- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Re: Dynamic address inspection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2021 10:30 PM
Hi everyone I'm trying to understand the "DAI" dynamic address inspection. The first functions of the DAI I understood those that make a check with the help of the dhcp spooning. Right after she says: """"DAI can be configured to check for both destination or source MAC and IP addresses: Destination MAC – Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body. Source MAC – Checks the source MAC address in the Ethernet header against the sender MAC address in the ARP body. IP address – Checks the ARP body for invalid and unexpected IP addresses including addresses 0.0.0.0, 255.255.255.255, and all IP multicast addresses."""" When would a hacker change the target mac address in the body arp to launch an attack? There is no example of this: I only thought about this scenario in the case of the destination address. PCB (hacker) sends an arp reply with header its mac address and in the mac address of the arp body the mac address of another computer. Obviously the example is also valid in the case of modification of the sender. I hope for a good day clarification
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2021 07:22 AM - edited 02-17-2021 01:57 PM
Port A "hacker"
Host mac-A IP-A
Port B
Host mac-B IP-B
Port C
Host mac-C IP-C
ARP request from Host B to Host C
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-B <- ok for DHCP snooping the check is doing by DAI
Sender Mac= mac-B
Sender IP= IP-B
Target Mac = mac-C
Target IP= IP-C
ARP reply
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-C <- ok for DHCP snooping the check is doing by DAI
*Sender Mac= mac-C
*Sender IP= IP-C
*Target Mac = mac-B
*Target IP= IP-B
*note the the MAC/IP is flap for ARP reply
NOW what if Host A reply ??
ARP reply
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-A <- ok for DHCP snooping the check is doing by DAI
Sender Mac= mac-A
Sender IP= IP-C
Target Mac = mac-B
Target IP= IP-B
this make
Host B use mac-A instead of mac-C for sending frame. and hence hack....
using DAI validate option
ARP reply
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-A <- ok for DHCP snooping the check is doing by DAI
Sender Mac= mac-A
Sender IP= IP-C<- not OK for DHCP snooping & DAI because the IP-C not map to mac-A
Target Mac = mac-B
Target IP= IP-B
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2021 03:03 AM
DAI is used to block ARP spoofing. The attacker can send unsolicited ARP
message to the switch to update the entry in ARP table pointing to his
machine, i.e. change the ARP mapping from victim IP-MAC to attacker IP-MAC.
The IP address is same but the MAC changes. The switch will accept this and
start forwarding the traffic to attacker. The attacker will act as man in
the middle by getting copy of the traffic and pass it to victim.
DAI will inspect ARP requests and only allows them if there is no valid
entry in DHCP snooping DB. If there is a valid DHCP snooping entry it will
drop the ARP message because the client is still active on that IP address.
It will only accept ARP changes on that IP if the DHCP snooping entry is
cleared.
***** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2021 03:40 AM
Hi Mohammed thank for your answer. I understand DAI function when interfacing with dhcp snooping. """"DAI can be configured to check for both destination or source MAC and IP addresses: Destination MAC – Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body. Source MAC – Checks the source MAC address in the Ethernet header against the sender MAC address in the ARP body. IP address – Checks the ARP body for invalid and unexpected IP addresses including addresses 0.0.0.0, 255.255.255.255, and all IP multicast addresses."""" I didn't understand when it says that it checks the mac address in the header with the mac address in the arp body; it's a different case
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2021 04:41 AM
I got the question now. Yes, this is another option in DAI to validate the
actual MAC address in L2 header (source or destination) against the address
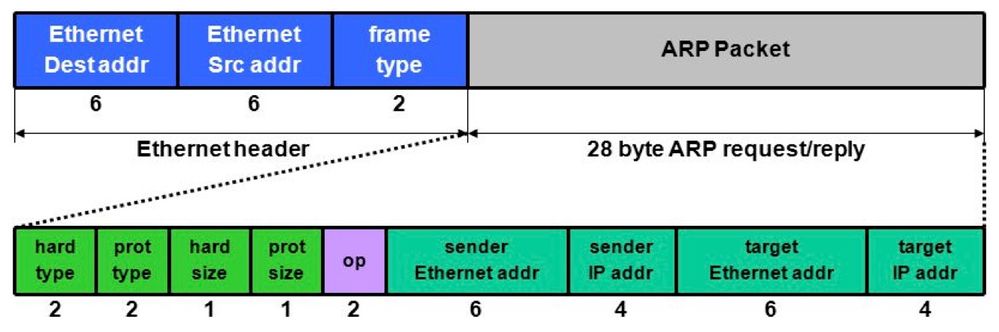
listed in the ARP payload. If you look at the ARP message structure below,
you will notice that ARP payload will have the L2 addresses for sender and
receiver. If the attacker sends an ARP message to the switch/router to
update ARP table, the switch will validate the MAC address of the attacker
in his frame against the MAC address in the payload. This should mismatch
because the MAC of attacker will be different from the MAC of the victim
which is in the payload.
[image: image.png]
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2021 04:00 PM
One example
Server with IP-A Mac-A
Host
hacker with IP-B Mac-B
all request dhcp and they all have entry in dhcp snooping table,
Now
hacker will send GARP with
source is Mac-B
target Mac is Mac-B
target IP is IP-A
this make all host instead of send the packet to Server it will send it to hacker using the Mac-B.
this is why DAI using validation option to stop suck as this attack.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2021 01:38 AM
This answer applies to both of you who have spoken and thank you. In other words, if there is dhcp snooping, the switch will check the mac address - ip address association. But in the case of "" Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body. "" for example what happens? In a regular scenario: pc-A sends arp request with header its mac address and mac address fffffffffff. In the arp-body of pc-A mac address sender + ip address of pc-A and ip address of pc-C (which is the recipient of which we have his mac address.) Pc-c reply with its mac address. Now let's assume pc-B intrudes into communication. What does he do? How does it change the payload? In the case of dhcp snooping ok it is clear that the switch checks in the payload the association between ip address and mac address that correspond in the database. Then it looks in the payload and sees that pc-C's ip address doesn't match the right mac address. Now same scenario without dhcp snooping but with "" Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body. "" We have the hacker's arp reply which looks like this: Hacker: header sender mac address PC-B and destination mac address PC-A. In the payload we have: IP address of PC-C and the destination mac-address of PC-B. So when it says: "" Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body. "" That is, it does not have to coincide what sense it has that it coincides it is normal that the destination mac address will be different from pc-A and the destination mac address in the payload will be that of pc-B ie of the hacker. Here's why I don't find myself with this definition: ""Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body. ""
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2021 07:22 AM - edited 02-17-2021 01:57 PM
Port A "hacker"
Host mac-A IP-A
Port B
Host mac-B IP-B
Port C
Host mac-C IP-C
ARP request from Host B to Host C
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-B <- ok for DHCP snooping the check is doing by DAI
Sender Mac= mac-B
Sender IP= IP-B
Target Mac = mac-C
Target IP= IP-C
ARP reply
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-C <- ok for DHCP snooping the check is doing by DAI
*Sender Mac= mac-C
*Sender IP= IP-C
*Target Mac = mac-B
*Target IP= IP-B
*note the the MAC/IP is flap for ARP reply
NOW what if Host A reply ??
ARP reply
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-A <- ok for DHCP snooping the check is doing by DAI
Sender Mac= mac-A
Sender IP= IP-C
Target Mac = mac-B
Target IP= IP-B
this make
Host B use mac-A instead of mac-C for sending frame. and hence hack....
using DAI validate option
ARP reply
Ether Des.= ffff:ffff:ffff
Ether Scr.= mac-A <- ok for DHCP snooping the check is doing by DAI
Sender Mac= mac-A
Sender IP= IP-C<- not OK for DHCP snooping & DAI because the IP-C not map to mac-A
Target Mac = mac-B
Target IP= IP-B
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2021 10:32 PM
This Is not clear you said:
"this make
Host B use mac-A instead of mac-B for sending frame. and hence hack....
using DAI validate option"
I think you wanted said: Host B use mac- A instead of Mac-C not Mac-B right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2021 01:56 PM
Yes you are right,
thanks for correct me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2021 01:29 AM
I think I understand, however, what sense does it make for a hacker what sense does it have to change the target address in the payload due to a mismatch between the mac address in the header (sent by the hacker) and the target mac address in the payload. Again in the example: This is clear: Because the hacker makes the traffic arrive on his mac address. """"""""Ether Des.= ffff:ffff:ffff Ether Scr.= mac-A <- ok for DHCP snooping the check is doing by DAI Sender Mac= mac-A Sender IP= IP-C<- not OK for DHCP snooping & DAI because the IP-C not map to mac-A Target Mac = mac-B Target IP= IP-B"""""""" mismatch between sender and sender in the payload body. But if we have this: """"""""Ether Des.= MAC-A (let's assume the hacker wants to attack only A's pc, not all) Ether Scr.= mac-A <- ok for DHCP snooping the check is doing by DAI Sender Mac= mac-A Sender IP= IP-C Target Mac = mac-C ( i.e. the change is made here by the hacker modifying the target in the payload with for example C instead of what should have been C.) Target IP= IP-B"""""""" So if checking for the mismatch between mac sender and mac sender makes sense because the hacker directs traffic to his computer. While in my opinion it makes no sense to change the destination mac other than that of the target destination. in your opinion what sense does it make? If you were the hacker in short
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2021 09:32 AM
In my opinion it is wrong; the basic functionality of the DAI does not check this string "Ether Scr. = mac-B <- ok for DHCP snooping the check is doing by DAI". Check the contents of the arp then in this situation:
ARP request:
Ether Des. = Ffff: ffff: ffff
Ether Scr. = Mac-B by DAI
Mac Sender = mac-B
Sender IP = IP-B
Target Mac = mac-C
Target IP = IP-C
Check sender mac + sender ip and target mac and target ip (even if you made a mistake here too, that is if you send an arp request you don't know the Target mac yet in this case the mac taget is 000000000000) However taken for granted, dai in its basic functionality controls the sender mac and sender ip and taget mac and target ip associations. The DAI check is not done on the frame header but in the content of the arp. When it says: "Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body", returning to the example a check is made between the destination mac address of the header with the Target mac inside the arp payload even if it must be added that the option mac address header mac address in the body of the arp must be done only in the arp reply not in the arp request. Checking with the src-mac option instead checks both requests and replicas. These additional options are made to prevent the host receiving the invalid frame from processing and discarding the request but there is no actual attack. Let me explain better: We have host a with mac-a (Hacker) and host b with mac b;
host A generates a frame with mac other than its own:
"mac - d" mac address header source mac:
mac- z source ip: ip-z target ip: example 192.168.1.10
mac target: unknown
mac address destination header: FFFFFFFFFFF
Replication of the 192.168.1.10 Host C:
What does Host C do? He sees a frame arrive (like everyone on the broadcast network) but host C removes the frame headers, looks at the arp request and sees that for him the request was made by "mac-z" and not "mac-d"
Then it creates the replica and sends it to "mac-z":
mac source header: "mac-c"
mac sender: mac-c
sender-ip: 192.168.1.10
Target ip: ip-z
Target mac: "mac-z"
mac destination header: "mac-z" (and not mac-d)
This is just an invalid replica and not a threat.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2021 10:02 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2021 11:16 AM
Let us try to clarify perhaps we say two things that are the same but in a different way; Then by default without configuring additional DAI options src-mac dest-mac and ip, without configuring these three options in default DAI configuration conditions, the DAI via dhcp snooping checks the ip mac associations that are inside the arp body then sender ip sender mac target ip target mac It does not check the source and destination mac address of the header. So if you don't configure those three options above I mentioned, an attacker can bypass basic DAI checks by changing the mac address in the sender and recipient header. These three options allow hosts to avoid unnecessarily processing frames which they will then discard and therefore invalid arp requests are defined, while the default configuration of the DAI is the one that gives you specific control to avoid attacks such as man in the middle.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide