- Cisco Community
- Technology and Support
- Security
- Network Access Control
- How to setup TACACS+ single-connect properly and safely
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to setup TACACS+ single-connect properly and safely
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2024 02:27 PM
Hello
DNAC/Cat Center is a very chatty product and it's constantly logging into devices to run many show commands.
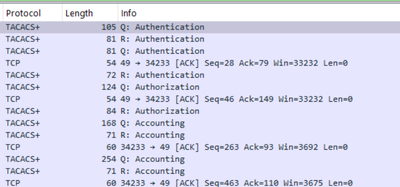
Without single-connect, there will always be a 3-way TCP handshake for every command issued when command authorization is enabled. Below is a Wireshark of a DNAC provisioned device, and executing a few successive show commands:
That made me think that perhaps it's time to investigate TACACS+ single-connect mode to lessen the network latency and make this setup run more efficiently. Below is the same thing with single-connect enabled:
I just haven't found a good technical guide that ties all the pieces together in such a way that I can make informed decisions - hoping that others can chime in and help me with the missing pieces below ...
In ISE, a DNAC provisioned IOS-XE device looks like this, which makes you believe you are running single-connect:
But the IOS-XE config generated by DNAC produces the config that does not enable single-connect, hence, single-connect is not actually running:
tacacs server dnac-tacacs_172.22.131.174
address ipv4 172.22.131.174
key 7 ******************
timeout 4
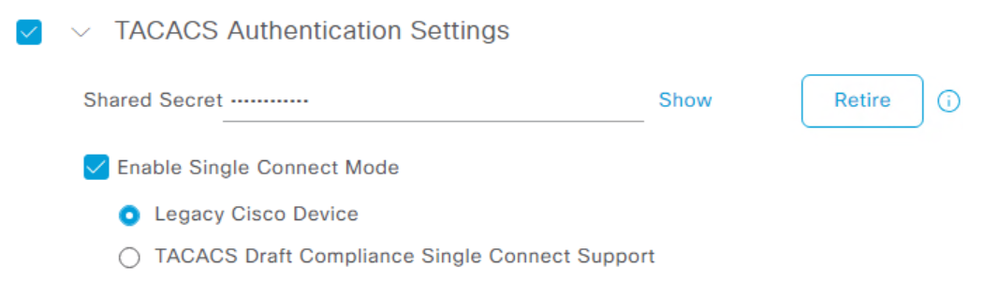
To activate single-connect mode, you must add the 'single-connection' key word to the IOS-XE config:
tacacs server dnac-tacacs_172.22.131.174
address ipv4 172.22.131.174
key 7 *************
timeout 4
single-connectionI can see the results in Wireshark.
I have read various articles that say "use legacy", and others say "use TACACS Draft Compliance Single.." - but I am looking for a technical answer to what the differences are, and what the implications are of using either. In Wireshark I could not see any differences.
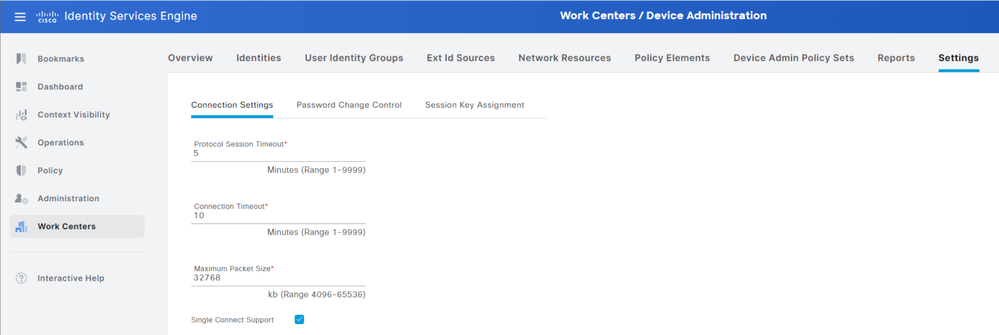
The other thing is, what is the TCP connection limit in ISE? I have read 5000. Is that per PSN? Can it be increased?
Let's say it's 5000. If you have more than 5000 devices managed by DNAC, you might run into issues, unless you tune the TCP idle settings, such that the sessions are cleared after DNAC sends its torrent of commands to a device. Perhaps, instead of the 5 min idle time, make it 1min?
Assuming you have enough TCP connections in your ISE nodes, and DNAC polls a device every 10 minutes, then we should tune ISE such that it keeps the connection alive longer than the DNAC polling interval (e.g. 11min).
But does that relate to the Session Timeout, or the Connection Timeout?
One would most likely enable single-connect for each device type (e.g. IOS-XE version) to ensure that it's behaving as expected, before rolling out across the entire network. And also bearing in mind, that I am asking this from the perspective of a network that is managed by DNAC. If there is no regular network polling involved (i.e. just humans randomly logging into devices ad-hoc), then I don't really care about single-connect.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2025 05:48 AM
Arne, as usual you are already on the case of our latest problem. We just crashed an ISE TACACS server (only TACACS in this deployment). We've noticed since DNAC/Cat Center that the PAN (also a PSN persona) had slowed and then the PAN filled the /opt directory. We swapped around the servers in the deployment and reworked the original PAN and things are back to normal, for now.
We are looking at our environment again and wondering about single-connect (which burnt us in the distant past). But like you say, there is not really a good technical guide that ties all the pieces together in such a way that we can make informed decisions.
Hello Cisco. Is it there and we are missing it? Or is the documentation just missing?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide