- Cisco Community
- Technology and Support
- Security
- Network Security
- CIsco ASA REST API HELP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CIsco ASA REST API HELP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2018 06:09 AM - edited 02-21-2020 07:06 AM
Hi, everybody.
I'm trying to perform sync of ACL configuration from one ASA to another.
Both devices have the same version of OS and REST-API
On source ASA I have this ACL:
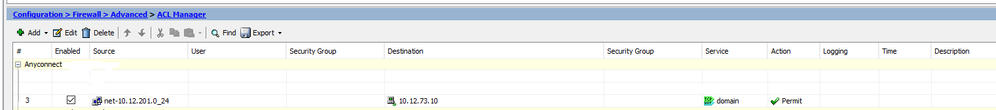
Using REST API, I get ACEs from ACL and trying to create them on target device.
To do that i'm using python.
And when I trying to POST (using REST API) third rule (see screenshot above) on target device
url = 'https://192.168.1.1/api/objects/extendedacls/Anyconnect/aces'
rule_json = {'kind':'object#ExtendedACE','ruleLogging':{'logStatus':'Default','logInterval':300},'isAccessRule':False,'destinationAddress': {'kind':'IPv4Address','value':'10.12.73.10'},'remarks':[],'destinationService':{'kind':'TcpUdpService','value':'tcp-udp/domain'},'permit': True,'active': True,'position': 3,'sourceAddress': {'kind':'objectRef#NetworkObj','objectId':'net-10.12.201.0_24'}}
requests.post(url, data=json.dumps(rule_json), headers=self.HEADERS, auth=self.cred, verify=self.verify_cert, timeout=self.timeout)
I getting this error
[
{'code': '',
'details': "\naccess-list Anyconnect line 3 extended permit tcp-udp object net-10.12.201.0_24 host 10.12.73.10 eq domain \n\nERROR: % Invalid input detected at '^' marker.\n",
'level': u'Error'}
]
So, as I understand - when ASA receive REST API POST REQUEST: behind the scenes executed CLI command, but in this case there is error because you can not use "tcp-udp" protocol in ACE statement.
So, my question is: is this bug or feature?
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2018 11:39 PM - edited 01-10-2018 03:27 AM
ADDITIONAL INFORMATION FOR QUESTION
1) When I get ACE using REST API (via Python) JSON-structure of ACE looks like following way:
{
'sourceService': {'kind': 'NetworkProtocol', 'value': 'tcp-udp'},
'kind': 'object#ExtendedACE',
'objectId': '2143418028',
'ruleLogging': {'logStatus': 'Default', 'logInterval': 300},
'isAccessRule': False,
'destinationAddress': {u'kind': u'IPv4Address', u'value': u'10.12.73.10'},
'remarks': [],
'destinationService': {u'kind': u'TcpUdpService', u'value': u'tcp-udp/domain'},
'permit': True,
'active': True,
'position': 3,
'sourceAddress': {u'kind': u'objectRef#NetworkObj', u'objectId': u'net-10.12.201.0_24'},
'selfLink': u'https://192.168.51.254/api/objects/extendedacls/Anyconnect/aces/2143418028'
}
2) After some manipulations I prepare following JSON-structure for POSTing to another device:
{
'sourceService': {'kind': 'NetworkProtocol', 'value': 'tcp-udp'},
'destinationAddress': {'kind': 'IPv4Address', 'value': '10.12.73.10'},
'destinationService': {'kind': 'TcpUdpService', 'value': 'tcp-udp/domain'},
'ruleLogging': {'logStatus': 'Default', 'logInterval': 100},
'permit': True,
'remarks': [],
'position': 3,
'sourceAddress': {'kind': 'objectRef#NetworkObj', 'objectId': 'net-10.12.201.0_24'},
'active': True
}
3) After posting JSON-structure to destination device, I'm getting following error:
{
'code': '',
'details': "\naccess-list Anyconnect line 1 extended permit tcp-udp object net-10.12.201.0_24 ^host 10.12.73.10 eq domain \n\nERROR: % Invalid input detected at '^' marker.\n",
'level': 'Error'
}
4) After some research I also understand following.
If I use this JSON-structure to create ACE in ACL
{
"sourceAddress": {
"kind":"objectRef#NetworkObj",
"objectId":"net-10.12.201.0_24"
},
"destinationAddress": {
"kind":"IPv4Address",
"value":"10.12.73.10"
},
"destinationService": {
"kind":"TcpUdpService",
"value":"tcp/domain"
},
"ruleLogging": {
"logStatus": "Default",
"logInterval": 100
},
"remarks": [],
"permit": True,
"active": True,
"position": 3,
}
POST request using Python is successfull and in sh running-config there is following ACE
access-list Anyconnect extended permit tcp object net-10.12.201.0_24 host 10.12.73.10 eq domain
If I use this JSON-structure to crete ACE in ACL
{
"sourceAddress": {
"kind":"objectRef#NetworkObj",
"objectId":"net-10.12.201.0_24"
},
"destinationAddress": {
"kind":"IPv4Address",
"value":"10.12.73.10"
},
"destinationService": {
"kind":"TcpUdpService",
"value":"udp/domain"
},
"ruleLogging": {
"logStatus": "Default",
"logInterval": 100
},
"remarks": [],
"permit": True,
"active": True,
"position": 3,
}
POST request using Python is successfull too and in sh running-config there is following ACE
access-list Anyconnect extended permit udp object net-10.12.201.0_24 host 10.12.73.10 eq domain
But if I trying to POST following JSON-structure
{
"sourceAddress": {
"kind":"objectRef#NetworkObj",
"objectId":"net-10.12.201.0_24"
},
"destinationAddress": {
"kind":"IPv4Address",
"value":"10.12.73.10"
},
"destinationService": {
"kind":"TcpUdpService",
"value":"tcp-udp/domain"
},
"ruleLogging": {
"logStatus": "Default",
"logInterval": 100
},
"remarks": [],
"permit": True,
"active": True,
"position": 3,
}
I'm getting error as I wrote earlier.
Based on error detail message, that I receive when performing POST request:
access-list Anyconnect line 1 extended permit tcp-udp object net-10.12.201.0_24 host 10.12.73.10 eq domain \n\nERROR: % Invalid input detected at '^' marker.\n
I can say, that internal REST API logic erroneously trying to use "tcp-udp" as protocol number while creating ACE. And such behavior lead to error.
But I expect that in confuguration I will get this ACE
access-list Abyconnect extended permit object-group TCPUDP object net-10.12.201.0_24 host 10.12.73.10 eq domain
Actually object-group TCPUDP normally created automatically when you create ACE with tcp/udp destination service in ASDM.
Based on this information I making conclusion that something is wrong in Cisco ASA REST API.
May be there is some trick in adding ACE with tcp-udp destination service, but there is no corresponding information in official documantation https://www.cisco.com/c/dam/en/us/td/docs/security/asa/api/asapedia_rest_api_132.pdf
Please, can somebody clarify this problem?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
