- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE ROPC with Azure - EAP-TLS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 11:24 PM
Hi Team,
Greetings.
I have a question regarding Cisco ISE Integration with Azure Using ROPC - EAP TLS for WiFi User Authentication.
We are doing PoC with Our customer to Implement 802.1x/EAP-TLS with Azure (by using ROPC), based on documentation :
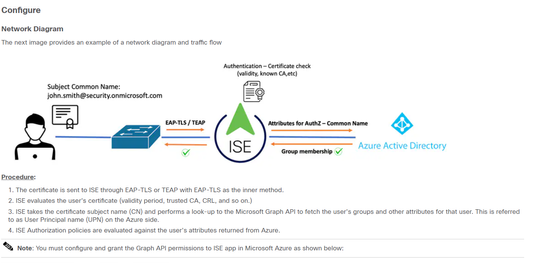
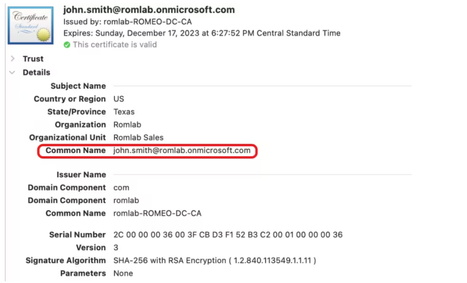
from what i understand in the document, that ISE will become "intermediary" to match between Client certificate in client device and on the Azure:
The question is :
- who's generate the certificate for the User (like one above) ? is it Azure?
- If it Azure, what Service on Azure that we need to used/enable?
- In the documentation, it also mention:
what root CA & Intermediate CAs we need to upload to ISE? is it from Azure ?
- Do ISE keep/saved Certificate of the user generated by Azure? if it is, where ISE keep it ?
Thanks!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2023 05:30 AM
Your own internal PKI generate the certificates. How you get the identity certificates to the machine is up to you. Most customers I work with use ADCA and InTune for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2023 10:12 AM
The OAuth-ROPC method is only used for username+password based authentication over EAP-TTLS+PAP.
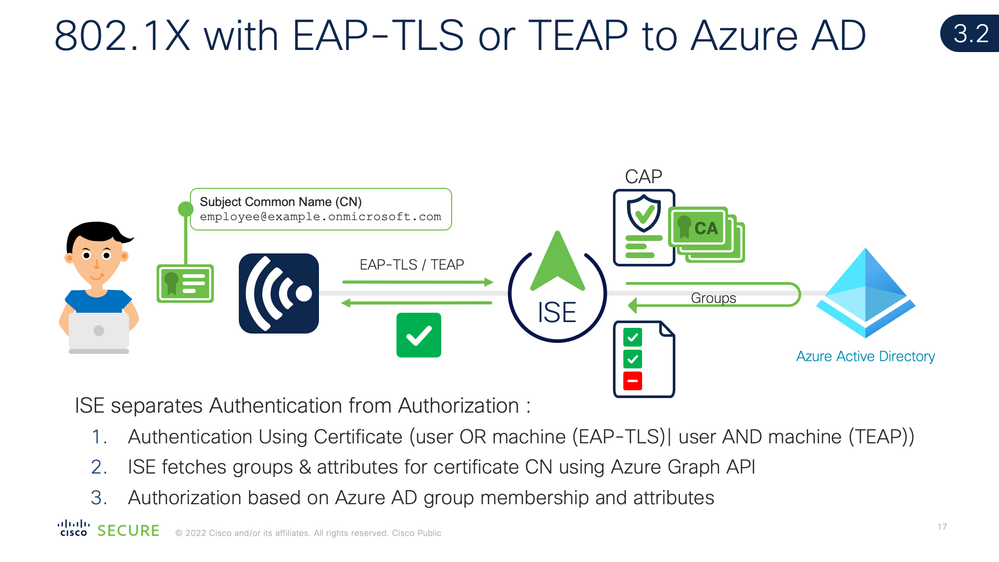
EAP-TLS user certificate-based authentication is authenticated by ISE based on any certificate authentication profile then an Azure AD group lookup is done separately for the User Principle Name (UPN) in the certificate. See Configure Cisco ISE 3.2 EAP-TLS with Microsoft Azure Active Directory
Consider watching our ISE Webinar that covers this topic and more:
▷ ISE Integration with Intune MDM 2022/08/02
28:25 EAP-TLS Authentication to AD : computer or user) (traditional 802.1X with AD)
30:06 TEAP(EAP-TLS) Authentication in ISE 2.7+ for computer+user (EAP-Chaining)
33:33 EAP-TLS Authentication with Hybrid AD+Azure Compliance
34:44 EAP-TLS Authentication with Azure Intune Compliance
35:29 EAP-TTLS+PAP Authentication in ISE 3.0 (no GUID for Intune)
36:31 EAP-TLS Authentication with Azure AD Authorization with Intune Compliance in ISE 3.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 07:54 PM
Azure does not currently have a native cloud-based PKI solution. The certificates would need to be enrolled for the users by Intune integrated with either your on-prem Active Directory Certificate Services (ADCS) or another solution like SCEPman.
You might also review this blog discussion the available options and supported flows with ISE and Entra ID.
Cisco ISE with Microsoft Active Directory, Azure AD, and Intune
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2023 05:30 AM
Your own internal PKI generate the certificates. How you get the identity certificates to the machine is up to you. Most customers I work with use ADCA and InTune for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2025 04:04 PM
Hi @ahollifield @Greg Gibbs @thomas
Agree that Internal PKI can generate the cert. Who can generate the CSR for PKI to create the cert ?
and also can you share the certificate parameter ( client auth , server auth , EKU , Cipherment etc ) need to be used during csr creation for user or device cert ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2025 04:39 PM
The CSR generation is all part of the SCEP flow. This is typically done using an MDM or some other SCEP proxy solution.
The options for identity lookup (user=UPN, device=DeviceName or DeviceID) are all discussed in my blog previously shared (https://cs.co/ise-entraid). You would need to look at how you craft the certificates to suit your specific environment.
Only client auth is typically required for client-side certificates. You can see an example in my example using Intune and MS Cloud PKI.
https://community.cisco.com/t5/security-knowledge-base/cisco-ise-with-microsoft-cloud-pki/ta-p/5198483
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2023 10:12 AM
The OAuth-ROPC method is only used for username+password based authentication over EAP-TTLS+PAP.
EAP-TLS user certificate-based authentication is authenticated by ISE based on any certificate authentication profile then an Azure AD group lookup is done separately for the User Principle Name (UPN) in the certificate. See Configure Cisco ISE 3.2 EAP-TLS with Microsoft Azure Active Directory
Consider watching our ISE Webinar that covers this topic and more:
▷ ISE Integration with Intune MDM 2022/08/02
28:25 EAP-TLS Authentication to AD : computer or user) (traditional 802.1X with AD)
30:06 TEAP(EAP-TLS) Authentication in ISE 2.7+ for computer+user (EAP-Chaining)
33:33 EAP-TLS Authentication with Hybrid AD+Azure Compliance
34:44 EAP-TLS Authentication with Azure Intune Compliance
35:29 EAP-TTLS+PAP Authentication in ISE 3.0 (no GUID for Intune)
36:31 EAP-TLS Authentication with Azure AD Authorization with Intune Compliance in ISE 3.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2023 11:13 PM
The OAuth-ROPC method is only used for username+password based authentication over EAP-TTLS+PAP.
==> Yes, we already try following method for EAP-TTLS (which is only using username+password).
for Windows Machine (10,11) & Android, we're able to use the method,
but unfortunately when we try on Apple Device (Macbook & iPhone), we cant use it EAP-TTLS (no option on Apple, for user to choose EAP-TTLS)
We try to explore another Way how to implement 802.1x with Azure that all device supported.
and now we try using EAP-TLS,
I'll try to check first from the video you've shared.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2023 07:54 PM
Azure does not currently have a native cloud-based PKI solution. The certificates would need to be enrolled for the users by Intune integrated with either your on-prem Active Directory Certificate Services (ADCS) or another solution like SCEPman.
You might also review this blog discussion the available options and supported flows with ISE and Entra ID.
Cisco ISE with Microsoft Active Directory, Azure AD, and Intune
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide