- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Re: AMSI Deleted for Windows Defender/Security
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2023 01:55 PM
We've had a handful of machines get flagged for the AMSI provider being deleted from the registry, and haven't been able to put a finger on the cause. The registry key being deleted looks like it's the one for Windows' built-in AV ( {2781761E-28E0-4109-99FE-B9D127C57AFE} ). All the flagged machines have their AMSI keys pointing set correctly for Secure Endpoint, and testing of uninstalling Secure Endpoint to go back to Windows Security has had the deleted key (listed above) be restored, and then get replaced once Secure Endpoint is reinstalled.
All the detected machines have had their connector versions upgraded recently, but for some the AMSI key deletion was detected within minutes of the upgrade, while several hours pass on other machines before getting flagged.
All scans have come back clean, and the vast majority of clients that had their connectors upgraded haven't triggered this, so we're trying to figure out if this is just a bug, or if there's actual suspicious activity going on.
If anyone's run into this before, or has advice for further investigation, it would be much appreciated.
Solved! Go to Solution.
- Labels:
-
AMP for Endpoints
-
Endpoint Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 09:32 AM
TAC response
"We have confirmed through Talos that there is a new BP feature introduced which can now delete "Registry" values if a BP Signature with that specific action gets triggered and that is essentially why we see this causing issues only with 8.1.7.
As most of these are actions taken against known and trusted AV solutions, much like in this case “MsMpEng.exe”, we can conclude these are false positives. There is an ongoing investigation with Talos to address these BP Engine false positives but as of right now, the known workaround that has worked for other customers is setting a BP engine exclusion:"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2023 02:18 AM - edited 04-25-2023 08:47 AM
_
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2023 04:06 AM
I put in a TAC case. If anything of value comes back, I will comment back.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 08:47 AM
Still waiting on a TAC response. Not leaving anyone hanging.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 09:32 AM
TAC response
"We have confirmed through Talos that there is a new BP feature introduced which can now delete "Registry" values if a BP Signature with that specific action gets triggered and that is essentially why we see this causing issues only with 8.1.7.
As most of these are actions taken against known and trusted AV solutions, much like in this case “MsMpEng.exe”, we can conclude these are false positives. There is an ongoing investigation with Talos to address these BP Engine false positives but as of right now, the known workaround that has worked for other customers is setting a BP engine exclusion:"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 09:44 AM
Thanks for checking this out and providing the information, it's much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 09:52 AM
If you want, email me for the future - ventaran@uhnj.org or anyone who uses AMP and updates regularly. It would be great to have a group of folks who use the tool we can bounce issues/ideas off of.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2023 12:05 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 06:14 AM
Hello, thanks for sharing this. But i still don't know how to set up this "BP engine exclusion" Can someone help with this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 07:13 AM - edited 05-22-2023 07:14 AM
Hi,
As you already know the MsMPEng is a defender, and it is a trusted application the reasoning why this is getting triggered is because defender is modifying its registry keys and that is being flagged by the BP engine as potential thread.
You can do two things here:
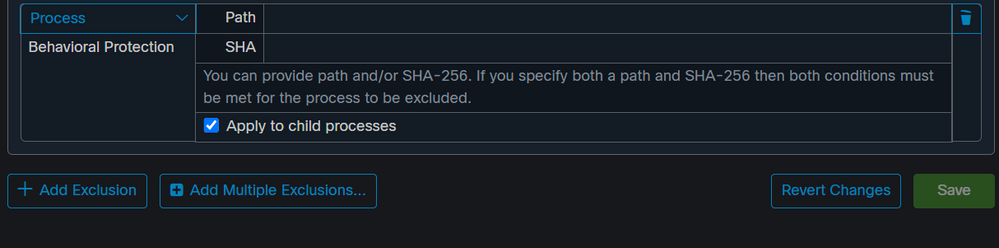
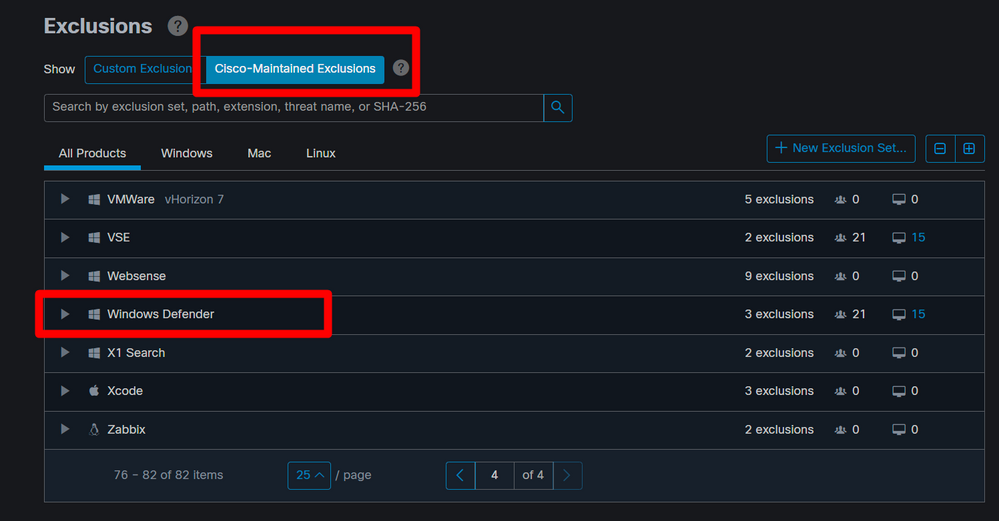
#1: You can add an custom exclusion for this. This will be done under exclusion there is an option to select Engine option where you should select Behavior Protection and chose either SHA256 or Path. Also verify that Cisco Maintained exclusions are in place as well
#2: Ensure that the APDE signature is up to date.
Hope this helped...
Regards,
Roman
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide