- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Cisco Endpoint Security Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2021 04:03 PM
Hello,
Is there a way to check what happened to the malicious file when Cisco Endpoint Security detects a threat and generate an even.
When I enter the Sha-256 hash I can see other information but not what happened? For example: Threat detected and file was quarantined or file deleted.
Thanks & Regards,
Sam
Solved! Go to Solution.
- Labels:
-
AMP for Endpoints
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2021 04:36 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 04:17 AM
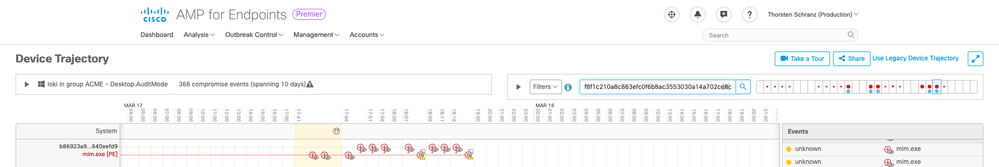
Hello @IamSamSaul, as @Ken Stieers already explained.
When checking the Event, you just need to open the Device Trajectory. In the example from the attached screenshot, i also filtered for the SHA256 hash of the malicious file.
Greetings,
Thorsten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2021 04:36 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 04:17 AM
Hello @IamSamSaul, as @Ken Stieers already explained.
When checking the Event, you just need to open the Device Trajectory. In the example from the attached screenshot, i also filtered for the SHA256 hash of the malicious file.
Greetings,
Thorsten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2021 07:56 AM
Thanks both Ken and Thorsten.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide