- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Re: need to block exe file
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 09:38 AM
Hi All,
Need to block below exe file path on server. Can anyone help me how can i do this in Cisco secure endpoint console.
c:\program files\uvnc bvba\UltraVNC\winvnc.exe
Solved! Go to Solution.
- Labels:
-
AMP for Endpoints
-
Endpoint Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2024 08:28 AM
Not sure If I follow. If you want to block that particular file winvnc.exe you will need to either grab that file and upload to Blocked Application or determine/calculate the SH256 of that file and add that hash instead once you add that apply the Block Application list to the policy for that server to block running that EXE again.
Or do what Marvin suggested with Simple Custom Detection, you will also need to apply that to your policy for that server, then run full or partial scan which will remove the file all together upon detection.
Both solution works based on SHA256. However you need to remember that if the SHA256 will change lets say with new version you will need to adjust that policy again .
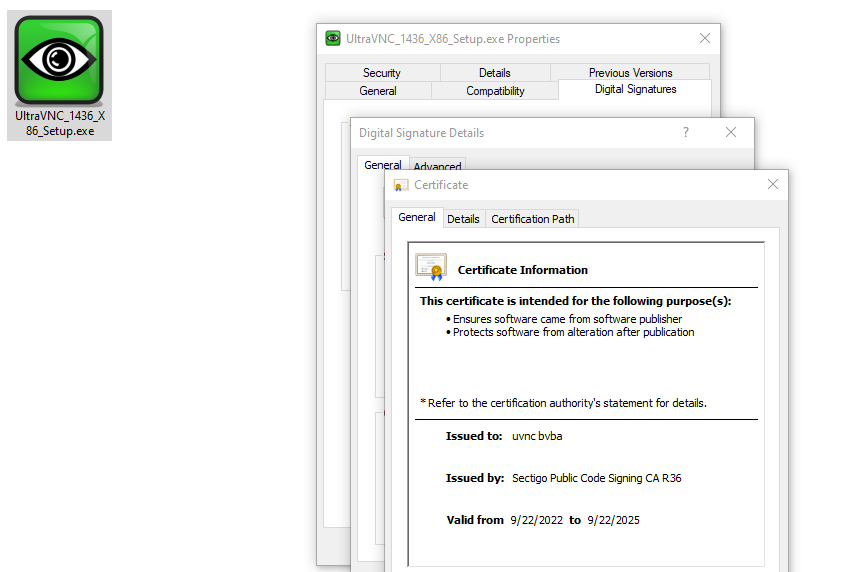
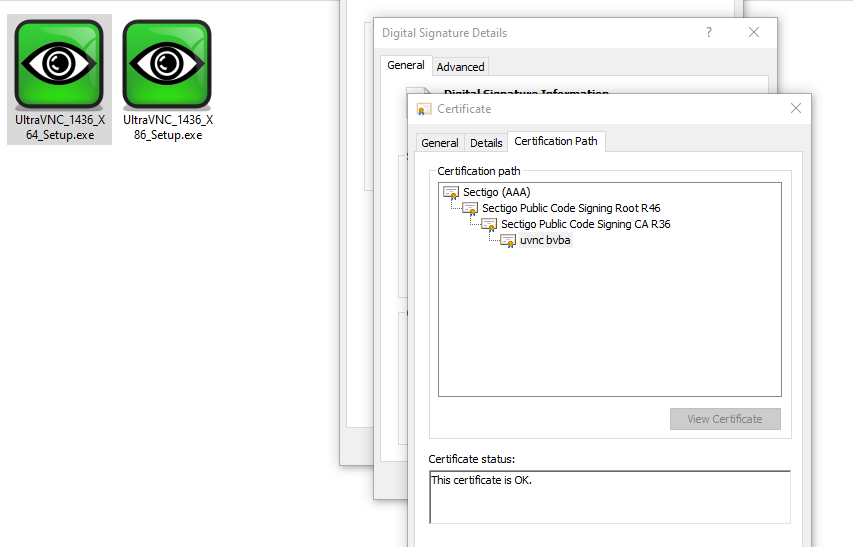
Unfortunately UltraVNC is not consider to be threat its just free software that can display screen of another computer (via the internet or network) on your own screen. In your case its unwanted software but for others they might use it in their environment. Also using valid certificates for the installer makes harder to deemed the file malicious. The latest UltraVNC looks like this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 09:45 AM
Use a Simple Custom Detection (SCD).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 12:23 PM - edited 04-17-2024 12:24 PM
You can also create your own list under Outbreak Control ---> Application Control - Blocked Applications then apply that list to your policy. This will only work on *.EXE files and it will block that application from running.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 11:14 PM
Hi Roman,
Using upload file search only for that machine, but i want to block exe file that resides in server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2024 08:28 AM
Not sure If I follow. If you want to block that particular file winvnc.exe you will need to either grab that file and upload to Blocked Application or determine/calculate the SH256 of that file and add that hash instead once you add that apply the Block Application list to the policy for that server to block running that EXE again.
Or do what Marvin suggested with Simple Custom Detection, you will also need to apply that to your policy for that server, then run full or partial scan which will remove the file all together upon detection.
Both solution works based on SHA256. However you need to remember that if the SHA256 will change lets say with new version you will need to adjust that policy again .
Unfortunately UltraVNC is not consider to be threat its just free software that can display screen of another computer (via the internet or network) on your own screen. In your case its unwanted software but for others they might use it in their environment. Also using valid certificates for the installer makes harder to deemed the file malicious. The latest UltraVNC looks like this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2025 01:56 AM
Hi @Vishal6 Could you please share more details about how you accomplished this? Like you did this exactly?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide