- Cisco Community
- Technology and Support
- Security
- Email Security
- Hello Sergio, I apologise if
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How can I track the IP address of a sender? (ESA C160)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2015 07:43 AM
I am unable to recevie emails from the domain vigarza.com, and the sender receives this message:
554 Your access to this mail system has been rejected due to the sending MTA's poor reputation. If you believe that this failure is in error, please contact the intended recipient via alternate means.
When I use the message tracking, I have no record of this email; thats probably because it is blocked before smtp protocol starts, just in the tcp connection.
How can I track the IP address of the sender, in order to except it from the reputation filter?
Which look should I look for?
Thanks!!
Sergio
- Labels:
-
Email Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2015 08:01 AM
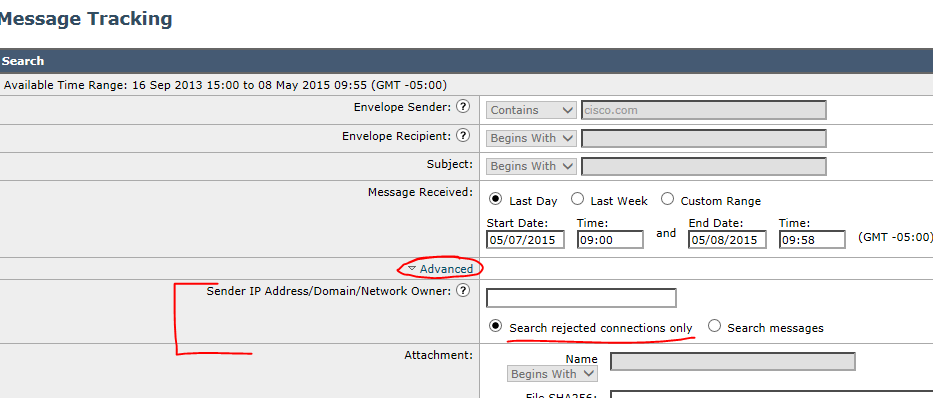
In the gui, go to Monitor/Message tracking.
Click on Advanced, enter the domain, and select "Search rejected connections only"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2015 06:45 PM
Hello Sergio,
I apologise if this update is late.
To further assist with capturing the IP of the rejected server as well, if you have not enabled tracking of rejected connections (it's disabled by default in GUI > Security Services > Message Tracking)
You can go through your mail_logs or historical message tracking when this domain was able to connect through.
See : (mail2world.com as an example)
- Date Time Info: MID XXXXX ICID XXXXX From: test@mail2world.com
- Date Time Info: MID XXXXX ICID XXXXX To: test@mail2world.com
- Date Time Info: New ICID XXXXXXX to Management(IP) from X.X.X.X connecting host reverse DNS hostname: smtp1.mail2world.com -- this followed by some further details
here you will add the connecting IP or their connecting reverse DNS hostname, for mail2world.com all their mail servers are similar pattern of smtp1.mail2world.com or mx1.mail2world.com so to allow all mail servers, use the name “.mail2world.com” the dot in the front to allow any other variable infront, then please go forward and commit this change and you will see their connections allowed.
This comes down to the connecting host’s ability to stop the source of spam exiting their IP, they will need to ensure their network and mail security is resolved and the spammer stopped.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



