- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE Device admin Authz rules query
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2019 02:46 AM
Hi Team,
Have a query regrading exclusion for Cisco Prime user request(auth/authz) to ISE nodes.
CU is having the Cisco Prime into network for monitoring/config change. Prime have the level 15 admin user which auth/authz on every network device(20K) and pull the required info that creates huge requests on ISE.
Can be a way to exclude the specific user or Prime IP exclusion on ISE to proceed further for auth/authz requests to minimise the overhead.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 05:47 AM
I don't quite follow what you've just written. But when you say "bypassed" then you surely mean "do not use TACACS at all". If your NAS sends a TACACS request to ISE then there is no concept of bypassing. ISE has to process the request. You can chose to authenticate locally (ISE internal user) - that is the only "optimisation"you can do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2019 04:19 AM
Well Prime is causing an authentication event on the NAS, so in reality it's not Prime's issue - you need to configure the NAS to first perform local auth, then TACACS. But if the NAS will always do TACACS first and local user only if AAA is down, then you have no hope to avoid the AAA call. You could put the use in the ISE Identity Group to avoid an AD/LDAP lookup.
On Cisco WLC you can set the order to be LOCAL, then TACACS. That would solve your issue. But it opens up a security issue because users can then bypass your TACACS server by creating their own accounts - and then TACACS doesn't log the commands,etc. Bad practice. Avoid that.
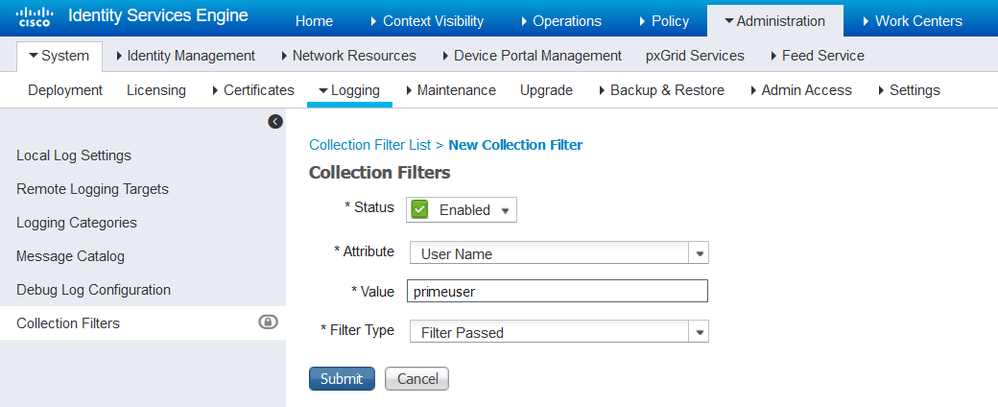
If the issue is that you don't want to see these events in LiveLogs then you can enable a Collection Filter to remove the events from the Logs (and reports too).
Administration -> System -> Logging -> Collection Filters
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2019 11:06 PM
Hi Arne,
Thanks for highlighting the use of Collection filter, can be a use case for CU for prime live logs filtering.
WLC is not a case as CU using TACACS feature only. In this case, I am not sure if only prime user can be filtered as Local auth on NAD devices. more looking on ISE side, can be a way to filter prime user authentication and should not be entertained/directly bypassed for authorization requests.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 05:47 AM
I don't quite follow what you've just written. But when you say "bypassed" then you surely mean "do not use TACACS at all". If your NAS sends a TACACS request to ISE then there is no concept of bypassing. ISE has to process the request. You can chose to authenticate locally (ISE internal user) - that is the only "optimisation"you can do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 08:56 AM
Hi Arne, thanks for more input. was looking that can bypass specific username or not on ISE.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide