- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 1.2 Authentication issue-Always to ACCESS_REJECT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 1.2 Authentication issue-Always to ACCESS_REJECT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2016 08:17 PM - edited 03-10-2019 11:54 PM
Hello Everyone,
I am doing new solution with ASA-SSL VPN login Authentication by ISE(external identify source is WIN2008 R2 AD)
The topology is that please see the topology map, it is a sample.

Device IP info:
ASA inside IP 10.254.254.1
outside IP x.1.1.1 (just a sample)
ISE 1.2 ip 10.254.254.249
ISE 1.4 ip 10.254.254.248
Software info
Asa version: Cisco Adaptive Security Appliance Software Version 9.2(3)4
Ise-1.2 VM Version : 1.2.1.198
ISE-1.4 1.4.0.253
About route of inside LAN
Two way ping test between ASA ISE DC all are passed, it is working well
The Problem is:
VPN user FAILED login to ASA VPN server x.1.1.1 ,at ISE 1.2 I can saw that the user passed the AD Authentication, but ise Selected Authorization Profile - DenyAccess :
|
24432 |
Looking up user in Active Directory - bytter1 |
|
|
|
24416 |
User's Groups retrieval from Active Directory succeeded |
|
|
24420 |
User's Attributes retrieval from Active Directory succeeded |
|
|
15004 |
Matched rule - Default |
|
|
15016 |
Selected Authorization Profile - DenyAccess |
And the solution at ISE is ask to change access type from ACCESS_REJECT to ACCESS_ACCEPT
|
Event |
5434 Endpoint conducted several failed authentications of the same scenario |
|
Failure Reason |
15039 Rejected per authorization profile |
|
Resolution |
Authorization Profile with ACCESS_REJECT attribute was selected as a result of the matching authorization rule. Check the appropriate Authorization policy rule-results. |
Actually at the setting at ISE user Authorization Profile, the ACCESS_TYPE was ACCESS_ACCEPT, So I do not need to do that change.

btw the at policySet setting,the Permissions is selected correct user Authorization Profile. also do not need change.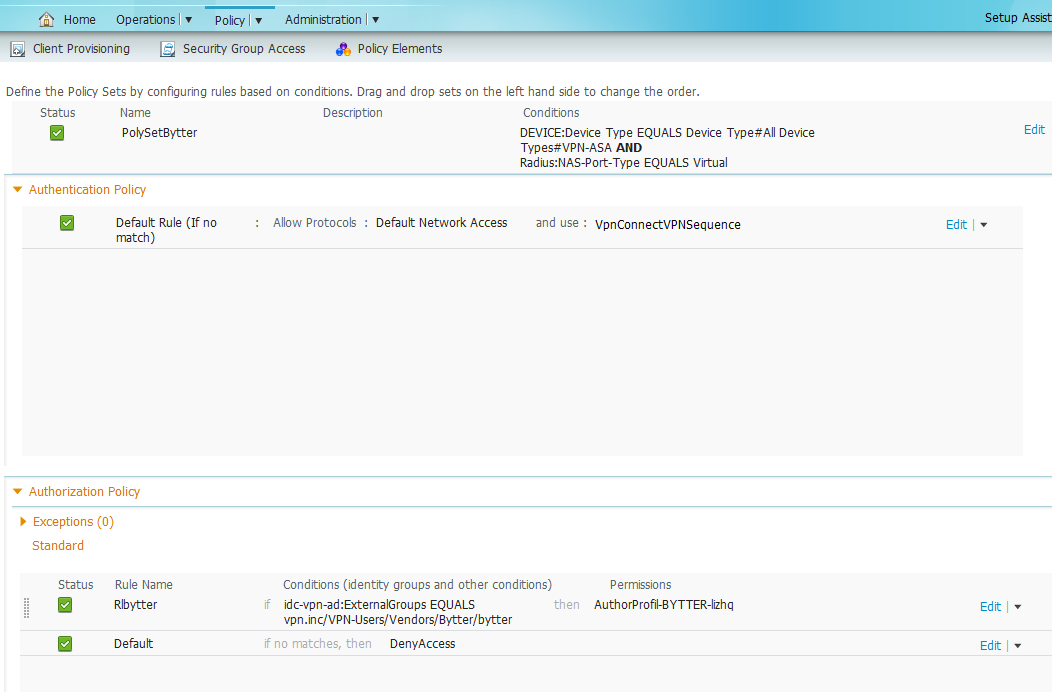
So would you please help me to solve this problem? Is it a ISE bug?
Why this issue happened at ISE 1.4.0.253 which I implemented too?
Thanks.
Regards,
by Steven
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2016 08:35 PM
client failed authentication due to “Suppress Anomalous Clients"
Failed Auth Logs:
5434 Endpoint conducted several failed authentications of the same scenario
From more detail please read this:
https://supportforums.cisco.com/discussion/11995281/ise-12-anomalous-client-suppression
This is a new feature introduced on ISE 1.2 and enabled by default. You can disable this on (Admin->System->Settings->Protocols->RADIUS)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2016 02:28 AM
Thank You Sir
after I disabled two options:
1 Suppress Anomalous Client
2 Suppress Repeated Successful Authentications
it is still not working now.
So please guide me more. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2016 10:17 AM
After I did some test, I find that the problem is belong to AD user group , Global security Group.
the User A with Group A, it is working and vpn can log on. and User b and Group b is not working.
but if I move User b TO group A, then User b can login.
if i move user A to User B, then User a can not login.
So i Believe that the problem is with AD.
Microsoft Windows [Version 6.1.7601], this is my windows server version- windows 2008 r2 enterprise with Service Pack 1.
and Now I am trying windows update now, It showed I need install 159 patches, So please check why this kind of issue happened?
is there any compatibility issue with ISE 1.2 and win2008 r2 with sp1?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 10:30 PM
just setup a WindowsServer2012 R2 (Microsoft Windows 6.3.9600])which installed all newest Security Patches,user the AD user to Login vpn, then ISE(Cisco Identity Services Engine Version : 1.4.0.253) still tell me:
Cisco Identity Services Engine
|
|||||||||||
but the AccessType-setting of every Authorization Profiles is ACCESS_ACCEPT
Could you please tell me how to solve it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2016 03:53 AM
Problem soloved
the problem is:
I created so many line of PolicySet(each one is with a Authorization policy just for one AD group), but every User login only goto top first PolicySet. for example, fisrt policy set is PolicySetGroupA, then UserA can pass the Rule(RuleUserA(AD externalGroups equals GroupA), but UserB is belong to GroupB,and next policy set is for GroupB.
after I just use one PolicySet (named vpnPolicySet)to contain every Authorization policy for Each user Group (RuleHinge RuleIWS) , then it is working.
| Event | 5200 Authentication succeeded |
| Username | hinge1 |
| Endpoint Id | 114.255.17.134 |
| Endpoint Profile | |
| Authorization Profile | AP-Hinge |
| AuthorizationPolicyMatchedRule | RuleHinge |
| ISEPolicySetName | vpnPolicySet |
| IdentitySelectionMatchedRule | Default |
| Event | 5200 Authentication succeeded |
| Username | iws1 |
| Endpoint Id | 114.255.17.134 |
| Endpoint Profile | |
| Authorization Profile | AP-IWS |
| AuthorizationPolicyMatchedRule | RuleIWS |
| ISEPolicySetName | vpnPolicySet |
| IdentitySelectionMatchedRule | Default |
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide