- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Identity PSK Questions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2018 02:20 PM
Team,
I have a customer that is looking to reduce the number of SSIDs and create some control around their PSK networks. The customer's network is an educational network (university) that hosts many networks across many different endpoints (around 80k). The client is looking at IPSK but were under the assumption that it would operate much like the Ruckus' iteration of DPSK, however that isnt the case.
We looked at many options and it seems as if the av-attribute doesnt allow you to reference a dynamic condition such as an AD attribute. The goal of the solution that i have in mind is to create a policy that references the AD attribute and have users register their device through the device registration portal, but echo back the client's AD attribute that is unique to them as their PSK. Zero touch is preferred but device registration is acceptable.
Is there a feature request or a solution that someone could walk me through, the goal of this exercise is to reduce the risk of the PSK and also reduce the number of ISE authorization profiles/policies to create in order to support this.
Thanks,
Tarik A.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 04:15 AM
Right now the closet to integration we have is the following. We are working on a More integrated approac but can’t discuss futures here in the forum. Please get your use case and opportunity info to the ISE product management team thru the sales channel
https://communities.cisco.com/docs/DOC-77607
We will also evaluate what you have here to see if there is an approach with AD but right now but I don’t understand how you are seeing this work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 04:15 AM
Right now the closet to integration we have is the following. We are working on a More integrated approac but can’t discuss futures here in the forum. Please get your use case and opportunity info to the ISE product management team thru the sales channel
https://communities.cisco.com/docs/DOC-77607
We will also evaluate what you have here to see if there is an approach with AD but right now but I don’t understand how you are seeing this work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 12:46 PM
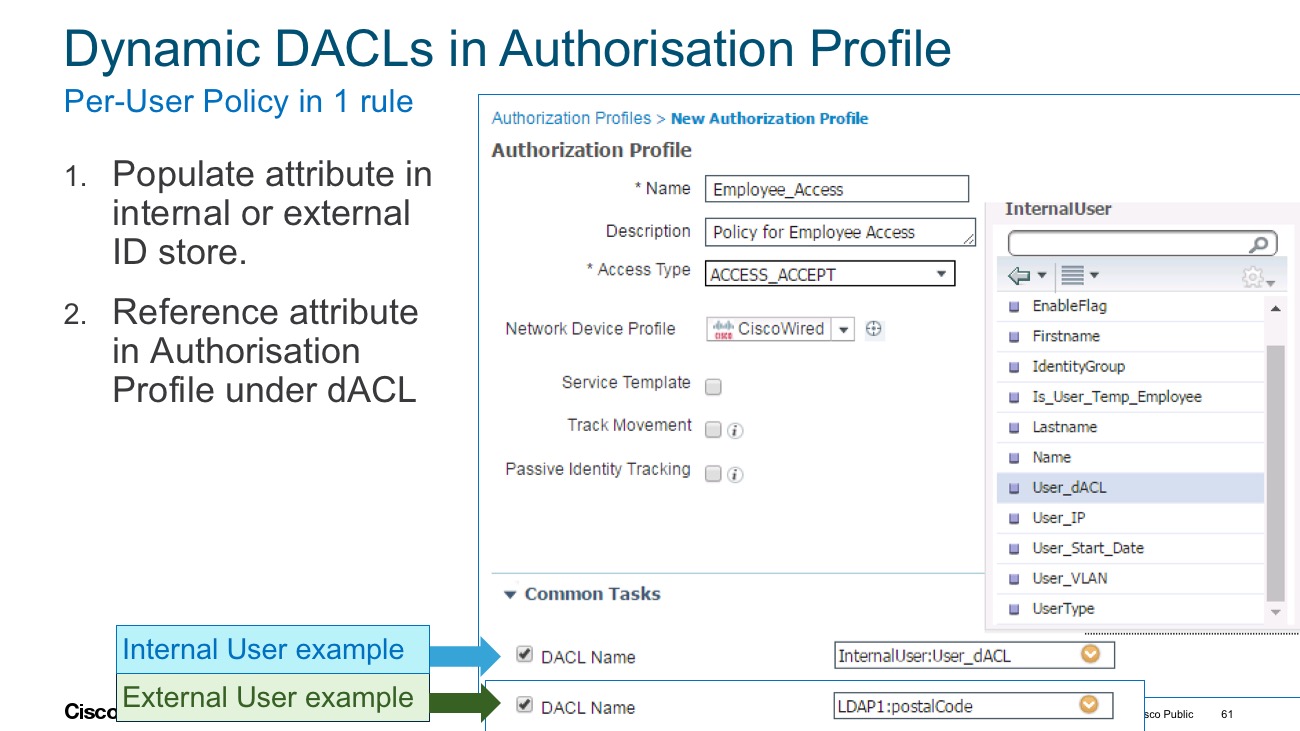
Thanks for the response Jason, much like the workflow and authentication policy when checking the SAN attribute for ISE provisioned certificates (where SAN=Calling-station-id), i was hoping for an authorization profile that can provide a dynamic attribute versus static attribute where the ascii value can be an attribute in AD. Here is the video that shows an example of authentication work flow -
Dynamic Attribute with ISE: MAC Address Matching
basically looking for this return attribute -
cisco-av-pair=psk=$ADattributevalue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 01:17 PM
like something like this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 03:35 PM
Yes sir, thats what i am looking for.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 04:08 PM
Let me know if this works out for you maybe we can share some knowledge
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 04:32 PM
Sorry, that is the model i am looking for, I guess we will need to lab this out and see what we can come up with. I looked at the document you provided, is there a way where we can leverage API integration so that when a device registers through an external API that the description can be leveraged much like the example you brought up?
Device registers using an external API integration + ISE then create a random attribute and injects that inside the custom attribute we create for the endpoint?
Thanks,
Tarik A.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2018 05:14 PM
Yes you should be able to do that with api integration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2018 08:27 PM
Jason,
So far so good, we are able to send the custom attribute with the API and even update existing records or create new ones. The customer is working on their end to code the webtop but this looks very similar to the DPSK feature that we were looking for.
Once we get it final, we can sync up and share notes.
Thanks.
Tarik A.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

