- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: CISCO ISE - Radius Failed Authentications
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 08:02 AM
Hi All,
Apologies if this is in the incorrect place - just wondering if somebody could help explain something. We have a wireless network which is managed and maintained by the local authority - the WLC is located remotely (Catalyst 9800-80) along with the ISE server.
I have limited access to viewing logs on ISE and I do have limited access to Cisco Prime to view things - we don't have any access to the config / setup.
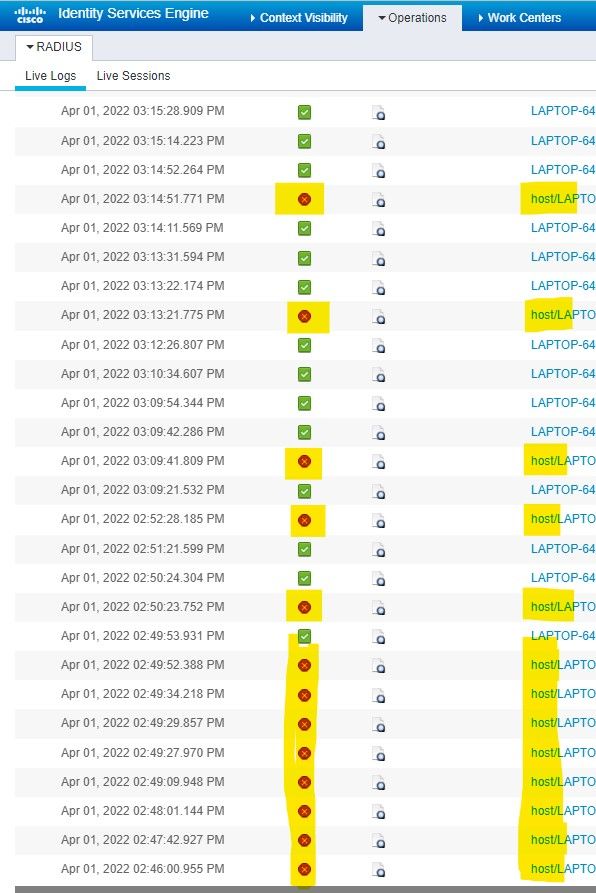
Our clients connect to 9120AXI-E Access Points - Throughtout the day we have major issues with devices not being able to connect - this tends to happen more when they are roaming across the building - and can then take quite sometime to re-connect. When I look at the ISE Live log files I see the following... Could somebody tell me what the difference is between the one's listed as HOST\laptopname that keep showing up with a red cross and those that just have the laptop name that have green ticks - the MAC address against the two are the same.
Why are some listed as HOST\name and others not?? - How do we fix this if it is a problem.
Thanks
Matt
Solved! Go to Solution.
- Labels:
-
Catalyst Wireless Controllers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2024 12:01 AM
And for anyone reading this far. The Windows eventlog which could have shown the error (CRL checks failing/timing out) is
"Applications and Service Logs/Microsoft/Windows/CAPI2/Operational"
You have to enable it first (which requires local admin rights), and then it will tell you all the details that the regular "Wired-Autoconfig" and "WLAN-Autoconfig" doesn't show.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2025 11:13 AM
For anyone stubmling on the issue.
You have to disable certificate revocation check on workstations with adding dword to regedit path.
Microsoft's workaround for this is to set a registry key to disable CRL checks for EAP-TLS:
PATH: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan\PPP\EAP\13
DWORD NoRevocationCheck
Value: 0x1 Set value to 1 to force the workstation not do to revocation check.
You can check the other thread where it explains https://community.cisco.com/t5/network-access-control/ise-wired-supplicant-crl-ocsp-check-issue/td-p/4022723
this made me huge headaches especialy when implementing EAP auth on dislocated Branch sides. Good luck
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide