- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ACL to allow only internet traffic on a subinterface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 02:18 AM
Hello,
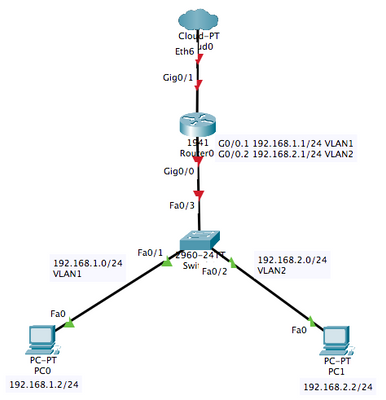
Here's a simple topology:
For the VLAN2, I'd like to allow only internet traffic.
Here's the ACL:
access-list 100 permit tcp 192.168.2.0 0.0.0.255 any eq 80
access-list 100 permit tcp 192.168.2.0 0.0.0.255 any eq 443
access-list 100 permit tcp 192.168.2.0 0.0.0.255 any eq 53
But I'm not sur how to apply it only to the subinterface and if I missed others elements.
Thanks!
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 02:26 AM
On a router, you typically apply ACLs on the L3-interface, that is the interface where your IP-address is configured:
interface gig0/0.2 ip access-group 100 in
And if your intention is to allow DNS, you should also add UDP/53.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 02:26 AM
On a router, you typically apply ACLs on the L3-interface, that is the interface where your IP-address is configured:
interface gig0/0.2 ip access-group 100 in
And if your intention is to allow DNS, you should also add UDP/53.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 02:52 AM
Thank you very much, I understand. Also, should I also apply this ACL on the gig0/1 for security (so only internet traffic is allow to 'enter')? You confirme me that there is an implicit deny all clause at the end of every ACL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 03:27 AM - edited 06-12-2021 03:32 AM
Putting an ACL on the internet-facing interface is best practice but slightly more difficult as you need to allow the return traffic. Or you configure a stateful firewall on the router. If you are on the beginning of your learning, that is probably for a later chapter.
And yes, all the ACLs have an implicit "deny any".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 03:31 AM
Thank you. If you have any online resources on this subject I'm interested.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 03:36 AM
I would buy a CCNA study guide and go through that. That are the basics that any Cisco technician needs to have.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide