- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE 2.3 Patch 1 in Distributed Environment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2017 03:27 AM
Hi All
Please could you let me know if anyone had success installing Patch 1 to Cisco ISE 2.3 in a distributed environment. In my lab after the Patch 1 install the authentication policies seems to have disappeared and no policy changes could be made. Seems like a bug
Any response would be highly appreciated.
Thanks
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2017 05:17 PM
CSCvg44615 looks similar to your symptom and seems due to the default auth rule setting to Deny Access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2017 03:19 PM
I have had success, although I had two PAN/MnT nodes, and one PSN node. Does that qualify for distributed ? :-)
I am able to change policies and nothing went missing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2017 05:41 PM
Thanks for your reply. Did you have PAN & MnT roles in separate nodes or together ? In my scenario all roles are on separate nodes. After the patch the authentication policies are all gone and I was unable to make any changes to policies. If I roll back the patch it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2017 08:31 AM
Please make sure you open a tac case
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2017 08:43 AM
Like Jason suggested, it's best to engage Cisco TAC to troubleshoot. Otherwise, please provide a copy of your ISE 2.3 CFG backup before applying Patch 1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 07:47 AM
Hi everyone
Thanks for your responses. I would surely log this with Cisco TAC. But out of curiosity I have setup another LAB and done some tests and have been able to reproduce the problem.
If you deploy 2.3.0.298 and create a Policy Set with some Authentication and Authorization rules and then apply the Patch 1 you would be able to reproduce the error. The default policy set doesn't seem to be affected unless you customized the default policy set. Any customization/addition done to Policy Sets before Patch would be affected. This was a distributed deployment.
If anyone sees the issue please do let me know.
Thanks for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2017 05:17 PM
CSCvg44615 looks similar to your symptom and seems due to the default auth rule setting to Deny Access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2017 10:49 AM
Hi hslai
I tried searching for the bug but it seems I do not have sufficient privileges to view the bug details. Please could you let me know if this would be resolved by Cisco or we would have to use a workaround as you suggested.
According to your workaround shall I modify the Default Policy Set or Default Authentication rule within my custom Policy Set.
My expectation was Cisco would have tested these basic things before releasing a Patch as this would affect significantly in a production environment.
Thanks for your assistance on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2017 11:00 AM
Please open a TAC case and ask TAC to request for a hot patch.
The bug should become visible in a day or two. Yes, TAC case notes for another customer showed the workaround is to delete the rule and reconfigure it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2017 11:45 AM
Policy Set - Authentication Policy is empty (Null Pointer Exception) if setting 'Deny Access'
CSCvg44615
Symptom:
ISE Authentication Policy shows no rules.
Conditions:
ISE 2.3 Patch 1
One of the authentication rules, including default, uses "Deny Access" as the identity source.
Workaround:
Delete the affected policy set, reconfigure all authentication policy rules to use an identity source other than "Deny Access".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2017 02:38 PM
Hi Favas
Thanks for the bug details. The workaround is difficult in production so I presume not applying Patch 1 is best way forward.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2017 01:20 PM
Successfully installed 2.3 Patch 1 on 11/3/2017 into a distributed deployment with (2) MnT, (2) PAN, (6) PSN, (2) SXP, (1) PXG. I went through every Authentication Policy and confirmed none of them were configured to use the 'DenyAccess'.
The upgrade took about 15m per node. No issues related to the upgrade reported so far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2017 02:27 PM
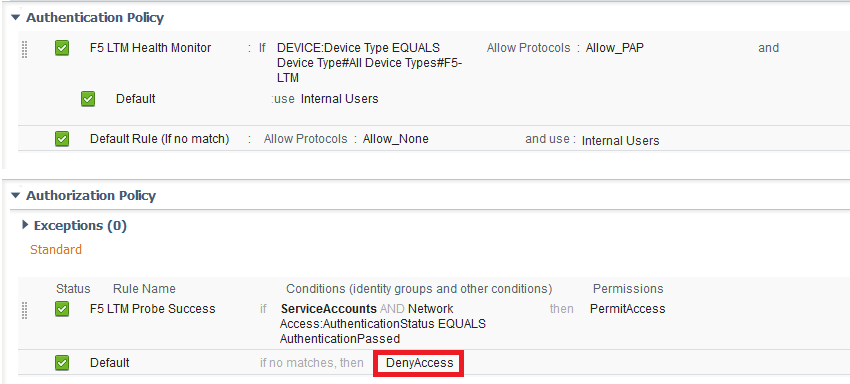
@Randy - that sounds promising. Just to be clear, does the Patch 1 bug affect Authentication Policies where there is at least one DenyAccess - e.g. below. If I leave it as is, will something break?
I have tried to make all my Policies as water tight as possible and I don't use defaults - e.g. in the Default Rule I use "Allow_non" as allowed protocols (which is an empty list). And I always put DenyAccess at the end of all my Authorization Policies.
But if that is going to break my policies then I can relax that for the purposes of the patch 1, which I am planning this Thursday.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2017 02:52 PM
arne.bier as I understand it, you need to make sure 'DenyAccess' is not applied to any of your 'Authentication Policies'. In the environment I just upgraded, some of the 'Authorization Policies', not all, still had default 'DenyAccess' as last rule. The bug, accordingly to what I read and what TAC told me, only applies to your 'Authentication Policies'.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2017 05:14 PM
Hi Arne
I would be a little careful. Because allowed protocols option in v2.3 is at Policy Set Level only. Inside a policy set where you have authencation rules you dont have allowed protocol option anymore.
I would suggest to have a look in a lab at the 2.3 architecture before you upgrade production. Also please ensure you verify this with the experts in the forum.
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



