- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: EAP-TLS cert. authentication is not working by the cert. signed by window enterprise CA.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 07:27 PM
The background is the end devices PC would like to use EAP-TLS for 802.1x wired auth. by the cert. signed by window CA.
When the cert. signed by window standalone CA, it is working fine.
However, when the cert. signed by window enterprise CA. it was failed.
As the Production environment is using window enterprise CA that it is necessary.
Any specific setting is needed in ISE to compatible to window enterprise CA?
The detail config. information of the ISE setting can refer to below post:
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 07:17 PM - edited 06-07-2020 09:30 AM
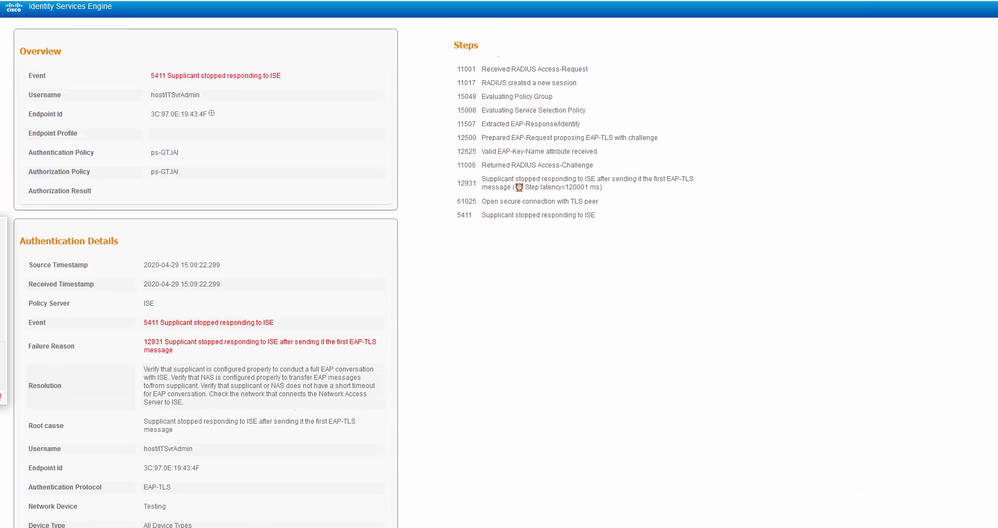
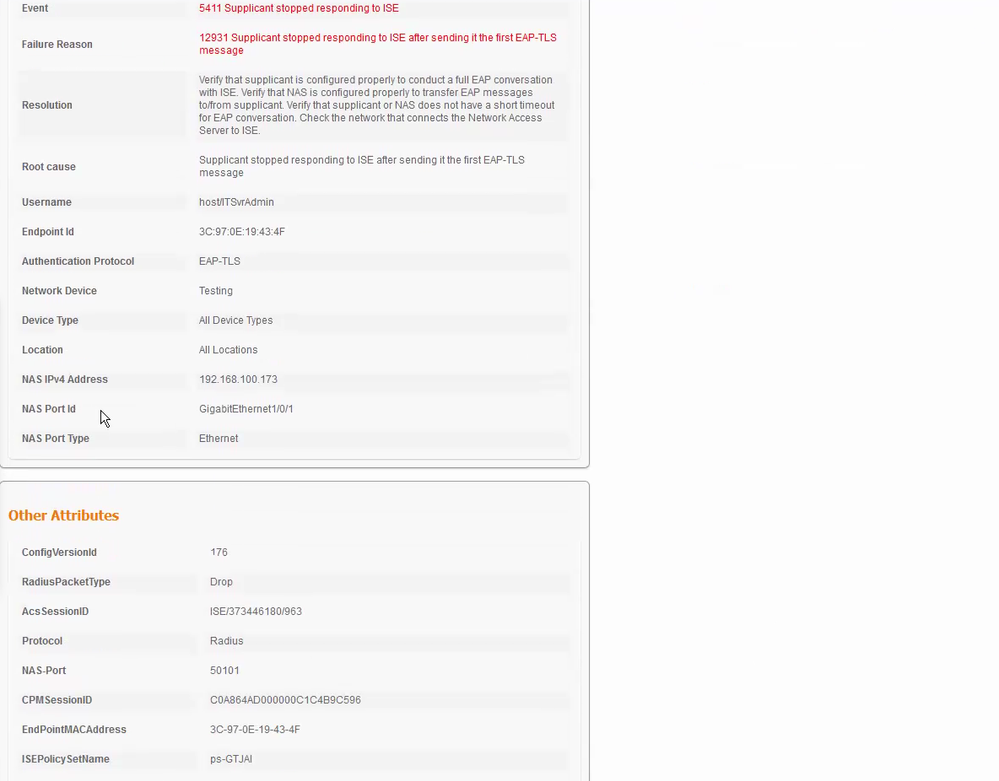
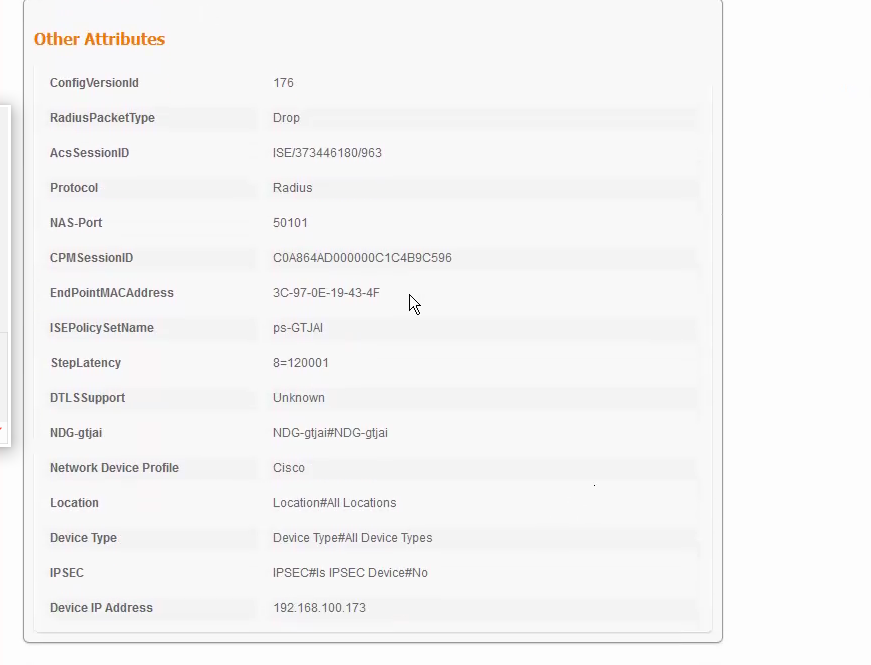
From the ISE detailed report, it seems the endpoint not presenting any client certificate at all. This usually happens when the 802.1X supplicant is not able to locate a usable client certificate.
I would suggest you to check the certificate template used to issue the client certificates. Usually we duplicate the built-in template for Users/Computers and modify the duplicate to fit our need. The client certificate usually need carry the usage for client authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 09:08 PM
Does your ise have the pki certificates installed in its trusted store?
How your client is configured?
Can you share the ise logs please?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 01:32 AM
If you do have the trusted certifciates in ISE I would check your client configuration. When setting up your client, if you're using the native Windows supplicant under Authentication > Settings, you can select the root that you trust. Are you trusting the one that's working but not the other?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 07:46 AM
For more information, below as the ISE live log.
Switch config:
aaa group server radius gp-ISE
server name ISE
!
aaa group server tacacs+ group-ts-ISE
server name ts-ISE
!
aaa authentication login default group group-ts-ISE local
aaa authentication enable default group group-ts-ISE enable
aaa authentication dot1x default group gp-ISE
aaa authorization exec default group group-ts-ISE local
aaa authorization commands 0 default group group-ts-ISE local
aaa authorization commands 1 default group group-ts-ISE local
aaa authorization network default group gp-ISE
aaa accounting auth-proxy default start-stop group gp-ISE
aaa accounting dot1x default start-stop group gp-ISE
aaa accounting exec default start-stop group group-ts-ISE
aaa accounting commands 0 default stop-only group group-ts-ISE
aaa accounting commands 1 default stop-only group group-ts-ISE
aaa accounting commands 15 default start-stop group group-ts-ISE
!
aaa server radius dynamic-author
client 192.168.100.240 server-key 7 xxxxxxxxxxxxxxxxxxx
server-key 7 xxxxxxxxxxxxxxxxx
!
aaa session-id common
!
dot1x system-auth-control
dot1x critical eapol
errdisable recovery cause bpduguard
errdisable recovery cause loopback
errdisable recovery interval 180
license boot level ipservicesk9
diagnostic bootup level minimal
!
interface GigabitEthernet1/0/1
switchport access vlan 100
switchport mode access
ip arp inspection limit rate 100
authentication event fail action next-method
authentication open
authentication order dot1x
authentication priority dot1x
authentication port-control auto
dot1x pae authenticator
spanning-tree portfast
!
ip radius source-interface Vlan100
ip sla enable reaction-alerts
logging history size 50
logging history debugging
logging origin-id ip
logging facility local2
logging source-interface Vlan100
logging host 192.168.100.240
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
!
radius server ISE
address ipv4 192.168.100.240 auth-port 1645 acct-port 1646
key 7 xxxxxxxxxxxxxxxx
!
!
Any hits for the ISE live log?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 07:17 PM - edited 06-07-2020 09:30 AM
From the ISE detailed report, it seems the endpoint not presenting any client certificate at all. This usually happens when the 802.1X supplicant is not able to locate a usable client certificate.
I would suggest you to check the certificate template used to issue the client certificates. Usually we duplicate the built-in template for Users/Computers and modify the duplicate to fit our need. The client certificate usually need carry the usage for client authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 06:45 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2020 06:47 AM
Hi @TerryLaw86466 ,
It seems you are doing Machine authentication. Username - host/ITSvrAdmin.
Please make sure the entire CA chain (Intermediate, Root) of ISE certificate is trusted in the Machine account (not User account), check Trusted Root Store.
Similarly, the Machine should be sending a certificate from its Personal Certificate Store from the Machine Account. And that certificate's Intermediate and Root should be present on ISE's Trusted Certificate Store.
Open Windows Start/Run and type mmc and then plug in Certificates for the Local Machine.
Please 'RATE' and 'MARK ACCEPTED', if applicable.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide