- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: How to auhorize IP Phones withouth ISE Plus licences
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2021 02:43 AM
Hi to all,
i would like to know if there is a safe way to categorize Cisco IP phones with a seperate (from PCs) authorization po;icy but without the use of ISE PLUS licences.
Is that possible?
For example :
IP Phone with MAB --> Voice Domain by using an authorization policy X
PCs behind IP phones (with MAB also) --> Data domain by using a seperate Authorization Policy Y
Is that possible without ISE PLUS licences?
Thanks,
Ditter.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2021 07:29 PM
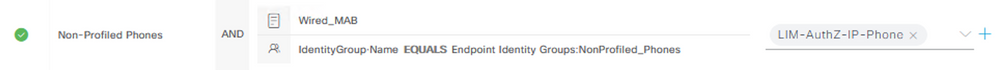
As @thomas mentioned, the only other option would be to use a static Endpoint Identity Group. You would need to create a new EIG under Administration > Identity Management > Groups > Endpoint Identity Groups.
You would then create an AuthZ Policy that uses that EIG as a matching condition; for example:
Once the policy elements are configured, you would need to add/update the endpoints in Context Visibility to associate them with that Static Group Assignment. This can be done manually, via CSV/LDAP import, or using the API.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2021 04:06 PM
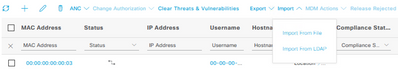
Correct... you can not import bulk Endpoint Identity Groups, but that's not what you are looking to do. You only need to create one new EIG for your Non-Profiled phones and use the 'Import from file' option in Context Visibility > Endpoints to add/update the EIG associated with your phones.
If you are not sure what fields need to be updated on the endpoint, you can select one of your phones and manually edit the Attributes to enable the Static Group Assignment and select the EIG you created. You can then Export that selected endpoint to look at the values in the 'IdentityGroup' and 'StaticGroupAssignment' fields.
You can then use the 'Import from file' CSV template to add all of your phone MAC addresses and specify the values for the fields you want to update. If the endpoints already exist in Context Visibility, they will be updated. If they don't, they will be created.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2021 03:42 AM
Profiling only categorizes endpoints automaticaly.
When you categorize endpoint manualy (MAC address to endpointgroup IP_phone), you can authenticate endpoint using MAB.
MAB AuthC >> IP_phone group >> Authorization policy (ISE has default IPphone policy with attributes that are reqired to corectly set ipphone to switchport voice vlan domain).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2021 08:05 AM
Thanks for the answer.
As i see it i could create a static pool of endpoints that are all cisco ip phones and use this for authentication.
But the problem as i see it is in the authorization portion:
As i have no ISE Plus licences i am trying to authorize the cisco IP phones with a way that consumes only base license and put them in the voice domain.Finally my PCs behind the Cisco IP phones should get in the data domain.
I used the default ISE policy for IP Phones (the one IdentityGroup·Name EQUALS Endpoint Identity groups:profiled:cisco-ip-phone but i noticed that the phone still consumes a base + plus license.
Any proposals?
Thanks again,
Ditter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2021 06:56 AM
You are consuming Plus license becose of this
Endpoint Identity groups:profiled:
Use olny identity group you manualy created for MAC addresses of IP Phones. NOT PROFILED (it requires PLUS Lic)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2021 11:52 AM
1) authenticate your phones with username/password or certificates
2) authenticate with a static MAB identity group
Either of these methods counts only a Base/Essentials license for basic AAA/802.1X.
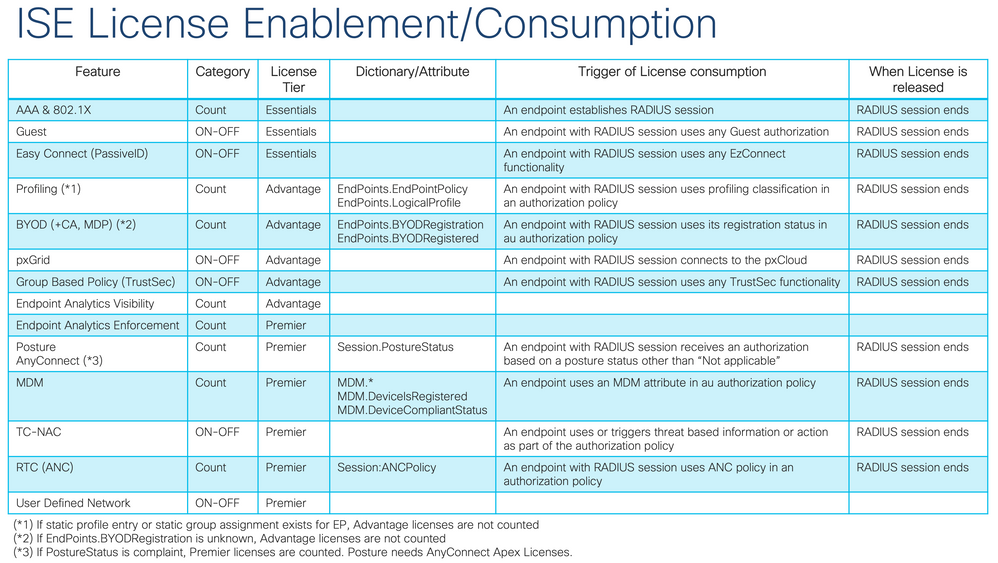
Here is a summary of ISE licensing and which attributes trigger consumption of Plus/Advantage licenses from this week's ISE Webinar. Look for it to be posted on our ISE YouTube channel next week for more licensing info.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2021 12:15 PM
Thanks Thomas, currently i am using MAB.
So my question is the following:
My problem is not the authentication but the authorization and more specifically to assign the IP Phones to the voice domain.
Can you propose an authorization policy condition i could use in order to pass the suitable authorization profile that assigns the phone to voice domain?
From what i found out thus far is that i can assign ip phones to voice domain only if i use an authorization policy condition that is based is some kind of profiling. Any other policy condition leads to the phone being in data domain.
Thanks,
Ditter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2021 07:29 PM
As @thomas mentioned, the only other option would be to use a static Endpoint Identity Group. You would need to create a new EIG under Administration > Identity Management > Groups > Endpoint Identity Groups.
You would then create an AuthZ Policy that uses that EIG as a matching condition; for example:
Once the policy elements are configured, you would need to add/update the endpoints in Context Visibility to associate them with that Static Group Assignment. This can be done manually, via CSV/LDAP import, or using the API.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2021 04:22 AM
Greg, ISE 3.9 does not seem to have an import feature for bulk update of a new EIG. Although there is an import feature for UIG, there is not such feature for EIG.
Is that correct?
As these endpoints do not exist in LDAP, i could only import them via API.
Please see attached PNGs.
Thanks, Ditter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2021 04:06 PM
Correct... you can not import bulk Endpoint Identity Groups, but that's not what you are looking to do. You only need to create one new EIG for your Non-Profiled phones and use the 'Import from file' option in Context Visibility > Endpoints to add/update the EIG associated with your phones.
If you are not sure what fields need to be updated on the endpoint, you can select one of your phones and manually edit the Attributes to enable the Static Group Assignment and select the EIG you created. You can then Export that selected endpoint to look at the values in the 'IdentityGroup' and 'StaticGroupAssignment' fields.
You can then use the 'Import from file' CSV template to add all of your phone MAC addresses and specify the values for the fields you want to update. If the endpoints already exist in Context Visibility, they will be updated. If they don't, they will be created.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2021 11:52 PM
Thanks so much Greg. I will give it a try asap.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2021 08:41 AM - edited 06-27-2021 08:45 AM
Hi Greg
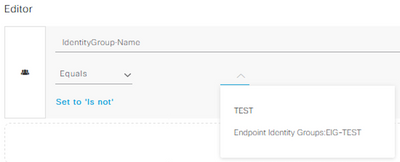
i stuck with configuring condition IdentityGroup:Name EQUALS Endpoint Identity Groups.
When i select Attribute IdentityGroup:Name i cannot find Endpoint Identity Groups in selection tree to assign specific value to attribute. I can use specific Identity Group membership with selecting it from Endpoint Groups suggested in selection tree as very 1st condition (this one coming after IF) but no with referred approach. Any help pls? SW 2.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2021 12:22 AM
The example I shared is using the newer Policy Set structure with the Conditions Studio that was introduced in ISE 2.3. I don't have an instance of ISE 2.1 (and this version has been End of Support since March 2020) to reference.
The approach you mention is the way an Endpoint ID Group was configured in that version.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2021 01:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2021 04:51 PM
If you have created the Endpoint Identity Group under Administration > Identity Management > Groups > Endpoint Identity Groups, then it should show up in the Conditions Studio. This screenshot is from ISE 3.0 patch 2.
If you're not seeing it, you might first try clearing your browser cache or using another browser. If that's not the issue, you could be running into a bug. I would suggest opening a TAC case, but ISE 2.3 has been End of Support since June 2020.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2022 05:11 AM
Hi,
i have tried this but it wouldnt work. what have you specified in the LIM-AUTHZ-IP-Phone?
Regards,
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide