- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Can ISE send a CoA in an Authorization Profile?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can ISE send a CoA in an Authorization Profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2018 09:05 PM
Hello
Customer asked if/how ISE can trigger a CoA in an Authorization Profile. I can't see how this is done in ISE.
Use case. Windows user authentication to trigger a VLAN change, using standard Windows supplicant.
They want to be able to bounce a wired port and force the user onto a different VLAN. The NAS is a Meraki Security appliance and it only listens for 802.1X frames for 8 seconds, and then defaults into a guest VLAN. By the time the user types in the AD username and password, the device is already in the Guest VLAN.
One option is to disable the Guest VLAN and have the PC hand around in Layer 2 limbo, waiting for the user auth.
But the Meraki docs do mention ISE and CoA ...
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 04:47 AM
Not that I know of
You could build a guest portal with a link to
A portal that has a kick off disconnect perhaps? Call the api?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 04:04 PM
I would have to ask Meraki the same question. Perhaps they alluded to the case where profiling is used to switch VLANs. I believe in that case ISE would send the CoA? I don't know much about profiling ![]() - but this is not what the customer wants.
- but this is not what the customer wants.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 04:49 PM
So what you are asking is if it’s possible to switch vlans after authentication? Sounds like the customer wants the default VLAN to be the guest VLAN. Is that the goal here? The desired functionality isn’t clear to me yet.
Warning: I either dictated this to my device, or typed it with my thumbs. Erroneous words are a feature, not a typo.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 05:03 PM
I don’t see how profiling has anything to do with dot1x failure to mab?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 05:16 PM
I am quoting the Meraki documentation from the URL I mentioned in my opening post.
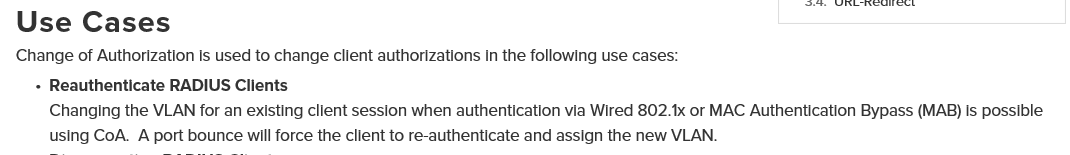
Now Meraki have sold me the dream ![]() ... and they mention ISE is a Radius server (see below).
... and they mention ISE is a Radius server (see below).
But they fail to explain how ISE is supposed to achieve this. That is what I want to know.
How does one marry up the statement above (changing VLAN when auth is 802.1X, and CoA using ISE)
More Meraki goodness ...
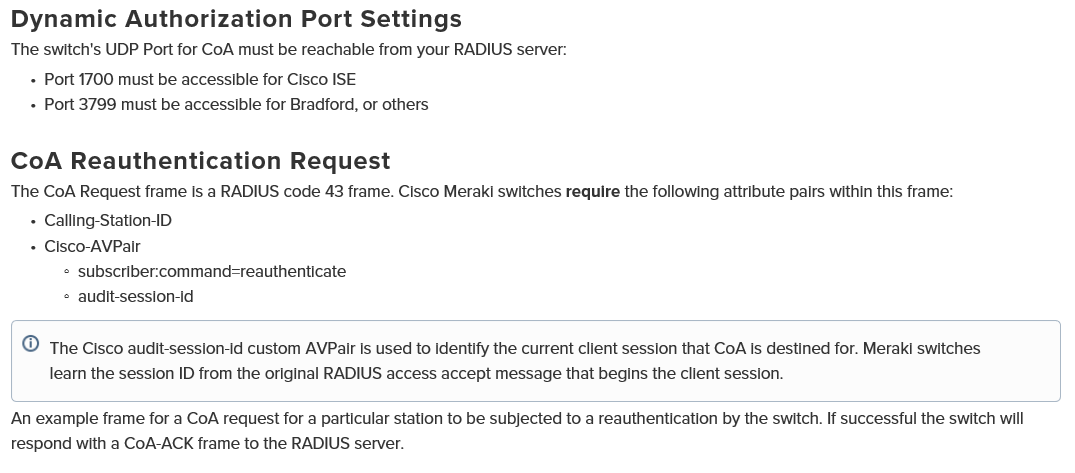
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2018 06:34 AM
If George is correct on the intend, then it does not require CoA at all. VLAN will be a set of tagged attributes included in the matched authorization profile.
ISE profiling has a global CoA Type at [Administration > System > Settings > Profiling] and default to No CoA. And, individual profile policies may override for CoA. If it set to perform CoA and if ISE detects a profiling event that would result in a different authorization policy rule, then ISE will trigger a CoA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2018 02:37 PM
Arne,
Yes, of course ISE supports RADIUS CoA. However, CoA does not happen in a RADIUS Authorization. CoA is initiated by the RADIUS server (ISE) asynchronously outside of the authentication request/response based on some other event (administrator, threat, API, etc.).
You may be asking if Meraki support RADIUS CoA. According to How To: Integrate Meraki Networks with ISE , they do.
A single 8-second timeout is incredibly short for 802.1X as you have found. We suggest 10 seconds x 3 retries as best practice as recommended in How To: Universal IOS Switch Config for ISE, Step 17.
Even if the authentication fell through to a MAB with Guest default, a good desktop supplicant would initiate an EAPoL-Start when the user enters their 802.1X credentials when not in response to an 802.1X EAP challenge which would then trigger the switch to do a RADIUS re-authentication.
If for some reason that is not working, you could potentially try doing a short RADIUS Attribute 27 (Session-Timeout) and 29 (Terminate-Action) to cause a re-authentication for Guest. Keep in mind that this could greatly increase the load on ISE for endpoints stuck in this state.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2021 04:32 AM - edited 08-12-2021 05:01 AM
Hi Thomas
Arne touched painful topic from my pov. As i understand in case of CoA configuration is set to reauthenticate each CoA sent to NAD will introduce downtime for target endpoint during reauthen process. I've found one of managed deployment (2.1) sending CoA w/o obvious reason (meaning that even if endpoint got authC'ed/authZ'ed ISE starts to send CoA relevant to this endpoint as soon as CoA is set to reauth). Any idea about why ISE considers to do this?
Attached screen shows how it looks like: bottom record - device was profiled & authorized, upper - CoA was configured to Reauth globally at about 12:36
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide





