- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 1x authentication please helpme!!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2019 07:32 AM - edited 06-20-2019 07:33 AM
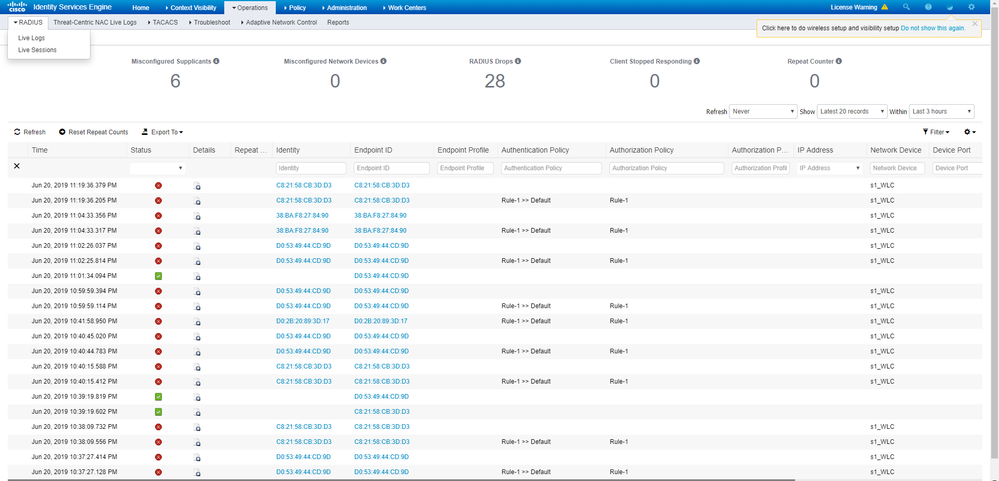
We are in the process of certification testing with ISE 3566 2.6 equipment.
But the above fails.
The detail information of the log is shown below.
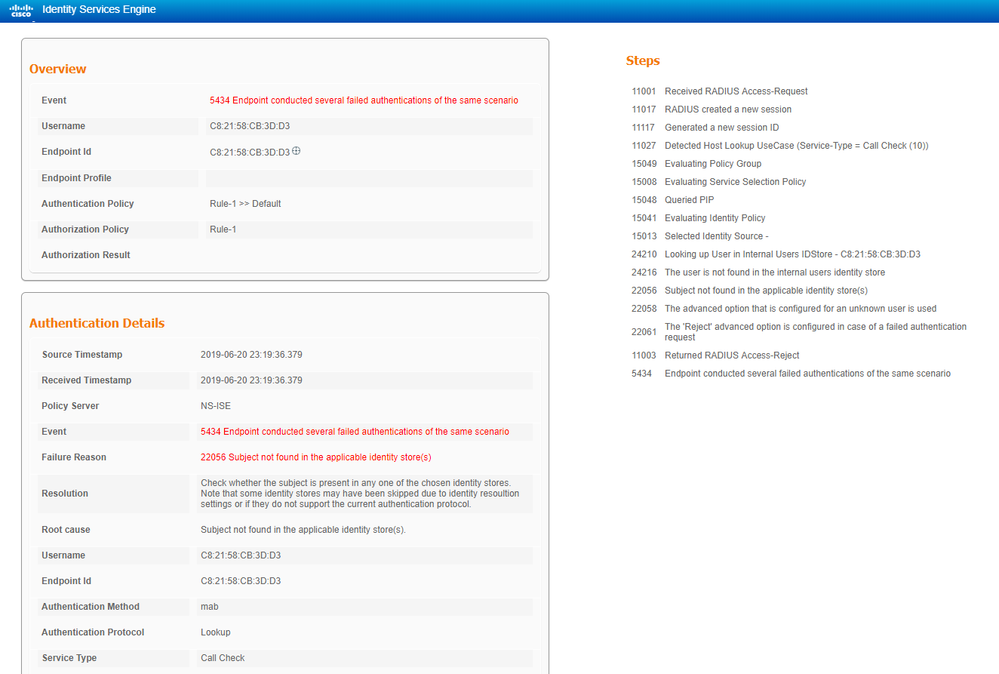
5434 Endpoint conducted several failed authentications of the same scenario
When I search Google, it seems to be recognized as a DDOS attack.
https://community.cisco.com/t5/policy-and-access/ise-and-failed-authentications-conducted-by-endpoints/td-p/2971530
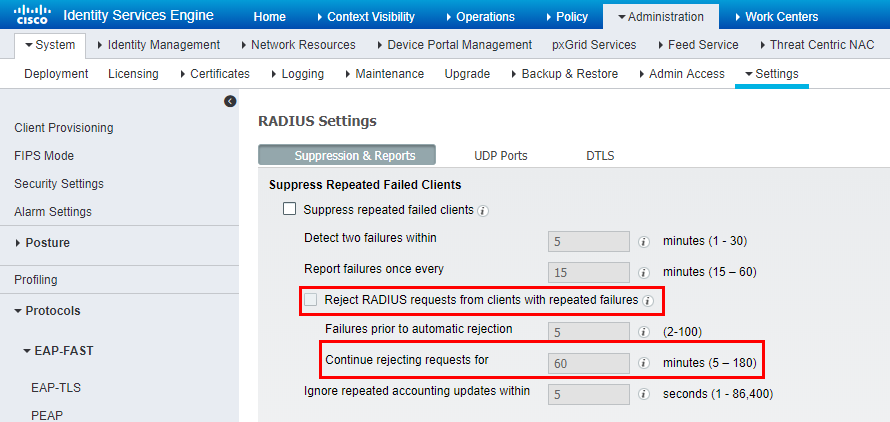
I tried to use the method mentioned in the link above, but I do not see the "Radius, Suppress Anomalous Clients" menu.
I think it's probably the version difference.
How do I resolve this issue in version 2.6?
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 05:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2019 11:53 PM
Thank you for answer.
I solved this problem.
The cause of the problem was Reject-RADIUS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2019 01:31 PM
What is the origin of those WLC authentications? Is it for an OPEN SSID, or iPSK? Or, are you using Radius on the WLC to perform device management, and have you got that working on the WLC? I have seen a bug with TACACS auth on WLC, that floods the ISE PSN with hundreds of requests after you login to WLC using TACACS. But I have not checked if that is the case when Radius is used as a device management protocol. Just a stab in the dark ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2019 09:35 PM - edited 07-06-2019 08:48 PM
See the session presentation slide 306 of Advanced ISE – Architect, Design and Scale ISE for your production networks - BRKSEC-3432.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2019 05:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2019 11:53 PM
Thank you for answer.
I solved this problem.
The cause of the problem was Reject-RADIUS.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide