- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: EAP-TLS,SCEP failing with Windows 10 11514 Unexpectedly received e
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2023 07:25 AM
Hi,
I've been working on a setting up an EAP-TLS wireless auth in Cisco ISE 3.2 for mix of domain joined and Autopilot machines.
At first I focused on machine authentication...I know it's not the easiest and not a best practice to set this up for AAD joined devices.
ISE is a lab setup (single node with all personas), but it's integrated with AD, its cert (used for Admin, EAP, Portal etc.) is signed by our Intermediate CA.
For domain joined laptop (W10) with an old NPS certificate for Client Auth. EAP-TLS authentication works like charm.
But Autopilot machine could not authenticate to the same SSID.
For Autopilot I've asked the guys managing our PKI/Intune to follow the guides and they've configured the NDES/Azure App Proxy, Intune Connector, configured Cert. Template and deployed SCEP cert. via Intune profile to test machines.
Cert looks good, at first sight...I tried to be changing stuff in it, making sure the config match the certificate template, but no difference in wireless authentication.
Also Root and Intermediate certs have been pushed to the Autopilot client with a help of Intune.
Whatever ISE policy and whatever CAP I've tried the client could not pass the Authentication phase.
I'm getting a error:
5400 Authentication failed
11514 Unexpectedly received empty TLS message; treating as a rejection by the client
Now, it's hard to vouch for the certificate template config...basic checks not revealed any discrepancies from the guide, but I can't vouch for it.
I'm trying to rule out the the issue of a client failing to trust the ISE EAP cert.
My thinking was, that if the same cert is being used for Admin, Web Portal and EAP, I can validate the trust by opening WE GUI of ISE on the test Autopilot machine - this reveals no errors, machine trust the ISE Gui webpage and cert assigned.
Question 1. Is this a proof, that machine should also trust ISE EAP certificate?
From the other hand, I was trying to test with the same SSID, also supporting EAP-PEAP with MsChapv2, as in this case client should also trust ISE EAP cert.
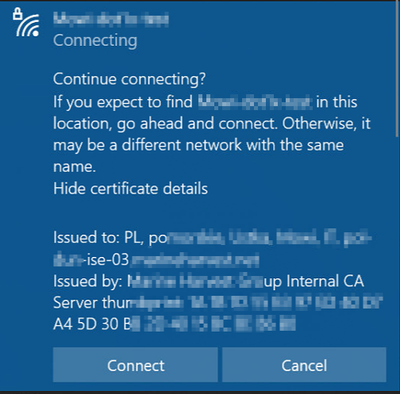
And when I do not pre-configure Wireless Profile on Windows, but just try to connect, I'm being prompted for Username and password. When I provided valid AD creds, I got a certificate warning:
Question 2: Does that warning proves, that client does not trust ISE certificate?
Because when I do pre-create a profile (still for PEAP with Mschapv2) and select Root CA, that provide trust to ISE, it allows me to connect without any certificate warning.
I hope you guys could point me out to some direction, as I'm quite fed up with this Autopilot/SCEP authentication
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2024 08:02 AM
Have you checked option number 37?!
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide