- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Anyconnect upgrade via ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2021 11:18 AM - edited 05-19-2021 12:37 PM
Hi Experts
We've Remote Access VPN configured on the ASA (9.8) which is authenticated and authorized by the ISE (2.6) with the posture enabled. Now we'd like to upgrade the Anyconnect (4.8) to 4.10 on the end-users PC.
1.Whether users can download or upgrade with the Anyconnect automatically when connecting to the VPN or does it need to pushed via SCCM?
2. If yes, do they require Admin privileges for the upgrade to happen?
3. I've seen the current Anyconnect image is being uploaded to the ASA as well as to the ISE. Why we need to upload on both the devices?
4. Which device is the Head-end here. Is it ASA or ISE?
Thanks in advance
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2021 08:16 AM
Final one on this thread, what if we force the upgrade to everyone by changing the path in ASA. Considering 1500 users are there, will there be any latency on the ASA/ISE? Will it be able to support the traffic load?
-You should be totally fine for two reasons:
1. Not all clients will VPN at the exact same point in time, and changing the order does not force already connected clients to upgrade. It is on the next connection they will upgrade.
2. The upgrade is not performed from ASA-->Client. The vpndownloader.exe will download the package from the ASA to the client and then the upgrade will be performed locally on each client.
This breaks down the AnyConnect piece: Understanding ASA AnyConnect Webdeploy (learnitwithcifelli.com)
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2021 01:57 PM
1. Auto-upgrade from ASA is simple but I would not try it on a large user count (max. 200 concurrent). SCCM is capable of large-scale deployment.
2. Auto-upgrade from ASA works even with user privileges.
3. AnyConnect image is a mandatory part of the package on ISE even if ISE is not capable of upgrading the image over RAVPN. However, only ISE can upgrade the Compliance Module which is bundled in the package on ISE. (The package is called AnyConnectConfiguration or “Agent” on ISE.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2021 03:34 PM
Thanks for the reply
When the authentication is controlled by the ISE, does the anyconnect is upgraded the ASA or from the ISE?
Which device is the Head-end here. Is it ASA or ISE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2021 10:31 PM
ASA is the headend. ISE is not capable of upgrading the image over RAVPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 01:14 AM
Hi Peter,
Thanks for the assistance.
Any idea on how do we upgrade the anyconnect on a phased approach or pilot users before we rollout to everyone? We're looking for the solution where users can be provisioned with the new software via SCCM but from the ASA config under webvpn, it looks like it's a global settings and it's applicable for everyone.
Can you please assist on this one?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 08:39 AM
Adding some information:
IMO webdeploy from ASA on VPN connections is straightforward and a great way to force the upgrade. As for onsite clients, if you do provisioning onsite then ISE can upgrade all components without the need of elevated privileges. Also, as mentioned by @Peter Koltl ISE webdeploy will fail/not work for RAVPN clients, but compliance module upgrades from ISE will work. If you do not have the on-site ability you can use ASA to aide SCCM with the upgrades and still support both client versions. You just need to support both old & new AnyConnect SW on the ASA & in ISE CPP.
For example, the ASA config entries to support old clients and not force upgrade, but also support new clients would look like this:
anyconnect image disk0:/anyconnect-win-4.9.05042-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-win-4.10.00093-webdeploy-k9.pkg 2
If you flip the order and make the new AC version client entry 1 then clients will get upgraded upon next VPN connection attempt. Another note that is important as you juggle the phased idea is in your CPP AnyConnect Result profiles you can configure it for the new AC clients, but support minimum version (old clients) and auto-defer ISE webdeploy upgrades. Would look something like this:
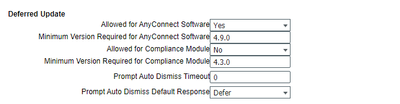
The above config does the following: Allows software deferral for AnyConnect, requires minimum version of 4.9.0 (in your case it would be 4.8.0 or the exact version), forces compliance module upgrade, states compliance minimum version required, and then the '0' combined with defer forces software update deferral without requiring user interaction. Once you confirm every client is upgraded you can reconfig the AC profs as needed. HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 11:20 AM - edited 05-20-2021 11:21 AM
Many thanks for replying in this thread. You've been so helpful in my compliance module upgrade and posture config.
I'm still not able to articulate the phased approach, as config done on the ASA would be for everyone, and the ISE don't do the Anyconnect webdeploy upgrade (it's the ASA which would perform the upgrade image on the client PC)
Is it possible for you to rephrase your statements, so I can get a maximum out of it. Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 12:16 AM
Hello @Mike.Cifelli ,
May i know what is meaning of 1 and 2 below i bold the number?
anyconnect image disk0:/anyconnect-win-4.9.05042-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-win-4.10.00093-webdeploy-k9.pkg 2
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 05:19 AM
@Azlan.my07 those are the order in which the ASA will support the AnyConnect versions, and also what versions are supported. If you move 2 to 1 then when clients running 4.9.05042 connect they will be forced to upgrade via webdeploy since the newer version is now entry one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 05:46 AM
Helo @Mike.Cifelli Thank you for your explanation; however, I have a problem: we have two ASAs configured for anyconnect. I checked that both asa have the same version of anyconnect, but when the user tries to connect, it prompts them to upgrade the software. I already unchecked "Auto Update" in the anyconnect profile, which is why I came across this topic and am trying to find out what the issue right now.
I notice from ASA 1 and ASA 2 configure anyconnect as below, is this the reason why the user keeps getting updates while connecting to anyconnect?
ASA 1
anyconnect image disk0:/anyconnect-win-4.8.02045-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-macos-4.8.02045-webdeploy-k9.pkg 2
ASA 2
anyconnect image disk0:/anyconnect-win-4.8.02045-webdeploy-k9.pkg 3
anyconnect image disk0:/anyconnect-macos-4.8.02045-webdeploy-k9.pkg 4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 06:49 AM
I notice from ASA 1 and ASA 2 configure anyconnect as below, is this the reason why the user keeps getting updates while connecting to anyconnect?
-What version of AC are the users connecting running? If lower than 4.8.02045 then yes, that is why users are being forced to upgrade. I suggest opening another thread outside of this completed one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 10:07 AM
@Mike.Cifelli Thank your for your response. I have created another thread.
https://community.cisco.com/t5/vpn/connecting-anyconnect-push-update/m-p/4599324
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 12:23 PM - edited 05-20-2021 12:25 PM
@Srinivasan Nagarajan no problem glad to help
So you made this comment, We've Remote Access VPN configured on the ASA (9.8) which is authenticated and authorized by the ISE (2.6) with the posture enabled. Now we'd like to upgrade the Anyconnect (4.8) to 4.10 on the end-users PC.
-Quick note, unfortunately you cannot modify the ISE AnyConnect (AC) Config profiles on-the-fly that get assigned in your Client Provisioning Policies as a result when wishing to change AC software version. There is actually a feature request submitted for this, but as of today not sure when it will be implemented.
What I am suggesting for a phased rollout is this:
-Provide SCCM team individual MSIs for new AnyConnect software so they can prep packages & prep your enterprise image (at this point they are awaiting your go ahead for deployment)
-Upload the new AnyConnect webdeploy .pkg file into ISE, create new CPP AnyConnect Config profile specifying new AnyConnect version + currently deployed compliance module + software deferral method mentioned above (shown below too)
-Assign new CPP AC config profiles to your CPP policies (at this point you are now supporting provisioning/posturing for both versions old/new)
-Upload new AnyConnect webdeploy .pkg file on ASA & enable it as first entry while old version remains enabled, but as second entry (this will force VPN clients to get upgraded on next connection attempt)
--Once this is done you can now support both so you can begin phased rollout. Give SCCM team go ahead.
-Have SCCM hit clients that have not been upgraded via ASA
-Once all enterprise clients are upgraded you can update the new CPP policy results for new AC version support to change minimum version requirement.
A way to test this suggested method:
Identify one test group, create new ISE AC Config profile supporting new AC Sw version + current compliance module + software deferral. Assign AC config profile to test CPP policy for your test group. Upload new AC version to ASA but have it enabled as entry 2 (not forcing upgrade, but providing support). Then have one client running old AnyConnect SW and another client running latest/greatest AC Sw. Test connections for both to ensure they get network access & are properly postured as expected. Once tests are good to go you should have no problem implementing on additional CP policies.
Here is a screenshot of a full ISE AC Config Profile supporting new AC version + old version + forcing SW deferral:
Good luck & hope this clears things up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 01:29 PM
Many thanks for the detailed one. It provides more clarity and please correct me if I'm wrong with the following approach from 4.9 to 4.10.
On ASA:-
anyconnect image disk0:/anyconnect-win-4.9.05042-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-win-4.10.00093-webdeploy-k9.pkg 2
On ISE:-
Upload the new image and create a new AC configuration (no software deferral)
ISE CPP Policy:-
Other conditions: Pilot_AD_group = AC_4.10
Domain Users = AC_4.9
As the upgrade progress, can we add users into the Pilot AD group, so they authenticate via AC4.10 (pushed via SCCM)
other users continue to authenticate via 4.9
Is this correct approach as I've followed this approach on ISE for Compliance Module upgrade which went successful and it provided more granularity based on AD groups we needed. Please assist.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 07:00 AM - edited 04-25-2022 07:01 AM
Yes-Yes-0-Defer would be needed to avoid force downgrade to the ISE CM version if the client has higher CM version.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide