- Cisco Community
- Technology and Support
- Security
- Email Security
- Hi Nasir,Thanks for your
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ironport recipient validation without LDAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2015 11:07 PM
Hi Everyone,
We are used already smarthost using QMAIL Program on linux in our environment. Now we are planing to replace a our smarthost to ironport.
We are previously incoming mail user validation using email address. If the email address not present in our valid recipient file the qmail program bounce the incoming mail.
Please advise us we can use the same validation future in ironport like qmail program.
Note : We are not planned the validation using LDAP.
Also please provide your suggestion for the incoming mail recipient validation possibles steps in ironport.
Thanks in advance..
- Labels:
-
Email Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2015 12:10 AM
Procedure Step 1:
2. Click Add Profile.
3. Enter the settings for the profile. For more information, see SMTP Call-Ahead Server Profile Settings in user guide. GUI -> Help and Support -> Online help
4. Configure the advanced settings for the profile. For more information, see SMTP Call-Ahead Server Profile Advanced Settings in user guide.
5. Submit and commit your changes.
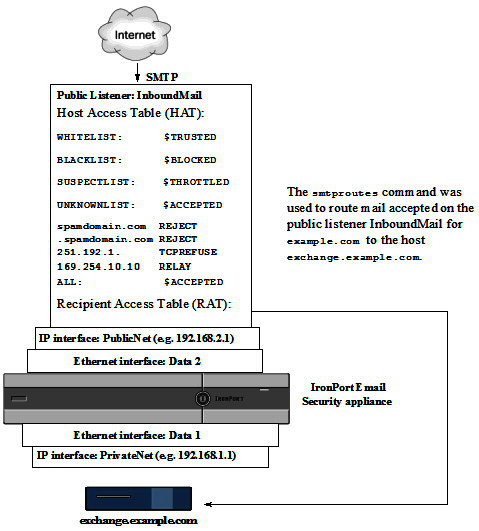
Enabling a Listener to Validate Incoming Mail Via the SMTP Server
Once you create the SMTP Call-Ahead Server Profile, you need to enable it on a listener to allow the listener to validate incoming mail via the SMTP server. SMTP call-ahead functionality is only available on public listeners, as recipient validation is not necessary for private listeners.
Procedure Step2 :
1. Go to Network > Listeners.
2. Click the name of the listener where you want to enable SMTP call-ahead functionality.
3. In the SMTP Call Ahead Profile field, select the SMTP Call-Ahead profile you want to enable.
4. Submit and commit your changes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2015 12:47 AM
Hi Nasir,
Thanks for your reply nasir.
Current MTA(QMail) is not validate from LDAP or SMTP server it have one validation file if the user email address is available in the validation file it accept otherwise it wont accept the incoming mail.
The same we except, we thought the same options will achieve using the incoming mail policy in ironport but we checked the test environment using ironport it accept and forward to exchange server if the email address not present in the incoming policy.
Better understanding i will explain my testing environment.
1. I have created incoming policy name test.

2. Inside the test policy i have mentioned my testing email id.

3. This is my test policy. I am except the external mail will only receive the particular mail id. Other mail will bounce to the sender. But i am facing the issue the another user not in the validation but the user also recive the mail and i have track the message detail it will accept using Default_Policy

Kindly advice us to any other configuration i have to done for that my query.
Thanks in advance..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2015 04:44 AM
Other people still get mail because the test policy doesnt apply to them so they go through the Default policy.
for what youre trying to do, look at content filters and message filters.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2015 02:18 AM
Hello Arumuga,
I am sorry, but on the ESA we have nothing like the validation file you have with the Qmail server.
There are different ways to implement a way how the Appliance only accept messages for incoming recipients.
One option is to use the SMTP Call-Ahead feature which checks the recipient with the internal SMTP Server and only accept the recipient email address if the internal smtp server would also accept them. If not, the recipient get rejected.
The second option is to use the Recipient Address Table (RAT) and insert each single email address instead of the complete domain. With this the Appliance also only accept incoming messages for the existing recipients. But with a higher number of internal email addresses, the list can get to long and performance issues could happen. Further this is not a good option as it is hard to support.
The third option is to use the Incoming Mail Policies in combination with Content Filters. Creating one Incoming Mail Policy for the existing Users and on the default Policy insert a Content Filter which bounce back the messages for all other recipients which are not within the relevant Incoming Mail Policy. This option are not preferred from my side, because this means the Appliance accept all messages and bounce back them afterwards during the mail processing in work queue. This could also cause that your Appliance bounce back the message to a different SMTP Server if a remote side has spoofed their sender email address.
The last option is to use LDAP for the recipient validation during the receiving of new messages.
If LDAP are not a option for you, you should take a look on the SMTP Call-Ahead option Nasir has explained as this will make sure that your Appliance only accept messages for existing internal email addresses and all other get bounced on the remote smtp server which connect to your Appliance.
Best regards,
Mark.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

