- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 1.2 EAP-TLS and AD authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 1.2 EAP-TLS and AD authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2014 06:43 AM - edited 03-10-2019 09:30 PM
Hi,
I am sure I have had this working but Just cant get it to now.
So I have a Computer that has a Certificate on it with the SAN - princible name = to 12345@mydomain.com. This is an auo enroled Cert from my AD.
My Authentication profile says
IF the SSID (called-station) contianes eduroam and Princible name containes @mydomain.com then user a certification authentication profile. (see attachemnt below)
Then my authorization profile says
if active directoy group = "Domian computers" then allow access.
When my computer trys to join it passes the certificate test, but when it gets to the AD group is get the below.
24433 Looking up machine in Active Directory - FY8FCT1$@mydomain.ac.uk
24492 Machine authentication against Active Directory has failed
22059 The advanced option that is configured for process failure is used
22062 The 'Drop' advanced option is configured in case of a failed authentication request
But I know my machine is in AD? What do i need to do to get the PC to use EAP-TLS to authenicate and AD group to authorize?
Cheers
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2014 07:02 AM
On Admin->Identity Management->External Identity Sources->Active Directory->Advanced Settings tab do you have enable machine authentications checkbox selected?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2014 07:05 AM
Hi,
yep looks like it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2014 07:06 AM
Can you post a screenshot of your relevant Authentication and Authorization policy settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2014 07:18 AM

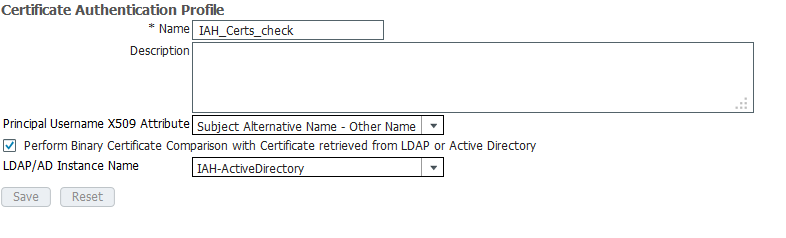
This accepts all requsts to one SSID and then as you can see if it is EAP TLS uses Cert store (see below), other wise AH
![]()
This jsut says if AD Group = /user/domainComputer allow full access (simple rule)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2014 07:44 AM
Perhaps try using the "common name" subject attribute not the "other name" subject attribute. In the past, I've used common name for my deployments and it had worked. I also configure it a little differently by configuring an identity source sequence for AD then local with the certificate profile selected. Not saying my way is the right way, just saying how I had achieved success in the past.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2014 07:56 AM
Trouble is i need the machine to use the "princible name" for authentication. My username must be in the formate
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

