication services
- As part of Duo’s end-of-support process, Duo systems for authentication will now reject requests using the following for TLS negotiation:
- DES-CBC3-SHA
- AES256-SHA
- AES256-SHA256
- AES128-SHA
- AES128-SHA256
- AES128-GCM-SHA256
- AES256-GCM-SHA384
- ECDHE-RSA-DES-CBC3-SHA
- TLS 1.0
- TLS 1.1
- Ciphers:
Operating systems policy updated
- Effective November 14, 2023, Android 10 is considered End of Life by Duo operating systems policy.
Expanded support for cross-browser and cross-device passkeys
- WebAuthn credentials registered via iCloud keychain in macOS or iOS Chrome 118 and later can now be used for authentication in Safari, and vice versa on all macOS and iOS devices signed in with the same iCloud account with iCloud keychain enabled.
Now in Public Preview: Unenrolled user lockout
- Administrators can now specify how many days an unenrolled user can remain in an active state before being locked out under Settings > Lockout and Fraud in the Duo Admin Panel.
- Locked-out users will need to contact their organization’s help desk to be unlocked. Once unlocked, they will have three days to register before being locked out again.
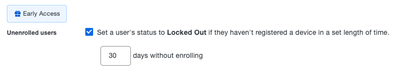 The option to set user status to locked out if they haven't registered a device in a set length of time
The option to set user status to locked out if they haven't registered a device in a set length of time
Temporarily disable user access through Duo Trust Monitor
- Administrators for Duo Advantage and Duo Premier accounts can now lock out users with suspicious activity through Trust Monitor > Security Events in the Duo Admin Panel.
- Selecting the button Lock out user on the user’s security event will temporarily disable user access; Admins can unlock the user via the user’s page, accessed via the Users section of the Duo Admin Panel.
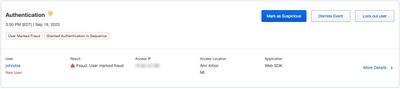 Security event with the new Lock out user button
Security event with the new Lock out user button
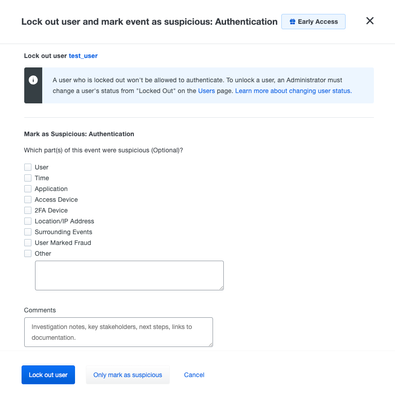 Options to lock out user and mark event as suspicious authentication
Options to lock out user and mark event as suspicious authentication
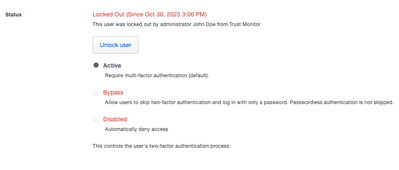 Locked out user status
Locked out user status
Updates to Risk-Based Authentication
- Device distance is a new Risk-Based Factor Selection risk pattern that detects if a user’s authentication device is more than 8,000 miles from their access device location. If this distance is detected, users will be prompted to authenticate with a more secure factor (step-up authentication).
- Improvements to the Authentication Log:
- The Trust Assessment column is now named Risk Assessment.
- The Risk Assessment column will provide additional information on Risk detected and Enforcement, which will highlight the detections triggered at authentication and the expected enforcement because of the detection respectively, when administrators hover their cursor over them.
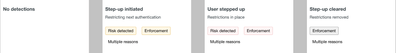 Additional information on Risk detected and Enforcement
Additional information on Risk detected and Enforcement
- Two Risk-Based Remembered Devices (RBRD) changes:
- Session verified replaces Remembered device in the Risk Assessment column and indicates that a user had a valid RBRD session and there were no RBRD risks identified.
- New device session replaces Reauthentication required and indicates that a user either did not have a valid RBRD session or had to authenticated from an anomalous network location.
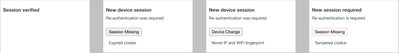 Session verified and New device session in the Risk Assessment column
Session verified and New device session in the Risk Assessment column
- The Authentication Log will now show entries:
- When a user is asked to authenticate with a more secure factor for the first time
- If a user still has a status that requires step-up authentication
- When a user asked for step-up authentication returns to their normal status
- When there are no detections
New and updated applications
Four new named SAML applications with Duo SSO
- There are now named SAML applications to protect Amazon Managed Grafana (note: does not support IdP authentication flow), Amazon Redshift, Productboard and YubiEnterprise Delivery with Duo SSO, our cloud identity provider.
- Reminder: Duo Access Gateway reached the last date of support on October 26, 2023. The new DAG end-of-life date will be March 30, 2024. Please see the Guide to Duo Access Gateway end of life for more details.
Duo Desktop macOS public beta version 6.1.1.0 released
- Fixed an issue that would prevent the app from automatically launching after being updated or when logging in.
- Significantly improved the performance of certain security agent checks.
Duo Desktop Windows 10 and 11 version 6.1.0 released
- Updating to this release enables the automatic launch setting for all users regardless of the previous state of the setting. This resolves an issue where the setting became disabled in Duo Desktop 6.0.0. Users who had previously disabled this setting and wish to keep it disabled will need to go into Duo Desktop's preferences and disable it again.
Duo Desktop Windows public beta version 6.1.1 released
- Fixed an issue that would cause automatic updates to the app to get delayed if the system was in sleep or hibernate mode.
Duo Mobile for Android version 4.54.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
Duo Mobile for iOS version 4.54.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
11/28: revised "Expanded support for cross-browser and cross-device passkeys" bullet to provide more clarity.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: