- Cisco Community
- Technology and Support
- Security
- Network Access Control
- cisco ise 2.3 command set & shell profile can work together?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2022 06:45 AM - edited 01-24-2022 09:54 AM
Hi friends, I created a new user going through the TUFFIN system in ISE with privilege of 3, in addition I limited the user to specific commands through the COMMAND SET.
But it does not work, when I check in the logs I see that the request goes to SHELL PROFILE but does not go to MATCHED COMMAND SET.
command set & shell profile can work together?
In ISE 2.3.
Thank
Shlomo Yitzhak
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2022 01:56 PM
Thanks for the clarification. It was not clear that you were trying to enable command authorization on a Cisco switch.
It sounds like you may not have the switch configured correctly for command authorization. I would suggest reviewing your ISE and switch configurations against the examples in the Device Admin Prescriptive Deployment Guide.
If it is still not working, the community would need more information to help including:
- Hardware/Software version of the switch
- Switch configuration related to AAA, TACACS+, and VTY lines
- Screenshots of Device Admin AuthC/AuthZ policy conditions
If the issue is urgent, please open a TAC case to investigate the issue in more detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2022 02:18 PM
Yes, ISE TACACS+ Authorization Policies can use a combination of Shell Profile and Command Sets. You can see an example of this for Cisco IOS Switches/Routers in the Device Administration Prescriptive Deployment Guide.
The system or network device using ISE, however, must support TACACS+ Command Authorization. Doing a Google search, I could only find external Authentication for Tufin. You will need to confirm if Tufin supports external Authorization or if you need to configure local Authorization in Tufin based on the privilege level returned by the Shell Profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2022 12:18 AM - edited 01-25-2022 12:19 AM
Hi Greg really thanks for the help.
I have set up a local user for TUFFIN with 3 privileges, but I want to allow TUFFIN to access only 5 commands.
show clock
show version
show access-lists
show ip route
show ip interface
And block everything else.
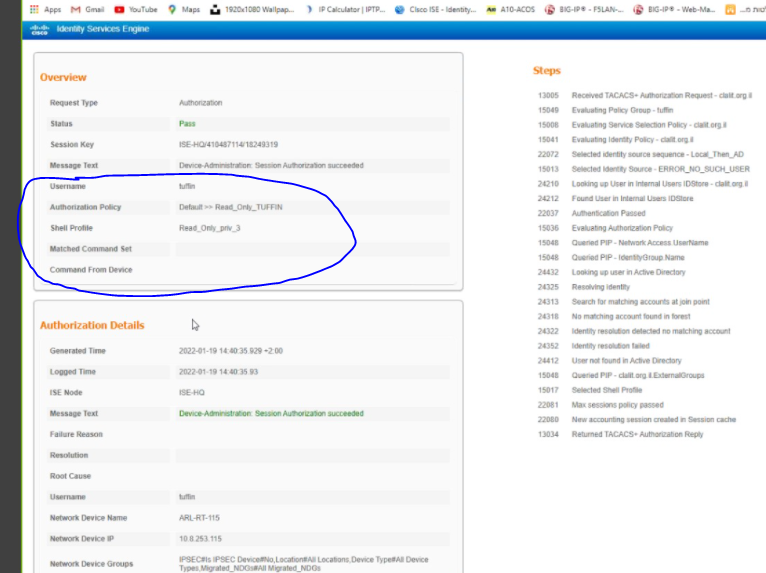
I have set in COMMAND SET the policy with the commands I want to enable but I see (image attached) that the request goes to SHELL PROFILE but does not go to COMMAND SET. There may be a bug in the version ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2022 02:17 PM
As I said in my earlier post, the system or network device (i.e. TACACS+ client) using ISE must support TACACS+ Command Authorization.
TACACS+ is essentially a suite of protocols and uses separate mechanisms for Authentication, Authorization, and Account. Just because a client supports external TACACS+ Authentication, does not mean it supports external TACACS+ Authorization.
From the RFC 8907 standard for TACACS+:
"In command-based authorization, the client requests that the server determine whether a command is allowed by making an authorization request for each command. The "cmd" argument will have the command name as its value."
As this communication is initiated by the client (Tufin, in this case), you need to verify that Tufin supports this external command authorization. You could also try to capture traffic from Tufin to confirm if you see the Authorization request being initiated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2022 02:50 AM
Hi Greg Thanks for the help.
I do not know the ISE so well and probably did not explain myself so well . TUFFIN asked me to make a user for it so they could access my Cisco switches and see a number of RUN commands. I'm not interested in connecting the TUFFIN to ISE. All they asked for was a local user on the ISE with privilege 3, and this user was limited to only 5 commands. I set up a user on the ISE with privilege 3 and limited through the COMMAND SET the SHOW commands I want.
All I need is a local user on the ISE with privilege 3 so that TUFFIN can access my Cisco switches and see 5 SHOW commands. Because privilege 3 allow more RUN commands that I do not want the TUFFIN to see so I try to restrict it via the COMMAND SET and it does not work.
Thanks shlomo itzhak
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2022 01:56 PM
Thanks for the clarification. It was not clear that you were trying to enable command authorization on a Cisco switch.
It sounds like you may not have the switch configured correctly for command authorization. I would suggest reviewing your ISE and switch configurations against the examples in the Device Admin Prescriptive Deployment Guide.
If it is still not working, the community would need more information to help including:
- Hardware/Software version of the switch
- Switch configuration related to AAA, TACACS+, and VTY lines
- Screenshots of Device Admin AuthC/AuthZ policy conditions
If the issue is urgent, please open a TAC case to investigate the issue in more detail.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide