- Cisco Community
- Technology and Support
- Security
- Network Access Control
- anyconnect Users unable to connect to Internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 02:05 AM
Hi All,
Setup an anyconnect VPN client in which Users are getting Authenticated and Authorize via ISE. Where Authentication is done based on AD Users/Group, while authorization is achieved via DACL for each tunnel group.
DACL is getting push successfully and also granular User base access has been achieved. But facing a problem of Users not getting an Internet after connecting to anyconnect vpn client
Attaching my Natting Policy for VPN Pool users.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 04:07 AM
Your Authorization result "GroupPolicy_VPNUsers" sends the dACL "acl_GroupPolicy_VPNUsers" allowing access to only 3 IP addresses in the 192.168.240.0 network.
Thus your authorized users will only be able to access those three addresses - i.e not the Internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2019 05:16 AM
Yes, vpn filter is the ASA-managed rough equivalent to ISE-managed dACL.
Of course ISE has more power and complexity.
Those two features however essentially accomplish the same thing - restrict a user or group to only the mentioned resources.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 02:57 AM
Is 11.1.1.0/28 your VPN pool?
What does packet-tracer on the ASA tell you if you use one of those addresses (pick a currently unassigned one) as the source and an Internet address as the destination?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 05:55 AM
Hi Marvin,
Thanks for your reply.
I have notice that if i authenticate my anyconnect users locally users are getting internet, but same if i authenticate and authorize via ISE users are unable to get internet access.
Is it anything ISE DACL blocking or need to have any ACL for Users authorizing via ISE Posturing. Attaching ISE DACL configuration example where 192.168.240.0/24 is my internal server ip address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 07:24 AM - edited 09-23-2019 07:25 AM
You didn't attach your dACL but here's what I use in my lab based on some best practices guide. In my case, Authorized VPN users are allowed access to anything.
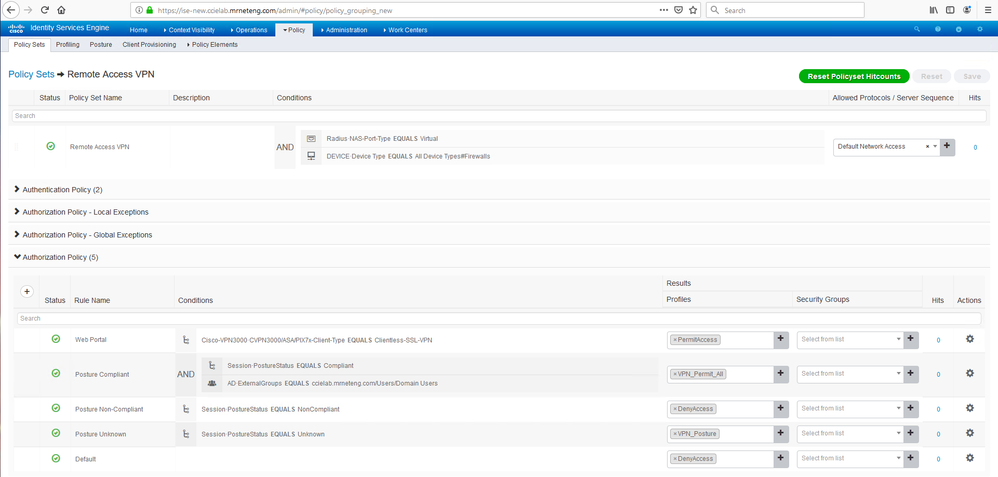

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 10:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 04:07 AM
Your Authorization result "GroupPolicy_VPNUsers" sends the dACL "acl_GroupPolicy_VPNUsers" allowing access to only 3 IP addresses in the 192.168.240.0 network.
Thus your authorized users will only be able to access those three addresses - i.e not the Internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2019 08:23 PM
Hi Marvin,
Just a small doubt, if you help it would be great for me.
Is it the ASA Vpn-filter works the same way as ISE dacl??
Cause when I apply it (Vpn filter) in my group policy by mentioning some of my internal server only, users are unable to reach internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2019 05:16 AM
Yes, vpn filter is the ASA-managed rough equivalent to ISE-managed dACL.
Of course ISE has more power and complexity.
Those two features however essentially accomplish the same thing - restrict a user or group to only the mentioned resources.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

