- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.3 as intermediate CA und Microsoft Root CA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 07:08 AM
Hello,
I am trying to Bind CA Signed Certificate to the CSR generated for intermediate CA.
The root ca is a Microsoft Server 2012R2
ISE is Version 2.3
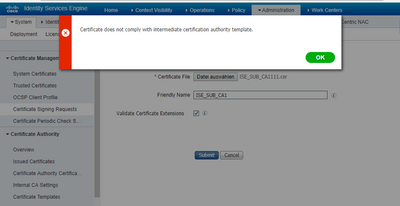
When binding the certificate, i get the following error:
Certificate does not comply with intermediate certification authority template.
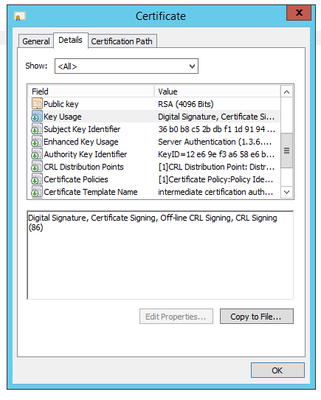
The certficate i am trying to bind, looks fine to me:
Digital Signature, Certificate Signing, Off-line CRL Signing, CRL Signing (86)
Has anyone encountered this issue before?
I'm guessing something is wrong with our Root ca, but who knows.
Any help is appreciated.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 08:04 AM
Also consider do you truly need to add ISE to be part of the PKI? If you’re doing BYOD onboarding using Native supplicant and certificate provisioning then use ISE self contained. It just works out of the box with minor setup ☺
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 07:53 AM
Suggest looking at ise-psc.log. The log should provide information on why the certificate was rejected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 08:09 AM
I can't see your EKU settings. Do you have both client and server authentication enabled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 06:05 AM
Yes, i have both client server authentication enabled.
I searched the ise-psc.log. I can't find anything conclusive, i've attached the log segment from when attempting to bind the certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 01:31 PM
Try bumping up the ca-service log under Administration -> System -> Logging -> Debug Log Configuration to debug and go through bind process again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 01:51 PM
Please see if you are using the right template in the CA to create the certificate.
Here is more information
-
ISE Intermediate CA—(Applicable only for the internal CA service when ISE acts as an intermediate CA of an external PKI) Used to generate an intermediate CA certificate on the Primary PAN and subordinate CA certificates on the PSNs. The certificate template on the signing CA is often called a Subordinate Certificate Authority. This template has the following properties:
-
Basic Constraints: Critical, Is a Certificate Authority
-
Key Usage: Certificate Signing, Digital Signature
-
Extended Key Usage: OCSP Signing (1.3.6.1.5.5.7.3.9)
-
Thanks
Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 07:14 AM
This ist the only useful message i'm getting from the log file, after setting debug condition:
Error occurred while verifying certificates for host: svtg001ise01.tg-cee.net. com.cisco.epm.cert.validator.CertPathVerificationException: Certificate Signature Verification failed
I created a Policy.inf file to generate the certificate, please see attached.
As it is a offline root ca, there are no (visible) certificate templates. The only thing i can influence, is the .inf file.
I have the root ca certificate imported under trusted certificates.
I'm running out of Ideas :-(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 08:04 AM
Also consider do you truly need to add ISE to be part of the PKI? If you’re doing BYOD onboarding using Native supplicant and certificate provisioning then use ISE self contained. It just works out of the box with minor setup ☺
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2019 02:06 PM
Hi,
This was probably already solved for you but if someone else runs into this, make sure to use a SubCa (Subordinate Certification Authority) as the certificate template from Microsoft CA.
In my lab this is what the cert has and it works for ISE's intermediate CA:
EKU
Server Authentication (1.3.6.1.5.5.7.3.1)
Client Authentication (1.3.6.1.5.5.7.3.2)
OCSP Signing (1.3.6.1.5.5.7.3.9)
Key Usage
Digital Signature, Certificate Signing, Off-line CRL Signing, CRL Signing (86)
The template has Basic Constraint as: "The subject is a certification authority (CA)." Critical extension.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide