- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE loadbalancing with A10 loadbalancer
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 02:36 AM
Is anyone in the community running multiple PSNs behind an A10 loadbalancer? There seems to be lots of documents on how to do it with F5 but not A10. I can get so far using wireless MAB in that a wireless client will get the login portal page and a suer can login in. On the wireless controller I can see that the client gets the redirect ACL but it never gets a successful CoA to pass it to the policy ACL.
I see multiple RADIUS errors on the ISE in the live logs. It looks as though the RADIUS requests are coming from the real interface (server side) of the A10 rather than the VIP. Currently I only have one real server (PSN) configured to avoid any persistence issues.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 01:47 PM
Mark,
Here you go. I cleaned up the config and modeled it after the following fictional topology:
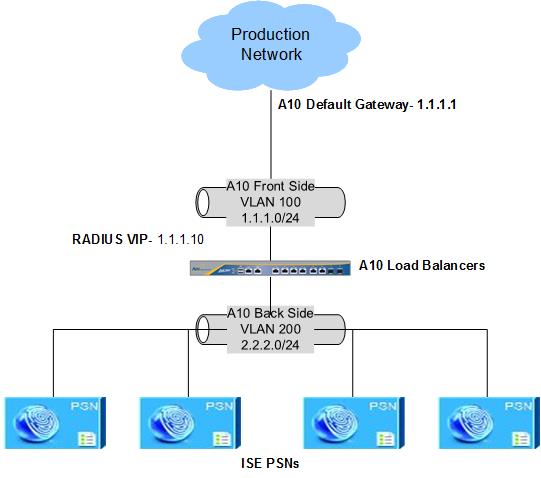
******************************************************************************
Interface Config, need to enabled the support of a promiscuous VIP
******************************************************************************
interface ve 1/28
name PSN Subnet
enable
ip address 2.2.2.1 255.255.255.0
ip allow-promiscuous-vip
*****************************************************
NAT Pool, RADIUS VIP to change CoA to
*****************************************************
ip nat pool COA-RADIUS-NAT 1.1.1.10 1.1.1.10 netmask /32 vrid 1
*****************************************************
Virtual Port Template
*****************************************************
slb template virtual-port SNAT-PORT-PRESERVE
snat-port-preserve
**************************************************************
Access List, only traffic from PSN subnet to UDP 1700
**************************************************************
ip access-list ISE-CoA
permit udp 2.2.2.0 0.0.0.255 any eq 1700
*****************************************************
Server, send traffic to A10 Default Gateway
*****************************************************
slb server A10-DFGW 1.1.1.1
health-check-disable
port 0 udp
health-check-disable
*****************************************************
Service Group
*****************************************************
slb service-group SG-A10-DFGW udp
member A10-DFGW 0
*****************************************************
Virtual Server
*****************************************************
slb virtual-server VS-ISE-COA 0.0.0.0 acl name ISE-CoA
vrid 1
port 0 udp
name ISE-CoA:udp-0
source-nat pool COA-RADIUS-NAT
service-group SG-A10-DFGW
template virtual-port SNAT-PORT-PRESERVE
no-dest-nat
So basically the VIP is doing MAC address swapping and the destination IP is not change at all. Just changing the destination MAC address to that of the default gateway, changing source IP to RADIUS VIP IP and sending packet on its way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 04:16 AM
I have done a large deployment with A10s before. We worked with the A10 support team to get a COA SNAT solution working that changes the CoA packet to be sourced from the VIP. I don't remember the specifics, but once we clearly spelled out what we need from the A10 the support at A10 was easily able to get a solution for us.
Basically all we told them was "We want any packet with a destination port of UDP 1700 sourced from the back side subnet to anywhere in the network to have its source IP changed to the VIP we are using for RADIUS."
I will try to contact the customer, to see if he will share a scrubbed version of the A10 setup for that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 05:00 AM
Many thanks for this. If you can get anything from the customer also that would be much appreciated.
Mark Pearson
Team Leader
Nottingham Trent University | Information Systems | 50 Shakespeare Street | Nottingham | NG1 4FQ
E: mark.pearson@ntu.ac.uk<mailto:mark.pearson@ntu.ac.uk> | P: 44 (0)115 848 8287<tel:441158488287> | M: 44 (0)7900 138476<tel:447900138476> | S: Skype for Business<sip:mark.pearson@ntu.ac.uk>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 01:47 PM
Mark,
Here you go. I cleaned up the config and modeled it after the following fictional topology:

******************************************************************************
Interface Config, need to enabled the support of a promiscuous VIP
******************************************************************************
interface ve 1/28
name PSN Subnet
enable
ip address 2.2.2.1 255.255.255.0
ip allow-promiscuous-vip
*****************************************************
NAT Pool, RADIUS VIP to change CoA to
*****************************************************
ip nat pool COA-RADIUS-NAT 1.1.1.10 1.1.1.10 netmask /32 vrid 1
*****************************************************
Virtual Port Template
*****************************************************
slb template virtual-port SNAT-PORT-PRESERVE
snat-port-preserve
**************************************************************
Access List, only traffic from PSN subnet to UDP 1700
**************************************************************
ip access-list ISE-CoA
permit udp 2.2.2.0 0.0.0.255 any eq 1700
*****************************************************
Server, send traffic to A10 Default Gateway
*****************************************************
slb server A10-DFGW 1.1.1.1
health-check-disable
port 0 udp
health-check-disable
*****************************************************
Service Group
*****************************************************
slb service-group SG-A10-DFGW udp
member A10-DFGW 0
*****************************************************
Virtual Server
*****************************************************
slb virtual-server VS-ISE-COA 0.0.0.0 acl name ISE-CoA
vrid 1
port 0 udp
name ISE-CoA:udp-0
source-nat pool COA-RADIUS-NAT
service-group SG-A10-DFGW
template virtual-port SNAT-PORT-PRESERVE
no-dest-nat
So basically the VIP is doing MAC address swapping and the destination IP is not change at all. Just changing the destination MAC address to that of the default gateway, changing source IP to RADIUS VIP IP and sending packet on its way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2018 02:15 AM
Thanks Paul, I'll give this a go and let you know
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2018 01:54 PM
If verified working, I can link to config from our HA/Load Balancing page since we lack an A10 example.
From config, it does not appear that A10 supports persistence on RADIUS attributes like Calling Station ID and no RADIUS-specific health monitor, correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2018 02:00 PM
Craig,
I can’t remember what we did for persistence at the customer I posted the A10 CoA config from. I thought we did something with RADIUS Calling Station ID, but not sure. The config snippet I was helping Mark with was just around the CoA SNATting piece.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide