- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.2 pxGrid - issue with CSR signing by CA server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 2.2 pxGrid - issue with CSR signing by CA server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 08:19 PM
Hi Team,
Not sure what the best alias is for this since its more related to Microsoft CA server than ISE or Stealthwatch but maybe someone from the team can help me out here…
I’m at my customer site trying to get the ISE v2.2 integration with Stealthwatch working. The customer has an internal CA server and we followed the attached guide (see page 10 onwards) for the CA pxGrid certificate template config. This worked perfectly in my lab, however at the customer site we are getting an error when we try to sign the ISE node’s Certificate Signing request for pxGrid usage based on that CA server pxGrid certificate template.
The error we are getting is:
Certificate Request Denied
Your certificate request was denied.
Your Request Id is 53. The disposition message is "Error Constructing or Publishing Certificate Invalid Issuance Policies: 2.5.29.32.0".
Contact your administrator for further information.
We did some search on google as to what the potential issue could be but can’t work out whats wrong with the template.
Anyone got some suggestions?
Thanks in advance
Thomas
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 08:22 PM
Here is the link to the ISE with Stealthwatch Integration that we used as a guide for the CA Server template config:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 08:35 PM
It seems like Microsoft CA is used and we've seen problems with "all insurance policy" in the cert template before. I would suggest you to try Garjendran's reply on 2013-Sept-03 to ISE On-Boarding process - Cisco Support Community
Best to consult Microsoft. An old note I had showed it possible to disable the check at the CA side:
Run the following command at the CA and restart the CA service
certutil –setreg CA\CRLFlags +CRLF_IGNORE_INVALID_POLICIES
net stop certsvc
net start certsvc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 08:43 PM
Thank you so much for your prompt reply Hsing-Tsu! I did read that post earlier, however it doesn't really explain what the solution is or how to fix this on the CA server. "This error may be because the byod template is configured with the "all insurance policy" (OID = 2.5.29.32.0) and the CA server is unable to publish the certs using this template due to its policy restrictions. This should be workable once we enable all insurancy policy in the CA server. Looking at how to do this in the CA."
"This should be workable once we enable all insurancy policy in the CA server" - Not sure what that ultimately means in terms of template or CA policy config.
I also found this note below with various ways of addressing this.
Issuance Policies with a CA Upgrade to Windows 2008 R2 AD CS PKI | SilkSpun
I guess what you outlined earlier is noted as option one in the link below. Not sure though if this is a good thing since it seems to kind of override the behaviour and checks within the CA. So I am basically wondering if there is an issue with the pxGrid certificate template we configured in the CA or if there are some other knobs we need to tweak in the CA somewhere to make this work. Problem is who can we ask since this is more like a MS CA server specific question.
Thanks
Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 08:59 PM
What I meant is most of the certificate templates need no insurance policy; that is, we may leave it empty.
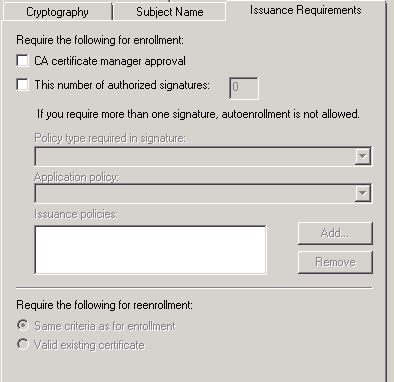
If one specified, then the CA needs to adhere to it and could cause problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 09:07 PM
Oh ok, no worries. Let me try that. So I basically ignore whats shown in the Stealthwatch/ISE integration guide?
Cheers
Thomas
Thomas Lenzenhofer
Network Security Consulting Engineer
Advanced Services / Security IDT
Cisco Systems APJC/Australia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 09:13 PM
I am guessing John copied that from our "old" BYOD guide. It works fine if MS CA is by itself and customers reported problems when using a multi-tier MS CA. I would suggest you to send John a note.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2017 09:19 PM
Cool that makes sense thanks! It worked fine in my lab on a standalone CA as you said, whereas the customer here has a 2-tier setup…
Thanks for your help!
Thomas
Thomas Lenzenhofer
Network Security Consulting Engineer
Advanced Services / Security IDT
Cisco Systems APJC/Australia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2017 06:21 PM
Hi again,
Just as FYI – the screenshot you referred to yesterday – we had already had that setting earlier (empty list) and that itself didn’t work. We had to remove the ‘All Issuance Policies’ from the list under the ‘Extensions’ tab and then it worked right away.
Thanks again for pointing me into the right direction.
Regards
Thomas
Thomas Lenzenhofer
Network Security Consulting Engineer
Advanced Services / Security IDT
Cisco Systems APJC/Australia
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide