- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 1.1 - switch ignores "Session-Timeout"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2012 12:40 AM - edited 03-10-2019 07:07 PM
hi all,
I'm playing around with ISE guest service and have some difficulty with Time Profiles.
After guest logs in, Radius attributes are sent to the switch (3750G) one of them is Session-Timeout which should be similar to 1h (DefaultOneHour)
According to ISE logs and switch debugs, ISE did it well and this attribute was sent but it seems that the switch simply ignores it.
May 24 07:03:11.658: %SEC-6-IPACCESSLOGP: list ACL-DEFAULT denied udp 10.1.100.194(1029) -> 10.1.100.2(389), 1 packet
19:46:57: RADIUS: COA received from id 36 10.1.100.6:64700, CoA Request, len 183
19:46:57: RADIUS/DECODE: parse unknown cisco vsa "reauthenticate-type" - IGNORE
19:46:57: RADIUS/ENCODE(00000000):Orig. component type = Invalid
19:46:57: RADIUS(00000000): sending
19:46:57: RADIUS(00000000): Send CoA Ack Response to 10.1.100.6:64700 id 36, len 38
19:46:57: RADIUS: authenticator 0B 30 6E 9B DF 97 0D A0 - D9 8B A5 5A 11 39 3E 41
19:46:57: RADIUS: Message-Authenticato[80] 18
19:46:57: RADIUS: 11 42 82 E2 52 68 DF 28 CD 43 AE 88 0C 5D 91 10 [ BRh(C]]
19:46:57: RADIUS/ENCODE(00000026):Orig. component type = Dot1X
19:46:57: RADIUS(00000026): Config NAS IP: 0.0.0.0
19:46:57: RADIUS(00000026): Config NAS IPv6: ::
19:46:57: RADIUS/ENCODE(00000026): acct_session_id: 27
19:46:57: RADIUS(00000026): sending
19:46:57: RADIUS/ENCODE: Best Local IP-Address 10.1.100.1 for Radius-Server 10.1.100.6
19:46:57: RADIUS(00000026): Send Access-Request to 10.1.100.6:1812 id 1645/25, len 267
19:46:57: RADIUS: authenticator 6D 92 DC 77 87 47 DA 8E - 7D 6B DD DD 18 BE DC 33
19:46:57: RADIUS: User-Name [1] 14 "0016d329042f"
19:46:57: RADIUS: User-Password [2] 18 *
19:46:57: RADIUS: Service-Type [6] 6 Call Check [10]
19:46:57: RADIUS: Vendor, Cisco [26] 31
19:46:57: RADIUS: Cisco AVpair [1] 25 "service-type=Call Check"
19:46:57: RADIUS: Framed-IP-Address [8] 6 10.1.100.194
19:46:57: RADIUS: Framed-MTU [12] 6 1500
19:46:57: RADIUS: Called-Station-Id [30] 19 "00-24-F9-2D-83-87"
19:46:57: RADIUS: Calling-Station-Id [31] 19 "00-16-D3-29-04-2F"
19:46:57: RADIUS: Message-Authenticato[80] 18
19:46:57: RADIUS: AD EB 99 4A F2 B9 4E BB 2E B3 E2 04 BE 5B 0C 72 [ JN.[r]
19:46:57: RADIUS: EAP-Key-Name [102] 2 *
19:46:57: RADIUS: Vendor, Cisco [26] 49
19:46:57: RADIUS: Cisco AVpair [1] 43 "audit-session-id=0A01280100000016043E0D23"
19:46:57: RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
19:46:57: RADIUS: NAS-Port [5] 6 50107
19:46:57: RADIUS: NAS-Port-Id [87] 22 "GigabitEthernet1/0/7"
19:46:57: RADIUS: Called-Station-Id [30] 19 "00-24-F9-2D-83-87"
19:46:57: RADIUS: NAS-IP-Address [4] 6 10.1.100.1
19:46:57: RADIUS(00000026): Sending a IPv4 Radius Packet
19:46:57: RADIUS(00000026): Started 5 sec timeout
19:46:57: RADIUS: Received from id 1645/25 10.1.100.6:1812, Access-Accept, len 272
19:46:57: RADIUS: authenticator F1 5F 57 72 FD 80 95 20 - 46 47 B5 CE DF 63 6E 1A
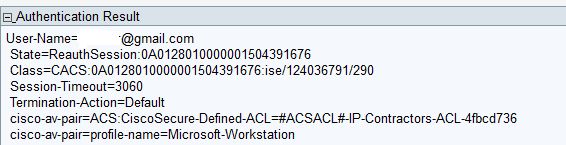
19:46:57: RADIUS: User-Name [1] 19 "xxxxx@gmail.com"
19:46:57: RADIUS: State [24] 40
19:46:57: RADIUS: 52 65 61 75 74 68 53 65 73 73 69 6F 6E 3A 30 41 [ReauthSession:0A]
19:46:57: RADIUS: 30 31 32 38 30 31 30 30 30 30 30 30 31 36 30 34 [0128010000001604]
19:46:57: RADIUS: 33 45 30 44 32 33 [ 3E0D23]
19:46:57: RADIUS: Class [25] 49
19:46:57: RADIUS: 43 41 43 53 3A 30 41 30 31 32 38 30 31 30 30 30 [CACS:0A012801000]
19:46:57: RADIUS: 30 30 30 31 36 30 34 33 45 30 44 32 33 3A 69 73 [00016043E0D23:is]
19:46:57: RADIUS: 65 2F 31 32 34 30 33 36 37 39 31 2F 32 39 37 [ e/124036791/297]
19:46:57: RADIUS: Session-Timeout [27] 6 2940
19:46:57: RADIUS: Termination-Action [29] 6 0
19:46:57: RADIUS: Message-Authenticato[80] 18
19:46:57: RADIUS: 26 46 2C B6 75 95 AF 37 E6 3B B1 CB F2 70 E0 8D [ &F,u7;p]
19:46:57: RADIUS: Vendor, Cisco [26] 72
19:46:57: RADIUS: Cisco AVpair [1] 66 "ACS:CiscoSecure-Defined-ACL=#ACSACL#-IP-Contractors-ACL-4fbcd736"
19:46:57: RADIUS: Vendor, Cisco [26] 42
19:46:57: RADIUS: Cisco AVpair [1] 36 "profile-name=Microsoft-Workstation"
19:46:57: RADIUS(00000026): Received from id 1645/25
19:46:57: RADIUS/DECODE: parse unknown cisco vsa "profile-name" - IGNORE
May 24 07:03:19.132: %MAB-5-SUCCESS: Authentication successful for client (0016.d329.042f) on Interface Gi1/0/7 AuditSessionID 0A01280100000016043E0D23
May 24 07:03:19.132: %AUTHMGR-7-RESULT: Authentication result 'success' from 'mab' for client (0016.d329.042f) on Interface Gi1/0/7 AuditSessionID 0A01280100000016043E0D23
May 24 07:03:19.140: %EPM-6-POLICY_REQ: IP 10.1.100.194| MAC 0016.d329.042f| AuditSessionID 0A01280100000016043E0D23| AUTHTYPE DOT1X| EVENT APPLY
May 24 07:03:19.165: %EPM-6-AAA: POLICY xACSACLx-IP-Contractors-ACL-4fbcd736| EVENT DOWNLOAD-REQUEST
19:46:57: RADIUS/ENCODE(00000000):Orig. component type = Invalid
19:46:57: RADIUS(00000000): Config NAS IP: 0.0.0.0
19:46:57: RADIUS(00000000): sending
19:46:57: RADIUS/ENCODE: Best Local IP-Address 10.1.100.1 for Radius-Server 10.1.100.6
19:46:57: RADIUS(00000000): Send Access-Request to 10.1.100.6:1812 id 1645/26, len 144
19:46:57: RADIUS: authenticator 1A 52 18 C5 25 A7 5C DC - 29 C9 5C 7C C5 B3 FC 58
19:46:57: RADIUS: NAS-IP-Address [4] 6 10.1.100.1
19:46:57: RADIUS: User-Name [1] 38 "#ACSACL#-IP-Contractors-ACL-4fbcd736"
19:46:57: RADIUS: Vendor, Cisco [26] 32
19:46:57: RADIUS: Cisco AVpair [1] 26 "aaa:service=ip_admission"
19:46:57: RADIUS: Vendor, Cisco [26] 30
19:46:57: RADIUS: Cisco AVpair [1] 24 "aaa:event=acl-download"
19:46:57: RADIUS: Message-Authenticato[80] 18
19:46:57: RADIUS: 2B 6B 13 37 0D 25 11 E9 6A 56 35 D8 91 9F EF F0 [ +k7?jV5]
19:46:57: RADIUS(00000000): Sending a IPv4 Radius Packet
19:46:57: RADIUS(00000000): Started 5 sec timeout
May 24 07:03:19.191: %SEC-6-IPACCESSLOGP: list ACL-DEFAULT denied tcp 10.1.100.194(2125) -> 10.1.100.6(8443), 1 packet
19:46:57: RADIUS: Received from id 1645/26 10.1.100.6:1812, Access-Accept, len 359
19:46:57: RADIUS: authenticator 31 B0 73 93 CA 0E 5C 7C - 11 29 AA 57 6C A1 53 D8
19:46:57: RADIUS: User-Name [1] 38 "#ACSACL#-IP-Contractors-ACL-4fbcd736"
19:46:57: RADIUS: State [24] 40
19:46:57: RADIUS: 52 65 61 75 74 68 53 65 73 73 69 6F 6E 3A 30 61 [ReauthSession:0a]
19:46:57: RADIUS: 30 31 36 34 30 36 30 30 30 30 30 30 35 44 34 46 [0164060000005D4F]
19:46:57: RADIUS: 42 44 44 44 33 37 [ BDDD37]
19:46:57: RADIUS: Class [25] 49
19:46:57: RADIUS: 43 41 43 53 3A 30 61 30 31 36 34 30 36 30 30 30 [CACS:0a016406000]
19:46:57: RADIUS: 30 30 30 35 44 34 46 42 44 44 44 33 37 3A 69 73 [0005D4FBDDD37:is]
19:46:57: RADIUS: 65 2F 31 32 34 30 33 36 37 39 31 2F 32 39 38 [ e/124036791/298]
19:46:57: RADIUS: Termination-Action [29] 6 1
19:46:57: RADIUS: Message-Authenticato[80] 18
19:46:57: RADIUS: 80 EF 5B 80 76 F1 C9 37 0B 25 34 37 10 57 CC 44 [ [v7?47WD]
19:46:57: RADIUS: Vendor, Cisco [26] 47
19:46:57: RADIUS: Cisco AVpair [1] 41 "ip:inacl#1=permit udp any any eq domain"
19:46:57: RADIUS: Vendor, Cisco
SW3750-1# [26] 48
19:46:57: RADIUS: Cisco AVpair [1] 42 "ip:inacl#2=permit ip any host 10.1.100.6"
19:46:57: RADIUS: Vendor, Cisco [26] 57
19:46:57: RADIUS: Cisco AVpair [1] 51 "ip:inacl#3=deny ip any 10.0.0.0 0.255.255.255 log"
19:46:57: RADIUS: Vendor, Cisco [26] 36
19:46:57: RADIUS: Cisco AVpair [1] 30 "ip:inacl#4=permit ip any any"
19:46:57: RADIUS(00000000): Received from id 1645/26
May 24 07:03:19.216: %EPM-6-AAA: POLICY xACSACLx-IP-Contractors-AC
SW3750-1#
SW3750-1#
SW3750-1#L-4fbcd736| EVENT DOWNLOAD-SUCCESS
May 24 07:03:19.216: %EPM-6-POLICY_APP_SUCCESS: IP 10.1.100.194| MAC 0016.d329.042f| AuditSessionID 0A01280100000016043E0D23| AUTHTYPE DOT1X| POLICY_TYPE Named ACL| POLICY_NAME xACSACLx-IP-Contractors-ACL-4fbcd736| RESULT SUCCESS
May 24 07:03:20.147: %AUTHMGR-5-SUCCESS: Authorization succeeded for client (0016.d329.042f) on Interface Gi1/0/7 AuditSessionID 0A01280100000016043E0D23
19:46:58: RADIUS/ENCODE(00000026):Orig. component type = Dot1X
19:46:58: RADIUS(00000026
SW3750-1#
SW3750-1#
SW3750-1#
SW3750-1#): Config NAS IP: 0.0.0.0
19:46:58: RADIUS(00000026): Config NAS IPv6: ::
19:46:58: RADIUS/ENCODE: Best Local IP-Address 10.1.100.1 for Radius-Server 10.1.100.6
19:46:58: RADIUS(00000026): Sending a IPv4 Radius Packet
19:46:58: RADIUS(00000026): Started 5 sec timeout
19:46:58: RADIUS: Received from id 1646/35 10.1.100.6:1813, Accounting-response, len 38
SW3750-1#
SW3750-1#sh authe sess int g 1/0/7Interface: GigabitEthernet1/0/7
MAC Address: 0016.d329.042f
IP Address: 10.1.100.194
User-Name: xxxxx@gmail.com
Status: Authz Success
Domain: DATA
Security Policy: Should Secure
Security Status: Unsecure
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
Vlan Group: N/A
ACS ACL: xACSACLx-IP-Contractors-ACL-4fbcd736
Session timeout: N/A
Idle timeout: N/A
Common Session ID: 0A01280100000016043E0D23
Acct Session ID: 0x0000001B
Handle: 0x2F000017
Runnable methods list:
Method State
mab Authc Success
dot1x Not run
SW3750-1#
Has anyone encountered similar thing?
I tried 12.2(58) and now Im testing
Cisco IOS Software, C3750 Software (C3750-IPSERVICESK9-M), Version 15.0(1)SE2, RELEASE SOFTWARE (fc3)
but in both cases it is similar.
regards
Przemek
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2012 08:01 AM
Hi,
Have you tried IOS 12.2.55SE3 which is recommended (tested) according to TrustSec 2.0 Design and Implementation Guide?
What's your port configuration? Have you included the "reauth" commands?
int gX/Y
...
authentication periodic
authentication timer reauthenticate server
Cheers,
Seba
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2012 08:01 AM
Hi,
Have you tried IOS 12.2.55SE3 which is recommended (tested) according to TrustSec 2.0 Design and Implementation Guide?
What's your port configuration? Have you included the "reauth" commands?
int gX/Y
...
authentication periodic
authentication timer reauthenticate server
Cheers,
Seba
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2012 11:44 PM
Hi Sebastian,
thx a lot those 2 commands solved the issue, my mistake. Now I can see remaining time for the session
SW3750-1#sh auth sess int g1/0/7
Interface: GigabitEthernet1/0/7
MAC Address: 0016.d329.042f
IP Address: 10.1.100.194
User-Name: jan@gmail.com
Status: Authz Success
Domain: DATA
Security Policy: Should Secure
Security Status: Unsecure
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
Vlan Group: N/A
ACS ACL: xACSACLx-IP-Contractors-ACL-4fbcd736
Session timeout: 28800s (server), Remaining: 28780s
Timeout action: Terminate
Idle timeout: N/A
Common Session ID: 0A012801000000221DE0F555
Acct Session ID: 0x0000002B
Handle: 0x99000023
Runnable methods list:
Method State
mab Authc Success
dot1x Not run
regards
Przemek
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide