- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE 802.1x Machine Authentication Cert EAP-TLS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2020 07:56 AM - edited 02-21-2020 11:12 AM
Hello,
I've been tasked with helping roll out 802.1x on our network, and am primarily over the Windows side of setting up group policies for Machine Certificate Auto Enrollment, and configuring the authentication methods. Because the networking team will primarily be handling the Cisco ISE portion of 802.1x, there is quite a large disconnect about what needs to be done. I'm trying to find good documentation between Cisco ISE 802.1x and Windows 802.1x (Group Policies for setting the correct authentication type, Enterprise CA Certificates), but haven't found anything specific to this scenario. Most videos or guides I've found are only for PEAP (username/password) and EAP-TLS (certificate) combined.
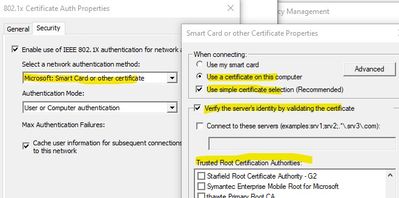
We'd just like to use machine certificates to authenticate. From what I'd understand, I'd just set the network authentication method to: "Microsoft: Smart Card or other certificate", and select the trusted root certification authorities. I just don't see any guides for this type of configuration. It would be nice if there was more information about how to set up the Cisco ISE and Authentication within windows to match for this scenario. Are there any guides/documentation that you know of for EAP-TLS only? Or is PEAP and EAP-TLS necessary to work with Cisco ISE/Windows clients?
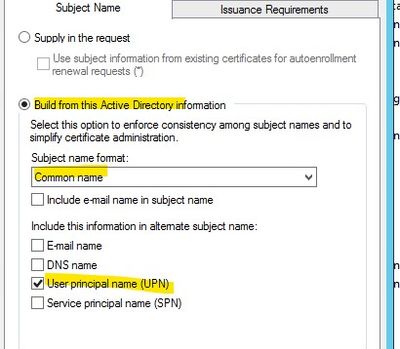
I also am not sure what Cisco ISE requires as a subject name for certificates to work (both Mac & PC):
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2020 09:44 AM
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2020 09:44 AM
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2020 07:38 PM
-Ryan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide