- Cisco Community
- Technology and Support
- Security
- Network Access Control
- EAP-TLS error on Apple OSX
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2019 03:53 AM
Hi,
I am trying to authenticate OSX clients with EAP-TLS on WiFi.
ISE and OSX has certificates from different issuing-certificate-servers but they share root-server.
ISE is in domain.com and OSX in sub.domain.com
The error I am getting in ISE is "12521 EAP-TLS failed SSL/TLS handshake after a client alert". My best guess is that OSX doesnt trust ISE, but I can't figure out what settings I have to do to get it to work.
We are using a MDM tool to deploy profiles to the OSX devices.
Have any one of you got info on what settings I have to do in OSX for it to trust ISE that has RADIUS-cert from another cert-server?
Regards
Philip
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 10:46 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 07:32 PM
Have any one of you got info on what settings I have to do in OSX for it to trust ISE that has RADIUS-cert from another cert-server?
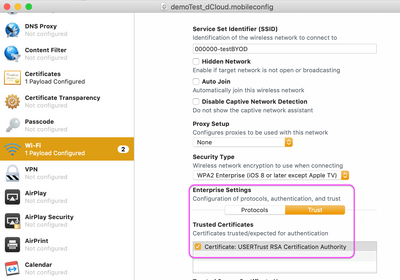
In case of ad-hoc connections, macOS should have prompted the users to trust the certificate(s). For non-ad-hoc, a MDM usually is used to provision the trust and you would need to consult the admin guide of the MDM product.
For my own testing, I am using Apple Configurator 2 to create a configuration profile, which may contain the certificate chain used by ISE and explicitly trusted for a network payload.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 10:46 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide