- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Error SSL Mobile Wildcard ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Error SSL Mobile Wildcard ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 11:51 PM
Hello
My Wildcard certificate was renewed. After of this PC, the connections are fine; the mobile device is the issue
- Labels:
-
Guest
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2023 05:29 AM
Renewed with the proper SAN fields? Wildcard present in the SAN also?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2023 03:13 AM - edited 12-01-2023 03:15 AM
Hello, @ahollifield I appreciate your response.
I generated the certificate via ISE and entered the same data as the previous certificate. I presume that if you have a wildcard certificate, do you also need to enter SAN fields? Nevertheless has SAN this wildcard
I don't get why a wildcar, like *.midominio.com, needs a SAN. If you follow mydomin.com, all entries should be validated.
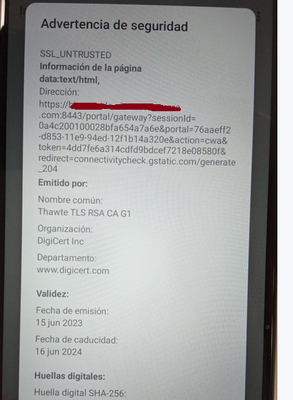
This is the certificate
ISE SIDE for portal
Mobile this ssl no trust only in mobile
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2023 04:48 AM
Yes this all seems correct. The wildcard must also have the wildcard in the SAN field. Are you sure the spelling of the domain is the same? Is the mobile device time/date correct? What version of Android? All other devices trust this certificate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2023 12:52 AM
Hi there @ahollifield
I apologize for the delay just to reply me today response.
iPhone It's ok no problem ; the mistake is in the Android mobiles; he attempts to use Android 12 as an example.
I am watching the firs words is bienvenido.xxxxxx.
May be in this case i woukd have to put a SAM bienvenido.xxxxx .
For solve this problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2023 06:16 AM
The mobile device which os it run?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2023 12:52 AM
Hhey
iPhone It's ok no problem ; the mistake is in the Android mobiles; he attempts to use Android 12 as an example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2023 03:16 AM
Hey any idea ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2023 05:12 AM
My guess is the Digicert/Thawte root/intermediate CAs are not trusted on that model/version of Android. Try a different Android client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2023 03:48 PM
@athan1234 : Adding to @ahollifield , please check the complete certificate chain and, if needed, take packet capture and use WireShark or the like to verify. And check the root CA against the list of trusted certificates on the Android OS.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide