- Cisco Community
- Technology and Support
- Security
- Network Access Control
- I suffering a strange issue ACS 4.2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
I suffering a strange issue ACS 4.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2012 12:56 PM - edited 03-10-2019 07:28 PM
Hi Guys
I suffering a strange issue , I have two group users (wireless user , VPN users),
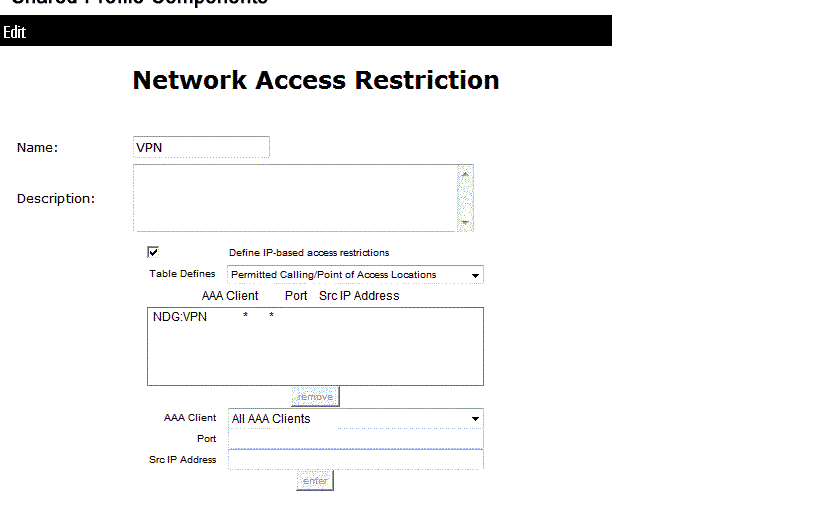
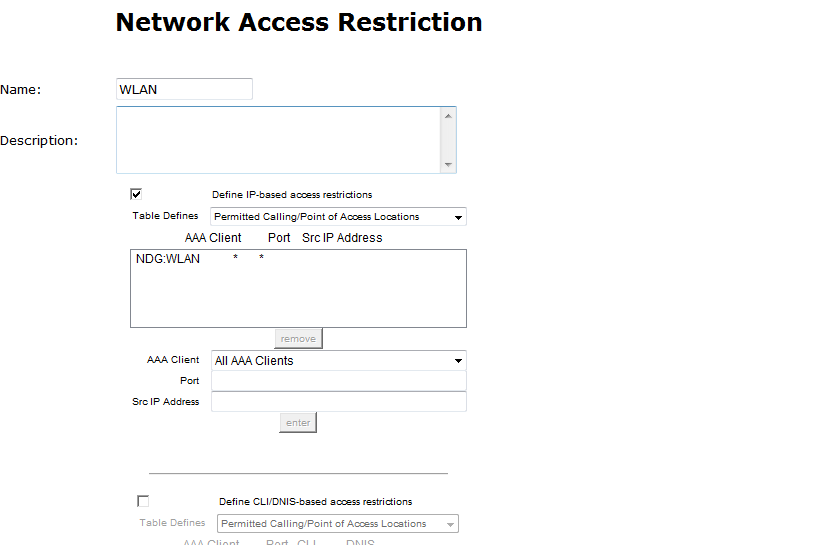
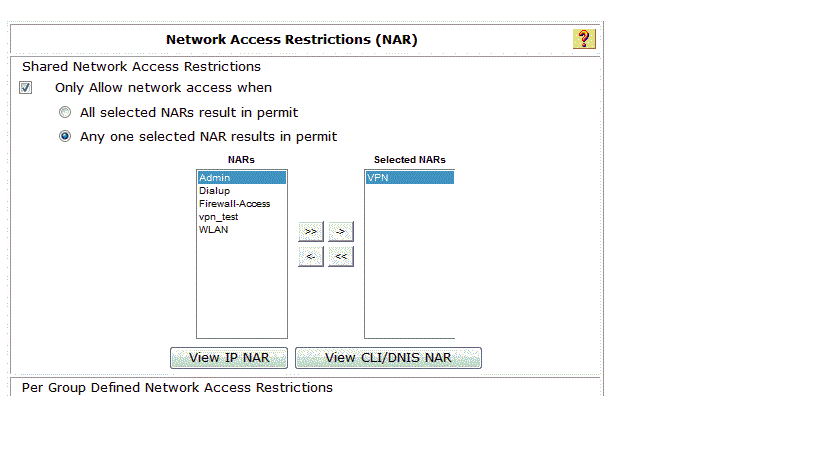
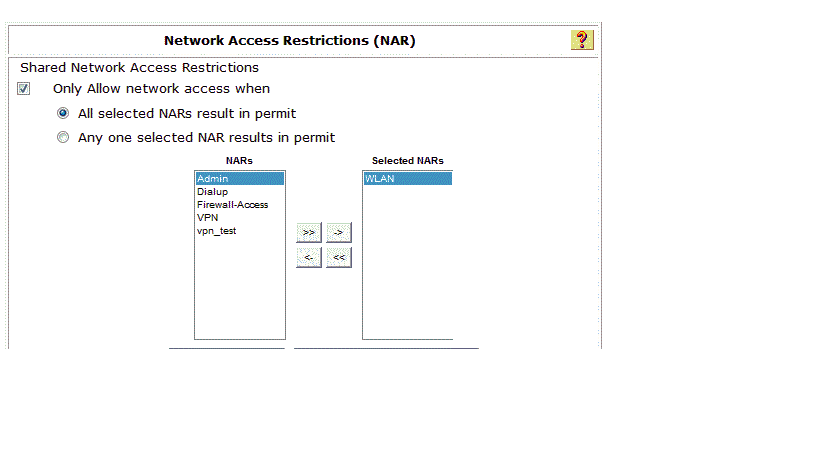
- I created a NAR To restrict users,, created two group NAR (network access restriction ) wirless group and vpn group
- I attached wireless NAR group to wireless group user , and attached VPN NAR group to VPN group users ,
Supposed Wireless users only have access to wireless ,and VPN users just have access to connect VPN and they don’t have access wireless .
The issue VPN user can access wireless!!!!!
Notice I used ACS4.2 And Aruba controller
Is this bug in ACS 4.2 or what ? please advice
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2012 12:39 AM
Hi,
NAR are based on two radius attributes (calling-station-id = client information) (called-station-id = network device information).
The issue is based on the VPN NAR that you have configured.
However let me explain why this works for the WLAN users, you configured an IP based rule (dont know if this was intentional but it works), in a way that if a client authenticates with the calling-station-id from the VPN server (ip address is the format for calling-station-id), that it must match the called-station-id that belongs in the "NDG-WLAN" which fails. I noticed that you do not have a DNIS condition configured, the ACS is designed to failover to this rule for non IP based NAR filters. For wireless dot1x authentication (calling-station-id is the mac address of the client), there is no CLI/DNIS based rule enabled so that is why the wireless requests are permitted.
When the VPN users connect to wireless an hit the VPN NAR, the calling-station-id is a mac address format, and with no CLI/DNIS rule configured you allow them access.
In the VPN NAR, you should create a DNIS based rule which denies access from the NDG:WLAN and wildcard the dnis field, and that will fix your issue.
Here is some reference material:
"IP-based NAR filters work only if ACS receives the Radius Calling-Station-Id (31) attribute. The Calling-Station-Id (31) must contain a valid IP address. If it does not, it will fall over to DNIS rules."
Thanks,
Tarik Admani
*Please rate helpful posts*
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2012 01:20 AM
Tarik :You are always the man when it comes to AAA. +5 my friend.
I would also add that called-station-id format is "AP_Mac_address:SSID".
so suppose that radio mac address of your SSID is 11:11:11:11:11:11 and your SSID is Test the called-station-id will be 11:11:11:11:11:11:Test
keeping this in mind, when you create CLI/DNIS access restriction filter, you need to provide one entry for every signel SSID that you have and want to allow the users to.
You can use wildcards (* for example) if you want to allow the users to all APs.
To allow client access on all APs on SSID Test then you need to configure the DNIS as *Test.
You look into this config example and it will certainly help you:
HTH
Amjad
Rating useful replies is more useful than saying "Thank you"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide