- Cisco Community
- Technology and Support
- Security
- Network Access Control
- CRL ISE configuration?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 11:40 PM
I have a root CA in my PKI deployment and a 'normal' CA underneath it which performs the certificate signing. My deployment use a CRL for certificate revocation, my question is do I configure this CRL under root CA or the 'normal' CA within the "Trusted Certificates" ISE menu?
I don't want to double up and configure on both because it will get downloaded twice (inefficient). I was "guessing" that it goes on the root CA certificate in my "Trusted Certificates" section, as that is ultimately at the top (root) of my PKI which signs the client certificates.
Just seeking clarification.
Thanks
DJ
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 11:06 AM
Use the root, reading this doc the CRL is signed by the root
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 09:43 AM
I am thinking the root but I am confirming with folks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 11:06 AM
Use the root, reading this doc the CRL is signed by the root
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 05:04 PM
Thanks Jase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 07:19 PM
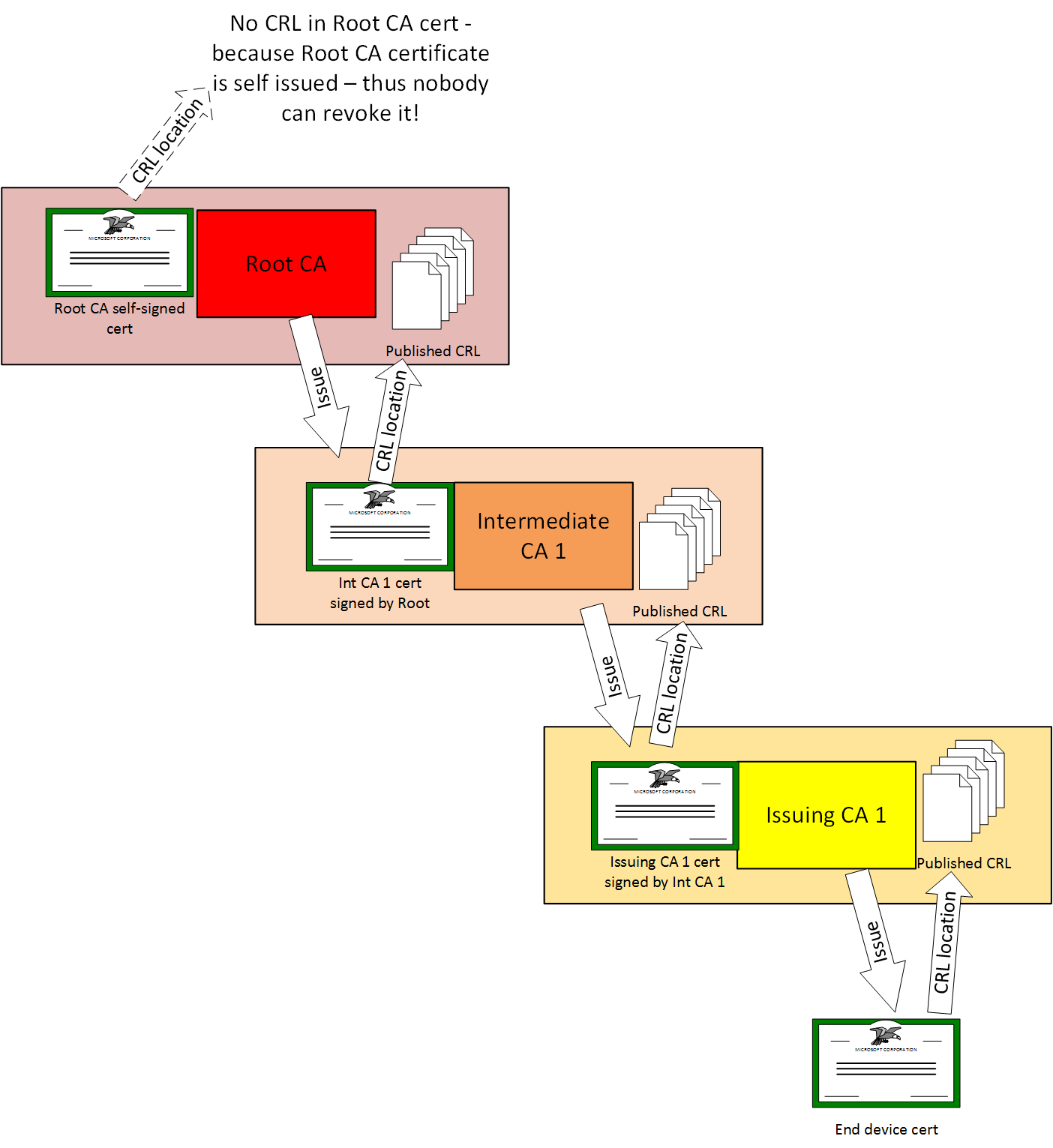
This question used to puzzle me so I drew a little diagram that I can reference to explain it all.
So it makes no sense to check for the revocation of the Root CA cert since nobody can revoke it - this is why you won't configure a CRL setting in ISE for the Root CA cert.
But in ISE you would configure the CRL setting only in the issuing CA cert (in your 2-tier setup) and that CRL points to the Root CA's CRL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 08:19 PM
I guess it comes down to this. The CRL is hosted at http://mycrl. I have a Root CA and an Issuing CA. ISE receives a certificate from the client which has been issued by the Issuing CA. Does ISE use the CRL configured within the Issuing CAs trusted certificate, because that was the CA which signed the client certificate. Or does ISE use the CRL configured within the Root CAs trusted certificate, because that is the 'top' level of trust in my PKI?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 08:44 PM
I would have to setup a two tier CA to see how this pans out in an ISE deployment, but I understand your question.
In your case you will have installed two Trusted CA certificates on your ISE deployment
Root CA cert
Issuing CA cert
Clients out in the field have a cert that was issued by Issuing CA. Clients then try to connect to ISE via EAP-TLS.
When an EAP-TLS request comes into ISE, during TLS setup, ISE will inspect the client cert look up the Issuer of that EAP-TLS client cert. If client cert was issued by Issuing CA, then ISE will try to download the CRL specified by the setting you provided in ISE Trusted Certs for the "Issuing CA cert" - after all, who else would know whether Issuing CA revoked one of its own certs, right? So the URL should be the URL of the Issuing CA.
I don't believe you would configure anything into the Trusted "Root CA cert" CRL field because nobody can provide a CRL for the Root CA cert.
It's confusing for sure. And I apologise if I got it wrong - but I plan to test this out myself just to understand the theory better.
What makes it worse is that ISE does not care about the Client cert's CDP (CRL Distribution Point) attribute, which contains the location of the CRL you want to download. I guess one might argue that the CDP is largely optional and often misconfigured - so having the ISE 'manual CRL method' is more reliable. But in my opinion it could be a tick box to allow some kind of plug and play behaviour.
BTW, ISE also doesn't support delta CRL's - so don't rely on publishing those (your CRL may contain a pointer to a delta CRL - ISE doesn't care about it). It only downloads one CRL per CA.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



