- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Can ISE/ASA/Anyconnect support multiple AD group membership?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2016 06:31 AM
I have a customer that is interested in deploying a remote access VPN solution using ASA, ISE and Anyconnect. Customer wonders how the solution can support user permissions when the user is part of multiple AD group within the memberOf attribute. Ideal flow would be that the permissions of each group would be appended/cumulative so that the permissions of all groups they are a member of are enabled simultaneously. They have 40-50 groups with unique ACL/permissions on each group.
In addition the customer is concerned about bug CSCum57190 which may impact this deployment.
Looking for guidance on how to support this without suggesting a re-ordering of their AD structure.
Thank you!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2016 09:14 PM
Previously, chips mentioned that some Cisco folks have some success in using "multi-match" authorization policy (non-Policy-set only) and cisco-avpair=ip:inacl to create separate authorizations which are then collectively applied to ASA.
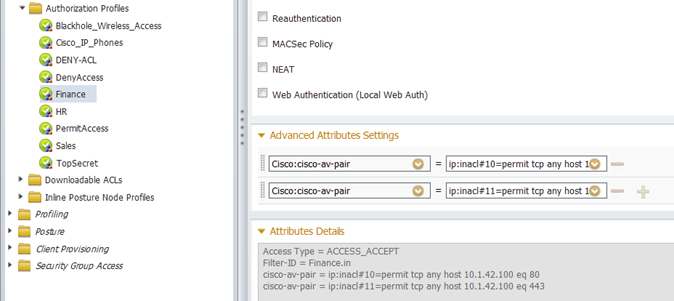
And, vibobrov illustrated it like this:
You can use ip:inacl#x ACL format to send ACEs from multiple ISE rules to the NAD. So you can do something like:
if user is in WebUsers group, send ip:inacl#1=permit tcp any any eq 80
if user is in SSHUsers group, send ip:inacl#2=permit tcp any any eq 22
You lose the neat way of managing ACLs, but the use case can be met. ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2016 09:14 PM
Previously, chips mentioned that some Cisco folks have some success in using "multi-match" authorization policy (non-Policy-set only) and cisco-avpair=ip:inacl to create separate authorizations which are then collectively applied to ASA.

And, vibobrov illustrated it like this:
You can use ip:inacl#x ACL format to send ACEs from multiple ISE rules to the NAD. So you can do something like:
if user is in WebUsers group, send ip:inacl#1=permit tcp any any eq 80
if user is in SSHUsers group, send ip:inacl#2=permit tcp any any eq 22
You lose the neat way of managing ACLs, but the use case can be met. ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2016 04:44 PM
Is there any size limitation of cisco av-pair ip:inacl?
How many ACEs could be fit into one radius packet since single Radius attribute can be up to 255 bytes long as explained in CSCum57190?
Could this av-pair be sent using as many RADIUS packets as required to transport the full ACL from ISE to ASA?
What is the merging algorithm where there is overlapping ACEs from different groups?
Will this cisco av-pair work with COA of ASA Version 9.2.1 VPN Posture with ISE Configuration Example - Cisco?
Is it possible to use ISE and ASA to have flexibility like DAP for accumulating Network Type ACL, Web Type ACL, Port-forwarding List, and URL lists for different LDAP group?
ASA 8.x Dynamic Access Policies (DAP) Deployment Guide - Cisco
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

