- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Firewall Ports Between Supplicant and ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2023 12:36 PM
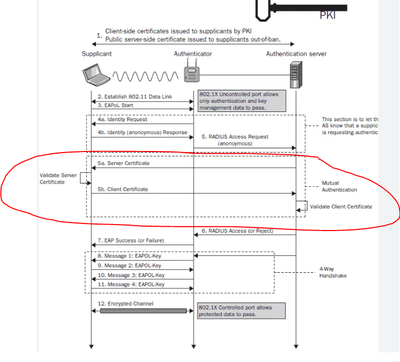
Do we need to allow any direct communication between ISE and the supplicant? On what port number?
I know its radius between the authenticator and ISE ports 1812 and 1813
but from the drawing below, there looks like traffic between the clients and ISE? what port number please?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2023 12:50 PM
You can check this guide for reference. There a few ports you may need to allow depending on the services you provide with ISE.
|
Web Portal Services: - Guest/Web Authentication - Guest Sponsor Portal - My Devices Portal - Client Provisioning - Certificate Provisioning - BlackListing Portal |
HTTPS (Interface must be enabled for service in Cisco ISE):
|
|||
|
Posture - Discovery - Provisioning - Assessment/ Heartbeat |
|
|||
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2023 12:45 PM - edited 07-18-2023 03:04 PM
There is no any kind of connection between client and ISE'
The client send to SW or WLC EAPoL
The SW/WLC will encapsulate it with radius message and send to ISE.
So only 1813/1812 (use SE/wlc ip as source ) what you need.
Only case that client connect to ISE is CWA ISE portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2023 12:50 PM
You can check this guide for reference. There a few ports you may need to allow depending on the services you provide with ISE.
|
Web Portal Services: - Guest/Web Authentication - Guest Sponsor Portal - My Devices Portal - Client Provisioning - Certificate Provisioning - BlackListing Portal |
HTTPS (Interface must be enabled for service in Cisco ISE):
|
|||
|
Posture - Discovery - Provisioning - Assessment/ Heartbeat |
|
|||
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2023 01:06 PM
@Flavio Miranda I need only client authentication using either EAP-TLS or MSCHAPv2.
Is there any ports required from the client to ISE for that? I don't see that in the design so I'm assuming no. please confirm.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2023 01:34 PM
No direct communication to ISE, supplicant talks to authentication over EAP and authenticate talks to authentication server (ISE) using radius.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2023 02:59 PM
For radius only, no need to open port between ISE and client
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide