- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ACS 5.2 - Authenticating user 802.1x and MSCHAPv2 using Identity
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2011 10:47 AM - edited 03-10-2019 06:25 PM
Hi Community,
I'm using the ACS 5.2 as the solution of authentication in my network. I configured both situations: Access Policies with Network Access and with Device Administration.
At this moment, I have some devices configured: 1 ASA (using RADIUS), 1 WLC-5508 (using RADIUS), 1 2960S (using TACACS+). And I have configured a External Identity Store, using LDAP (I can see and select all groups without problem).
Everything is working fine. My next step was configure users to use 802.1x to authenticate using ACS with my LDAP database.
Assuming all configurations are correct on all computers (when I use a Internal database works fine), these are the following logs/configurations in the ACS:
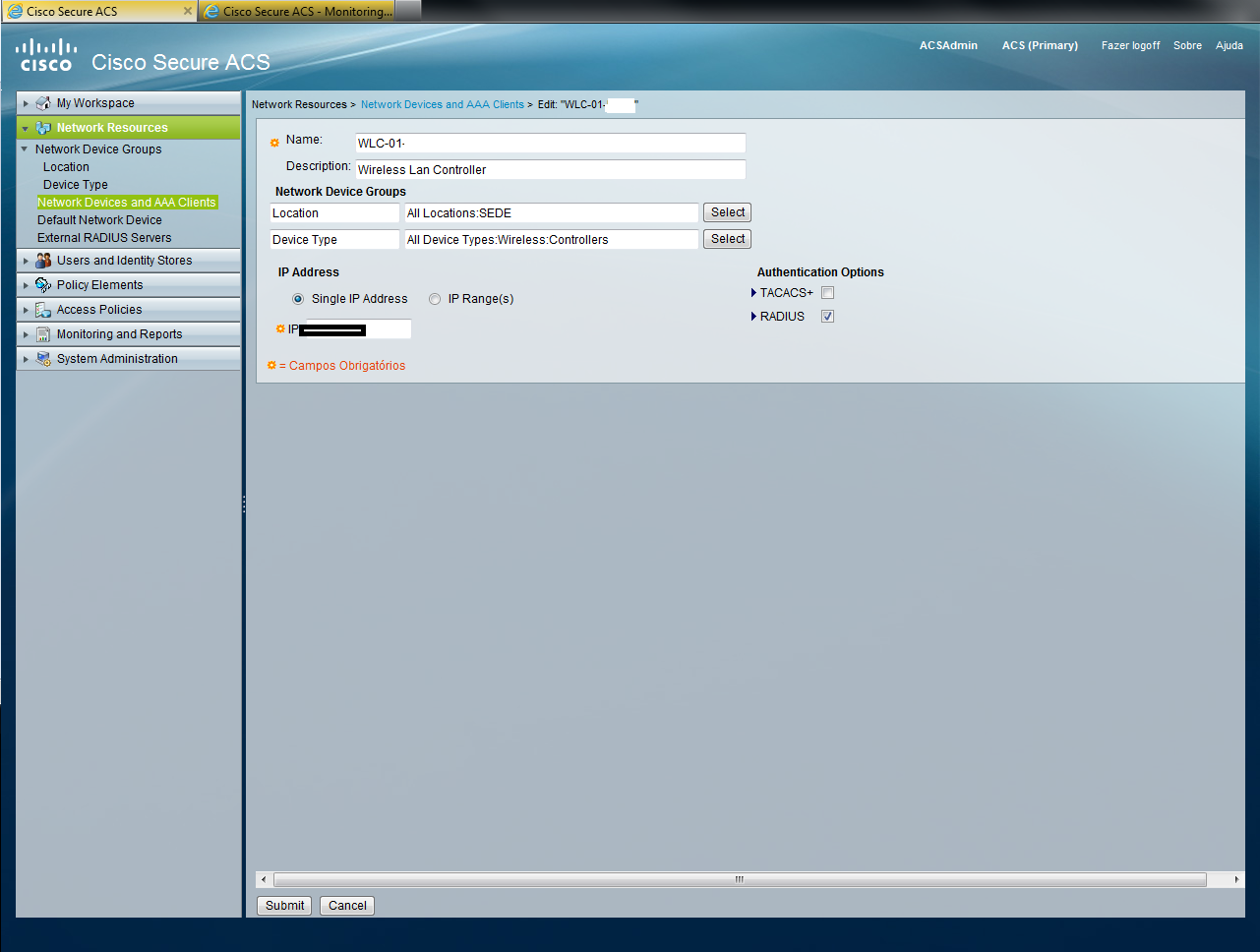
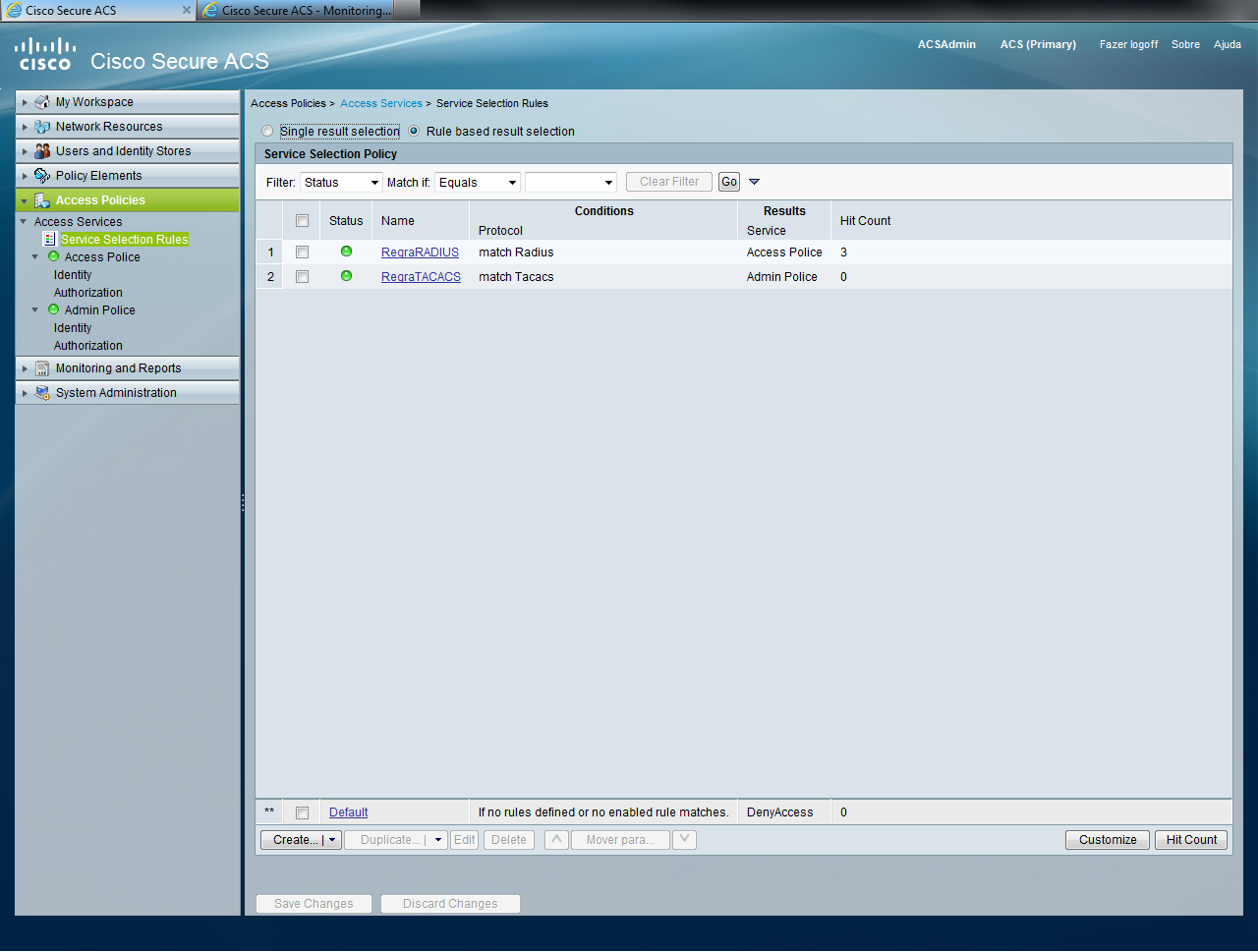
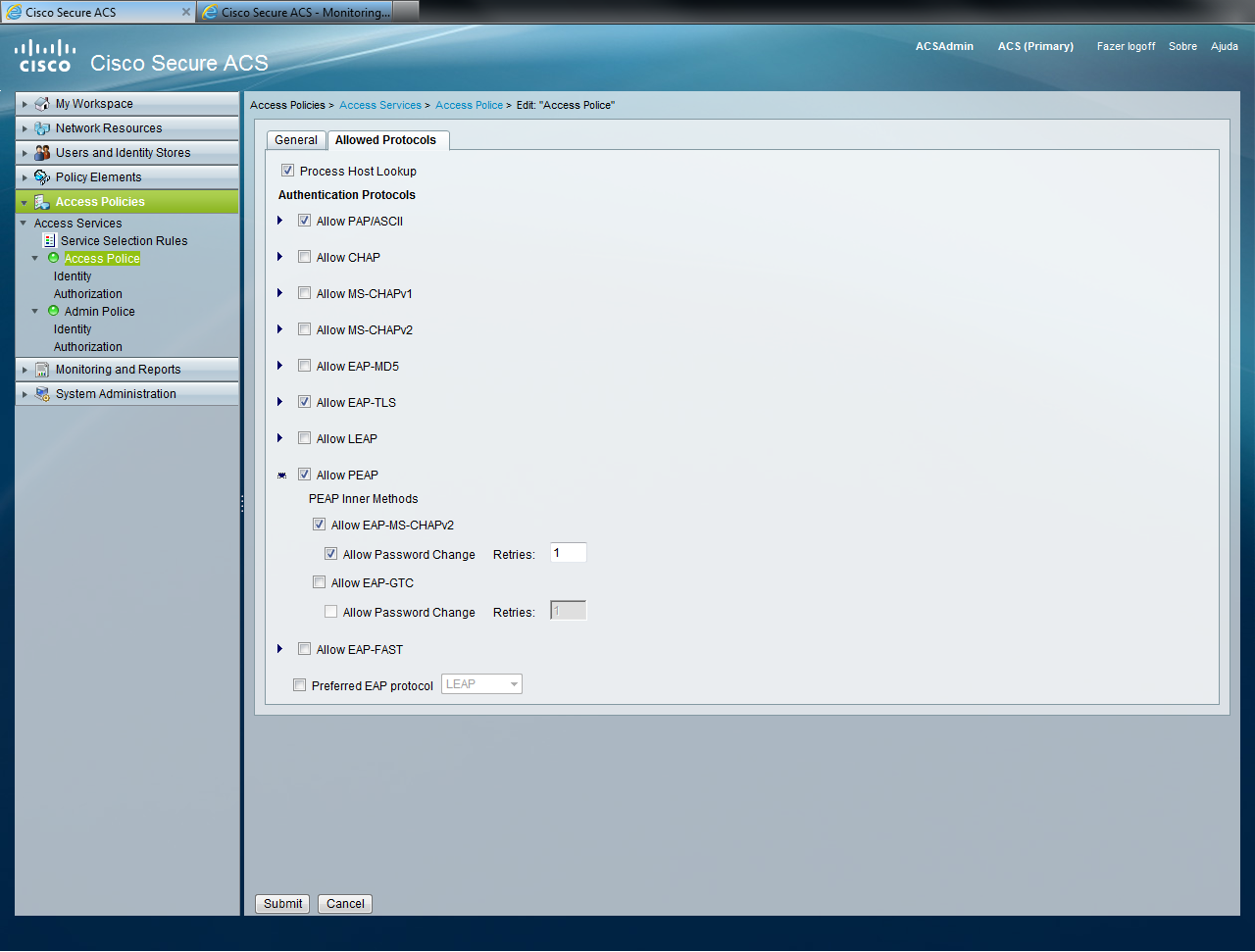
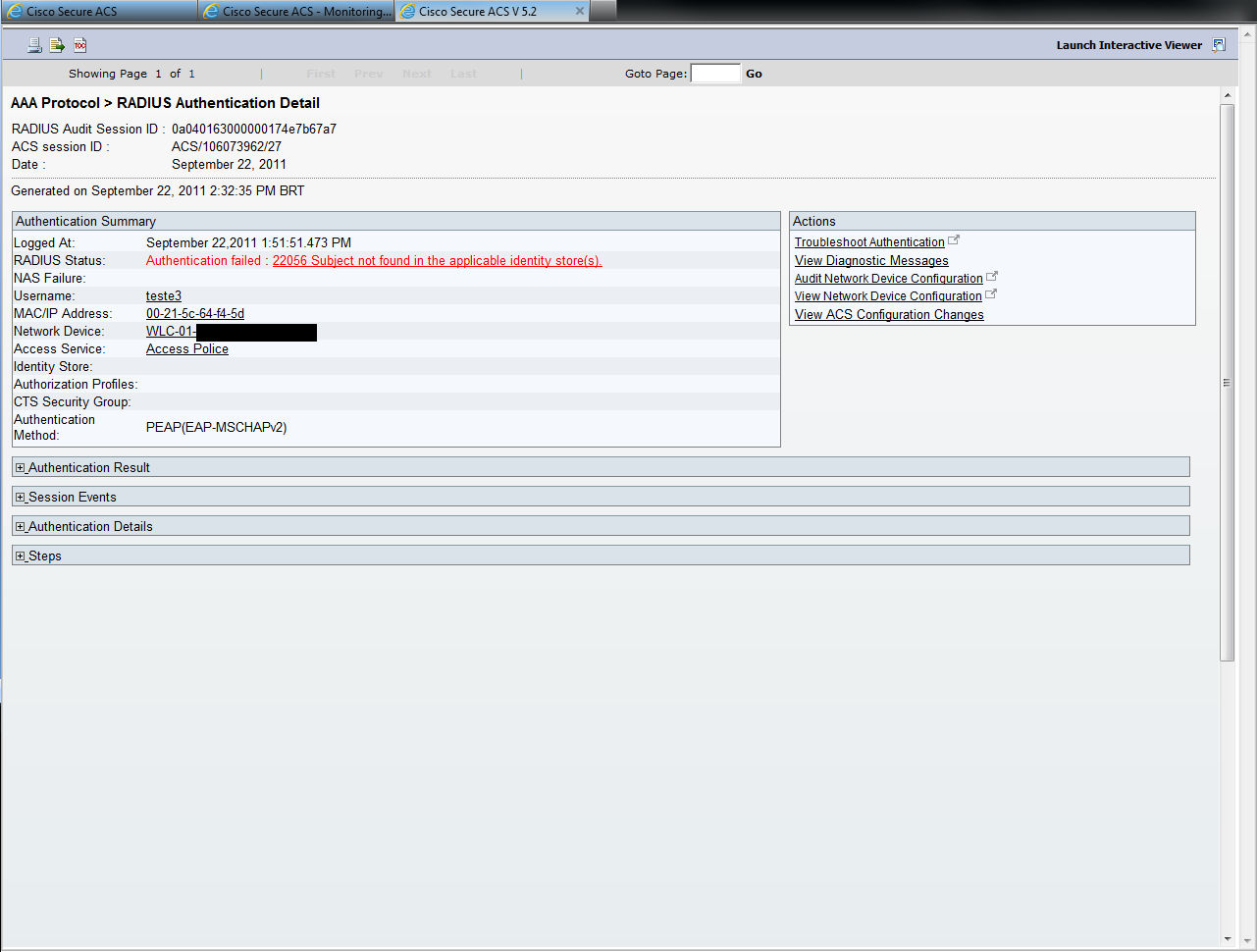
At this point, we can see the error:
| Header 1 |
|---|
11001 Received RADIUS Access-Request 11017 RADIUS created a new session Evaluating Service Selection Policy 15004 Matched rule 15012 Selected Access Service - Access Police 11507 Extracted EAP-Response/Identity 12500 Prepared EAP-Request proposing EAP-TLS with challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 12301 Extracted EAP-Response/NAK requesting to use PEAP instead 12300 Prepared EAP-Request proposing PEAP with challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 12302 Extracted EAP-Response containing PEAP challenge-response and accepting PEAP as negotiated 12318 Successfully negotiated PEAP version 0 12800 Extracted first TLS record; TLS handshake started. 12805 Extracted TLS ClientHello message. 12806 Prepared TLS ServerHello message. 12807 Prepared TLS Certificate message. 12810 Prepared TLS ServerDone message. 12305 Prepared EAP-Request with another PEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 12304 Extracted EAP-Response containing PEAP challenge-response 12318 Successfully negotiated PEAP version 0 12812 Extracted TLS ClientKeyExchange message. 12804 Extracted TLS Finished message. 12801 Prepared TLS ChangeCipherSpec message. 12802 Prepared TLS Finished message. 12816 TLS handshake succeeded. 12310 PEAP full handshake finished successfully 12305 Prepared EAP-Request with another PEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 12304 Extracted EAP-Response containing PEAP challenge-response 12313 PEAP inner method started 11521 Prepared EAP-Request/Identity for inner EAP method 12305 Prepared EAP-Request with another PEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 12304 Extracted EAP-Response containing PEAP challenge-response 11522 Extracted EAP-Response/Identity for inner EAP method 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 12305 Prepared EAP-Request with another PEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 12304 Extracted EAP-Response containing PEAP challenge-response 11808 Extracted EAP-Response containing EAP-MSCHAP challenge-response for inner method and accepting EAP-MSCHAP as negotiated Evaluating Identity Policy 15006 Matched Default Rule 15013 Selected Identity Store - 22043 Current Identity Store does not support the authentication method; Skipping it. 22056 Subject not found in the applicable identity store(s). 22058 The advanced option that is configured for an unknown user is used. 22061 The 'Reject' advanced option is configured in case of a failed authentication request. 11815 Inner EAP-MSCHAP authentication failed 11520 Prepared EAP-Failure for inner EAP method 22028 Authentication failed and the advanced options are ignored. 12305 Prepared EAP-Request with another PEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 12304 Extracted EAP-Response containing PEAP challenge-response 12307 PEAP authentication failed 11504 Prepared EAP-Failure 11003 Returned RADIUS Access-Reject |
So, what can be the cause? Compatibility with LDAP?
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2011 12:22 PM
Plinio,
Look at this doc,
There is a table that says that LDAP isn't a db compatible with our EAP type (MSCHAP-V2).
LDAP you can only use with TLS, PEAP-GTC and EAP-FAST-GTC.
TLS will use certificates on both sides, suplicant and server authentication server.
*GTC if I'm not wrong is a OTP system to use with EAP.
Identity Store | EAP-MD5 | PEAP EAP-MSCHAPv2 | EAP-FAST MSCHAPv2 | PEAP-GTC | EAP-FAST-GTC | |
|---|---|---|---|---|---|---|
ACS | Yes | Yes2 | Yes | Yes | Yes | Yes |
Windows AD | No | Yes | Yes | Yes | Yes | Yes |
LDAP | No | Yes | No | No | Yes | Yes |
RSA Identity Store | No | No | No | No | Yes | Yes |
RADIUS Identity Store | No | No | No | No | Yes | Yes |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2011 12:22 PM
Plinio,
Look at this doc,
There is a table that says that LDAP isn't a db compatible with our EAP type (MSCHAP-V2).
LDAP you can only use with TLS, PEAP-GTC and EAP-FAST-GTC.
TLS will use certificates on both sides, suplicant and server authentication server.
*GTC if I'm not wrong is a OTP system to use with EAP.
Identity Store | EAP-MD5 | PEAP EAP-MSCHAPv2 | EAP-FAST MSCHAPv2 | PEAP-GTC | EAP-FAST-GTC | |
|---|---|---|---|---|---|---|
ACS | Yes | Yes2 | Yes | Yes | Yes | Yes |
Windows AD | No | Yes | Yes | Yes | Yes | Yes |
LDAP | No | Yes | No | No | Yes | Yes |
RSA Identity Store | No | No | No | No | Yes | Yes |
RADIUS Identity Store | No | No | No | No | Yes | Yes |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2011 01:14 PM
+5 Rodrigo
this is an LDAP limitation, not ACS. if ldap db returns a clear text password, mschapv2 methods won't work
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

