- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.0+ EAP-FASTv2 & OSX High Sierra Incompatible?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2018 10:19 AM
I'm using this as a last-ditch effort to understand what may be happening with this issue, as I have already reached out to TAC at least twice to follow-up on this while watching bug notifications and anything I can find on the web (which isn't much).
I have been running EAP-FASTv2 with our fleet of OSX devices for about 2 years now, however upon upgrading a test machine to High Sierra, EAP-FASTv2 authentications are broken, making the protocol unusable. I have watched two Cisco bug IDs go from Open to Fixed and yet haven't seen a fix applied in a patch for ISE. When I reach out to TAC, they say that the tickets say "waiting for Apple developers", yet no information regarding this is in the bug notifications and they have no ETA.
Considering High Sierra has been released for over 3 months now and that Cisco and Apple announced publicly they were in partnership to work on making their tech agree with each other last June, what happened here? Three months of this protocol being completely broken and no real feedback or communication from either side on who will fix and when is absolutely unacceptable taking into consideration the partnership between companies and that both of these tickets are marked as Closed/Fixed.
Any insight is greatly appreciated.
Here are the most recent bug IDs for this issue:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvg73639
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvf96030
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2018 04:13 PM
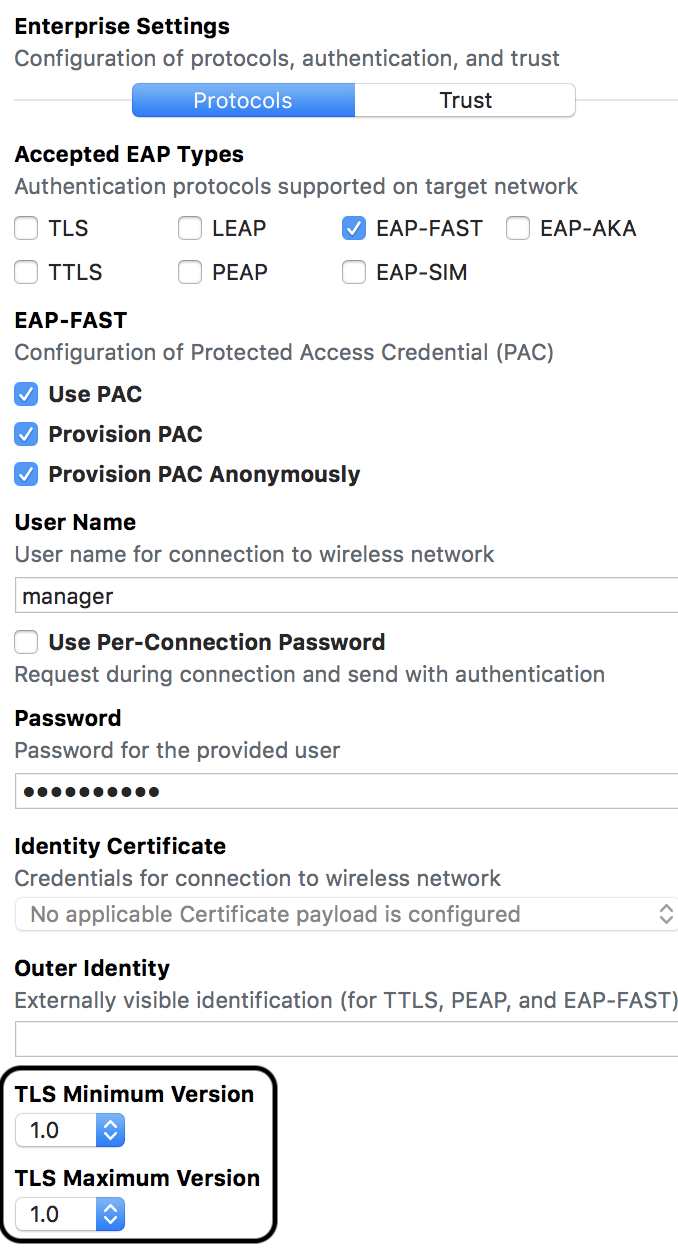
Attached is a profile I created using Apple Configurator 2 and tested ok with the dCloud lab Cisco ISE Mobility Deep Dive. It seems the key is to use 1.0 as the TLS Max Version.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2018 08:03 AM
CSCvg73639 is a doc bug.
CSCvf96030 is addressed and verified in ISE 2.3 Patch 1. It seems a change in SPW.
Which ISE release is your deployment on? I will check with our team and see whether we may validate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2018 10:23 AM
I am running ISE 2.3 without any patches at the moment. It appears that sometimes the upgraded (10.13) laptops will respond with the prompt saying that "this wifi network could not be joined" and when that happens I don't even see a failed authentication attempt in ISE. I will be able to get more test data on Monday.
Thanks for looking into this issue - the help is greatly appreciated with how frustrating this has been ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2018 10:36 AM
Alright! Finally was able to get more information on this issue - My OSX 10.13 (High Sierra) test machine reaches ISE when attempting to authenticate and gets the following errors in the authentication report:
| Event | 5411 Supplicant stopped responding to ISE |
| Failure Reason | 12118 EAP-FAST cryptobinding verification failed |
| Resolution | Verify that the client's supplicant is properly configured. |
| Root cause | EAP-FAST cryptobinding verification failed. |
Our 10.12 (Sierra) laptops have been fine. Any insight into if this corresponds with an open bug ID or anything I can test to get more information for this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2018 12:08 PM
What is the SPW version you used? Our engineering team said the fix in the latest SPW for macOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2018 10:34 AM
I have not had to use SPW ( I believe this is used to configure dot1x profiles for devices? ) - our laptops would just connect with 10.12 to the network without further configuration. Is that something I should check out? I didn't see the download for OS X under the ISE images page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2018 07:22 PM
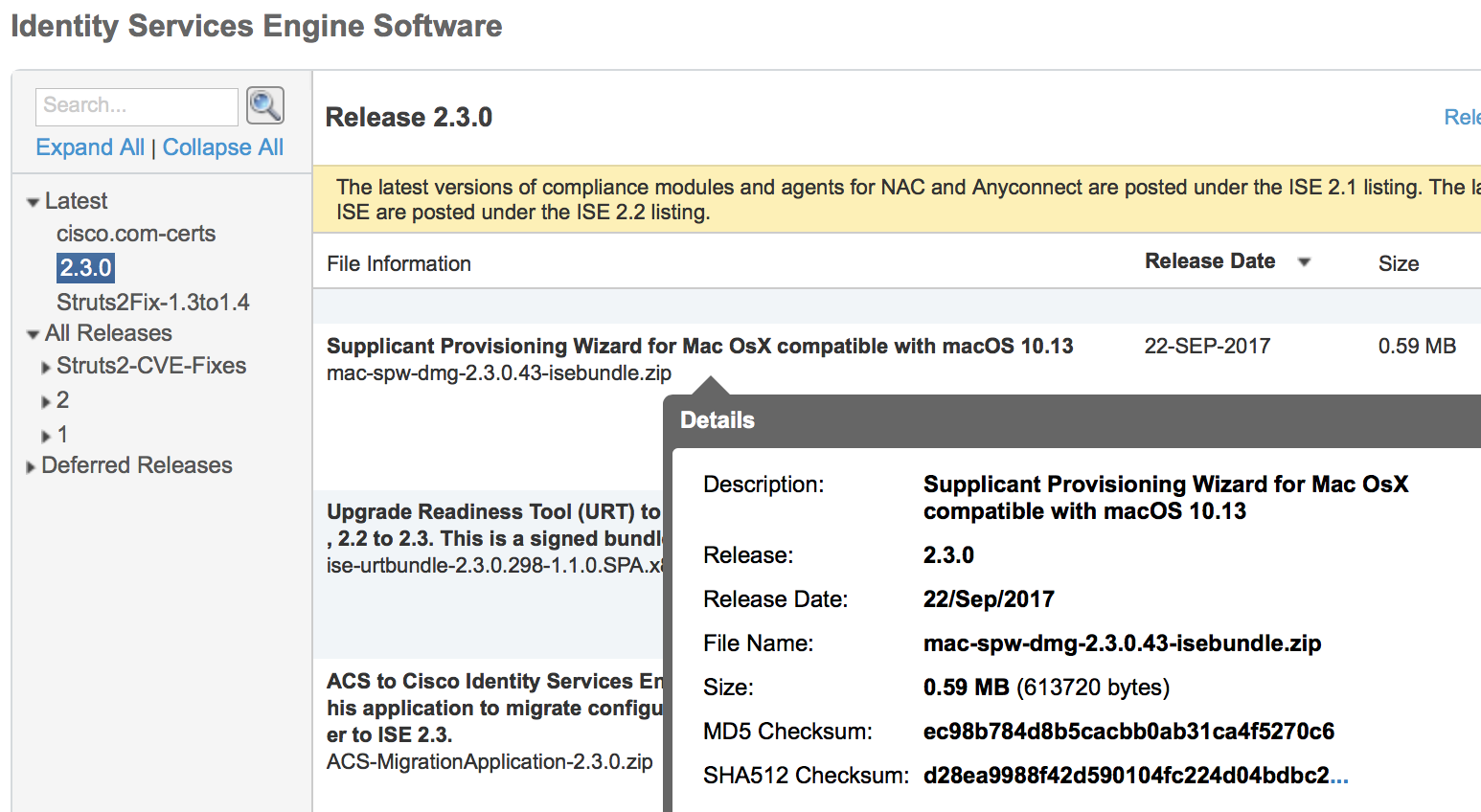
Please download mac-spw-dmg-2.3.0.43-isebundle.zip under ISE 2.3.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2018 11:15 AM
Thanks for that! I found the installer and downloaded it - however I was unable to find documentation for it. Will this help me create a dot1x profile that I can then deploy to other machines? At the moment, SPW starts up and proclaims it cannot find ISE, so any information to troubleshoot myself would be very much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2018 12:10 PM
This SPW is for ISE BYOD.
Please take a look of the following:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2018 04:13 PM
Attached is a profile I created using Apple Configurator 2 and tested ok with the dCloud lab Cisco ISE Mobility Deep Dive. It seems the key is to use 1.0 as the TLS Max Version.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2018 10:24 AM
After some discussions, it turns out SPW for macOS version 2.3.0.43 was a temporary solution and we are planning to post 2.2.1.43, which has full support for macOS 10.13.x.
If you do not use ISE BYOD for macOS, please do try the info I posted in with Apple Configurator 2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 02:26 PM
Well, I'll be. Had some time to test this today and after trying pretty much everything, once we set TLS to 1.0, the OSX 10.13. laptops were able to connect without issue. Yay! Final question then is, is this is a missing TLS1.2 cipher issue and if so, is this on ISE or OSX? ![]()
Anyhow, thanks so much for digging into this hslai, you have been amazing at uncovering the answers to the questions I've had and are the true expert of this forum.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 02:37 PM
The issue is that there are ciphers in the EAP-FAST RFC that Apple has disabled.
For EAP-FAST to work the ciphers below need to be enabled for authenticated/anonymous PAC provisioning.
TLS_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
For authenticated PAC provisioning
TLS_DH_anon_WITH_AES_128_CBC_SHA
For Anonymous PAC Provisioning
Apparently, macOS 10.13.x allows these ciphers with TLS 1.0.
You are welcome and thanks a lot for your nice words.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide